Anti Targeted Attack Platform
How do businesses protect against APTs?
So called Advanced Persistent Threats are sophisticated, targeted, long-term and usually extremely well-prepared attack campaigns, professionally designed to bypass single-layer protection.
The main purpose of an Anti-APT/Anti-targeted attack solution is to raise the cost of mounting an attack to the point where such an exercise is no longer practicable or economically viable. These solutions rely on the application of multiple techniques: the more different layers of detection that can be implemented and the more potential attack entry-points supervised, the higher the probability of an attack being uncovered, no matter how much time and money the attacker is prepared to throw at it.
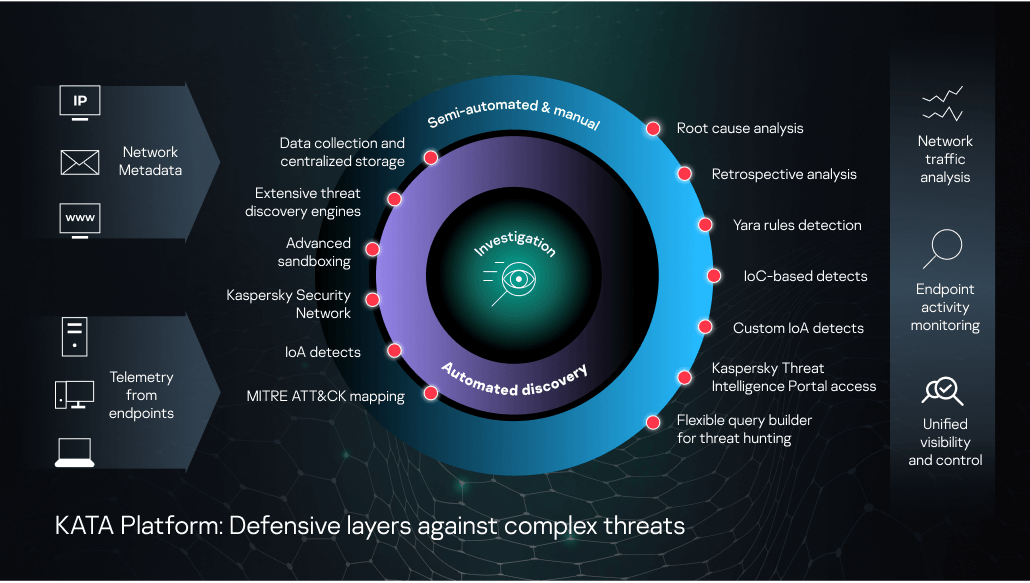
The KATA Platform, combining Kaspersky Anti Targeted Attack with Kaspersky EDR, is an example of this sort of enterprise solution. Its advanced technology layers include:
Network traffic analysis. This module features behavior detection capabilities and analyzes traffic and objects using IDS technology and URL reputations:
- Intrusion Detection technology combines both traditional and advanced threat detection, powered by a unique set of IDS rules for traffic analysis, oriented towards targeted attacks. IDS rule-sets are automatically and promptly updated.
- URL reputation analysis. Suspicious or undesirable URLs are detected based on reputation data from the cloud-based global Kaspersky Security Network (KSN), which also includes information about URLs and domains connected to targeted attacks.
Sandbox. The sandbox runs suspicious objects on its own virtual machines, to detect malicious activity. The sandbox receives sample execution tasks which include virtualization parameters based on the source of the evaluated object and the purpose of the evaluation (e.g. type of OS(s), OS configuration, environment, parameters of sample start, execution duration).
During sample execution, the sandbox collects:
- logs of the sample’s behavior (including list of system functions calls, iteration with another processes and files, network activities, URLs etc)
- dumps
- dropped objects
- traffic generated by the sample
Once execution is complete, the artefacts acquired are stored, then processed by a dedicated scanner. If the sample has been found to be malicious, a verdict will be attributed, and the results mapped to the MITRE ATT&CK knowledgebase. All the collected data is stored internally to enable further analysis of the adversary’s tactics and techniques without the need for additional sandbox requests, saving on server resources.
A comprehensive set of features, including OS environment randomization, time acceleration in virtual machines, anti-evasion techniques, user activity simulation, etc, all contribute to highly efficient behavior-based detection. The sandbox uses a number of patented technologies and can be operated in both automated and manual modes.
Kaspersky Security Network (KSN) is a global cloud infrastructure holding reputation verdicts and other information about objects processed by the KATA Platform (files, domains, URLs, IP addresses and more). KSN also provides detection using cloud ML models, such as Cloud ML for Android: local APK file metadata is collected by the Platform and sent to KSN, which replies with a verdict created by the ML-based model. A private cloud based solution Kaspersky Private Security Network (KPSN) is available for organizations unable to send their data to the global KSN cloud but still wishing to benefit from Kaspersky’s global reputation database. In addition to private access to our global threat intelligence database, verdicts from the KATA Platform are stored on a local KPSN database and automatically shared with other Kaspersky products deployed within the organizational infrastructure for automated response. Organizations with KPSN deployed can benefit from reputations provided by external 3rd party systems with no intermediate steps, via an API.
Targeted Attack Analyzer (TAA) can discover suspicious actions based on enhanced anomaly heuristics, provisioning real-time automated threat hunting capabilities. It supports the automatic analysis of events, and their correlation with a unique set of Indicators of Attack (IoAs) generated by Kaspersky’s Threat Hunters. Each time a significant anomaly is detected by the TAA, the IT-security specialist receives a written description, recommendations (such as how to reduce the risk of a recurrence of the discovered event), and an indication of the confidence in the verdict and severity of the event to help in ranking. All IoAs are mapped to MITRE ATT&CK to provide detailed information including the ATT&CK-defined technique used, a description and mitigation strategies. This means you can automatically benefit from top-level threat research without overloading highly skilled in-house experts - freeing up their time for other complex tasks like deep incident investigation & threat hunting. You can also create your own database of custom IoAs appropriate to your particular infrastructure, for example, or to your industry sector.
Enhanced anti-malware engine. Working on a central node, with more aggressive settings than are enabled on endpoint configuration, the engine scans objects for malicious or potentially dangerous code as well as sending objects with potentially malicious contents to the sandbox. This results in highly accurate detections that can be of significant value during the incident investigation stage.
IoC scanning. The KATA Platform allows centralized IoC loading from threat data sources and supports automatic scheduled IoC scanning, streamlining the analysts’ work. Retrospective database scans can be used to enrich the quality of information about previously flagged security events and incidents.
Certificate verification. The Certcheck module checks the validity of signed certificates and the presence of suspicious certificates.
KATA Platform services for IT security experts also include:
Detection with YARA rules. YARA is one of the most frequently used tools for hunting new variants of malware. It supports complex matching rules to search files with specific characteristics and metadata - for example, strings that characterize a particular coder's style. It’s possible to create and upload customized YARA rules in order to analyze objects for threats specific to your specific organization.
Retrospective analysis. Automating data, object and verdict collection and their centralized storage allow to conduct retrospective analysis while investigating multi-stage attacks, even in situations where compromised endpoints are inaccessible or when data has been encrypted by cybercriminals. In addition, saved files from mail and web traffic can be automatically rescanned periodically, applying the latest updated detection rules.
Powerful flexible query builder for proactive threat hunting. Analysts can build complex queries in searching for atypical behavior, suspicious events and threats specific to your infrastructure, to improve the early detection of cybercrime activities.
Kaspersky Threat Intelligence Portal access. Manual threat queries in our Threat Intelligence knowledgebase give IT security analysts additional context for threat hunting and effective investigation.
KATA Platform aggregates data for analysis from different sources:
A network sensor receives copies of all traffic data, from which it retrieves objects and network metadata for further analysis. Network sensors detect activities in multiple areas of the IT environment enabling the ‘near real-time’ detection of complex threats in proxy, web and email environments:
- The network sensor is able to extract information about the source, destination, volume of data and periodicity of network traffic (even when the file is encrypted). This information is generally sufficient for a decision to be made about the level of suspicion to apply, and to detect potential attacks. SMTP, POP3, POP3S, HTTP, HTTPS, ICAP, FTP and DNS protocols are supported.
- The network sensor can intercept web traffic and handle objects transmitted by HTTPS by means of integration with the proxy server via the ICAP protocol.
- The email sensor supports integration with mail servers, via POP3 and SMTP connection to the specified mailbox. The sensor can be configured to monitor any set of mailboxes.
In addition to full network traffic analysis, the platform can provide an automated gateway-level response to complex threats, using Kaspersky Secure Mail Gateway and Kaspersky Web Traffic Security as a full-featured network sensors serving the KATA Platform.
Endpoint sensors (Kaspersky EDR) gather all the necessary data from endpoints across your infrastructure. Agent deployed on endpoints constantly monitor processes, interactions, open network connections, operating system status, changes to files, etc. They then send the collected data and information relating to the detection of suspicious events to the KATA Platform for additional study and analysis, as well as for comparison with events detected in other information flows.
The KATA Platform in use
By implementing the listed above technologies under a unified server architecture and with centralized management, the KATA Platform secures potential threat entry-points at network and endpoint levels, including web and mail servers, PCs, laptops, servers, and virtual machines, delivering a detailed insight into what's happening across your organization’s IT infrastructure. KATA gives your IT Security Specialists a comprehensive toolkit for multi-dimensional threat discovery, in-depth investigation, proactive threat hunting and a centralized response to complex incidents.
The KATA Platform integrates with Kaspersky Endpoint Security for Business to offer endpoint protection that includes the automatic blocking of threats and responses to complex incidents. It also integrates tightly with both Kaspersky Security Mail Gateway and Kaspersky Web Traffic Security, to block email- and web-based threats and to provide an automated response to more complex threats. This all-in-one solution significantly reduces the time and energy your IT security teams need to spend on advanced threat protection, thanks to the optimum automation of defensive actions at both network and endpoint levels, enriched with Threat Intelligence and managed through a single web console.
The KATA Platform protects corporate infrastructure against complex threats and targeted attacks without the need to attract additional resources. Embedded into your current strategy, the Platform equips your IT Security Team or SOC to counter complex threats and targeted attacks reliably and effectively, complementing existing third party protection technologies and supporting interaction with your SIEM.
