Over 2022, Kaspersky detected and blocked 221,695 cyberattacks on Internet of Things (IoT) devices in South Africa. In Kenya, the figure is 45,562 and for Nigeria, 30,089. All these attacks were blocked on Kaspersky honeypots – decoy devices used to attract the attention of cybercriminals and analyse their activities.
IoT devices include wearables, smart home appliances, smart city systems, self-driving cars, automated retail checkouts, and other smart devices for home and business use. These devices can collect and transfer data over a wireless network without human input. Cybercriminals use networks of infected smart devices to conduct DDoS attacks or as a proxy for other types of malicious actions.
The number of attacks on IoT devices has been increasing exponentially over the last years. This is related both to the activity of criminal actors and to the increasing number of IoT devices that are in use. According to open research, in 2020 there were 42,4 million IoT devices operating in Sub-Saharan Africa. By 2030, the number is expected to triple and reach 264 million¹. Capitalising on weak security of IoT devices, cybercriminals are intensifying their attacks.
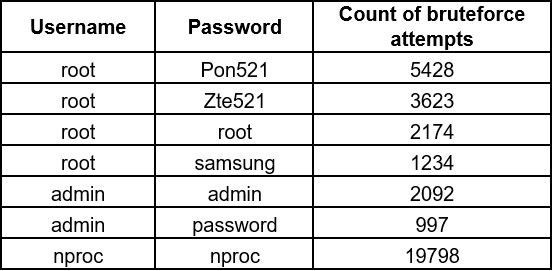
A brute force attack uses trial-and-error to guess login and password info or encryption keys, with hackers working through all possible combinations to guess correctly. In the African region throughout 2022 there were over 93,000 attempts to brute force logins and passwords to IoT devices using only the most popular combinations (examples are provided in the table below); the total number of brute force attempts is even higher.
Examples of the most popular brute force login combinations for IoT devices in the African region:
“As the number of IoT devices grows and attacks intensify, cybercriminals use both advanced and simple tactics to infiltrate smart devices. One of these tactics is using simple password and login combinations – our research showed that on hundreds of thousands of IoT devices the most common login-password combinations are admin-admin, guest-guest, or other variants that come as default on different kinds of equipment,” commented Vladimir Dashchenko, security expert at Kaspersky ICS CERT². “It is easy to change the default password, so we urge everyone to take this simple step towards securing your smart devices. Speaking of more thorough protection, IoT vendors should consider implementing the next generation cybersecurity approach in their products – where devices would feature innate, built-in protection that would make them Cyber Immune. Such technology is already available on the market, including offers from Kaspersky. For instance, Kaspersky IoT Secure Gateway system is designed to serve as a secure gateway for the Internet of Things on an enterprise network.”
Given the diversity of IoT devices and their related cybersecurity risks, the need for their protection is clear, especially when it comes to smart cities or critical infrastructure. Traditional measures are not sufficient for IoT protection, making it crucial that specialised security solutions are implemented.
To keep your devices safe, Kaspersky recommends users:
• Install updates for the firmware you use as soon as possible. Once a vulnerability is found, it can be fixed through patches within updates.
• Periodic rebooting will help get rid of malware already installed (although in most cases the risk of reinfection will remain).
• Change the factory passwords at initial setup, use complex passwords at least 8 characters long, including upper and lower-case letters, numerals, and special characters.
• Use a strict access policy, network segmentation and a zero-trust model. This will help minimise the spread of an attack and protect the most sensitive parts of the infrastructure.
• Check the IoT Security Maturity Model – an approach that helps companies evaluate all steps and levels they need to pass to achieve a sufficient level of IoT protection.
• Use a dedicated IoT gateway that ensures the inbuilt security and reliability of data transferring. For instance, Use Kaspersky Threat Intelligence to block network connections originating from malicious network addresses detected by security researchers.
References:
¹ https://www.statista.com/statistics/1183457/iot-connected-devices-worldwide/
² Kaspersky Industrial Control Systems Cyber Emergency Response Team




