Kaspersky Lab experts have investigated one of the most active APTs (Advanced Persistent Threats) in Asia, operating specifically around the South China Sea area. It was named “Naikon” after the “nokian” User-Agent substring within an attack components’ code.
Why Naikon matters
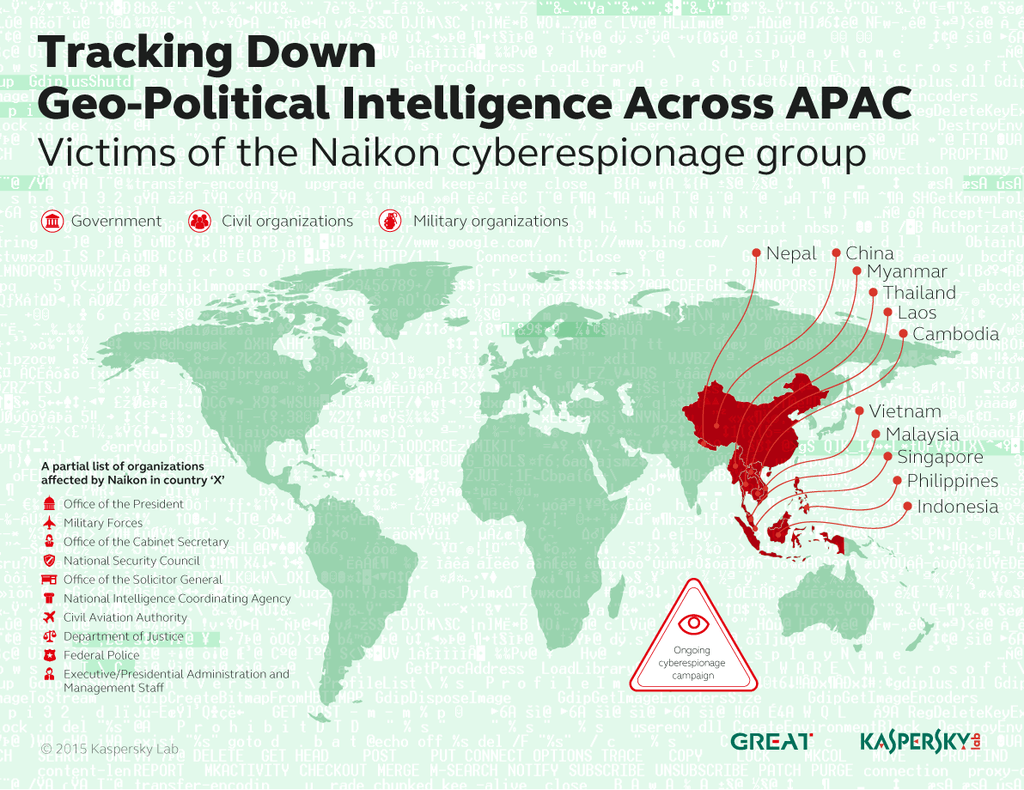
Naikon attackers appear to be Chinese-speaking, targeting top-level government agencies in the region, as well as civil and military organizations in countries including the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, Nepal, Thailand, Laos and China.
At Kaspersky Lab, we see that these high volume, high profile geo-political and geographically focused attacks, featuring dynamic, well-organized infrastructure, lasting at least for the last five years. In some cases, Naikon relies on externally developed modules such as set of a full featured backdoors. Our own introduction to the Hellsing APT, incidentally, was through an attack from Naikon on a Hellsing-related organization.
To penetrate target networks, the Naikon APT typically relies on ‘traditional’ spear-phishing, using email attachments containing a CVE-2012-0158 exploit. This APT also spoofs fake file extensions, use RTLO (Right To Left Override, or, embedding a special Unicode character in a filename to make the real file extension reversed), or extra spacing (like “letter to Gov office.doc .exe” including up to 200 spaces). Finally, to increase the probability that the attached executable will be opened, they also modify file icons to look like word documents. While they are simple techniques, they were very effective against target organizations.
Naikon is the type of extremely well-made threat that any enterprise should be alert to when planning a comprehensive information security strategy.
KL technologies to fight Naikon successfully
The full list of measures available to mitigate APTs can be found here. Kaspersky Lab implements fully supports these measures and we implement them wherever appropriate in our own products.
Allowlists and heuristics
We recommend allowlists as the first endpoint-based protective measure to be taken against APTs. Along with timely OS and applications updating, effective user rights administration supported by allowlists can mitigate up to 85% of Advanced Persistent Threats.
The well thought-out deployment of a Default Deny scenario is vital for a truly comprehensive counter-APT strategy. According to Kaspersky Lab’s vision, such a strategy includes both network-based and endpoint-based elements, with technologies based on allowlists playing key roles. Over-cautious as this may sound, the reality is that there are still attack scenarios where typical Anti-APT solutions are powerless.
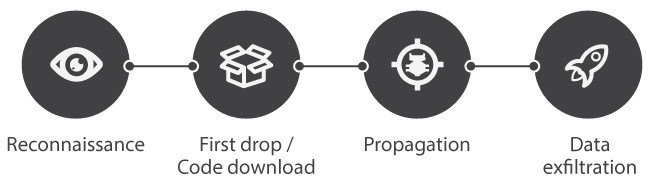
Allowlists are very useful at the first drop/code download stage of an APT, but it is not of course sufficient in itself. Besides allowlists, Kaspersky Lab implements other technologies to halt the APT at different stages. Multiple endpoint-based security layers should be considered when building an efficient defense against previously unknown malware components.
As spear-phishing (along with drive-by infection) is the main method of first drop distribution, enterprises should also take email security into account. Email security techniques including anti-phishing, anti-spam and the attachment control are implemented in Kaspersky Security for Mail Servers.
Kaspersky Lab Automatic Exploit Prevention (AEP) functionality and other technologies is highly effective at detecting Naikon components, the set of exploits it uses. Exploits are spotted using the verdicts “Exploit.MSWord.CVE-2012-0158.*” and “Exploit.MSWord.Agent.*”, while backdoors are detected as “Backdoor.Win32.MsnMM”. Other backdoors and components are detected under a variety of names, including “Trojan.Win32.Agent” and “Backdoor.Win32.Agent”.
Heuristic detection is also used. For obvious reasons, previously unknown malware samples cannot be detected using reputational databases. But we do know the typical patterns, indications for such malware. Heuristic algorithms are based on this knowledge, allowing security software to detect even 0-days. So heuristics are a crucial part of a multilayered comprehensive defense.
Further considerations
Deploying a specialized security solution is a must, but there are many purely administrative measures that can be taken to resist the Naikon APT. Regularly updating to the latest version of Microsoft Office will help get rid of CVE-2012-0158 attacks and others like it. Timely patching like this can most easily be achieved using a Patch Management toolkit, like that offered by Kaspersky Lab, working together with or instead of Microsoft WSUS. Vulnerability Assessment and Patch Management combined will also update all popular third party software to latest versions.
Microsoft EMET (Enhanced Mitigation Experience Toolkit) is a useful addition to Kaspersky Lab products with AEP implementation installed. Another recommendation is to disable Java wherever this application is not strictly necessary. Kaspersky Lab Application Control is of particular value here, allowing system administrators to choose which software is prohibited or allowed at any endpoint on the enterprise’s network.
All the mentioned technologies are implemented in security enterprise solution Kaspersky Endpoint Security for Business (KESB)
 APT
APT