Targeted e-mail attacks aren’t limited to spear phishing and business e-mail compromise (BEC). Another serious threat is conversation hijacking. In a nutshell, this is scheme where attackers insert themselves into a business e-mail conversation and pose as one of the participants. This post analyzes how such attacks work and what to do to minimize their chances of succeeding.
How do attackers gain access to e-correspondence?
To worm their way into a private e-mail conversation, cybercriminals need to somehow gain access to either a mailbox or (at least) the message archive. There are various tricks they can deploy to achieve this.
The most obvious is to hack the mailbox. For cloud services, password brute-forcing is the method of choice: attackers look for passwords associated with a particular e-mail address in leaks from online services, then try them out on work e-mail accounts. That’s why it’s important, first, not to use the same credentials for different services, and, second, not to give a work e-mail address when registering on sites unrelated to your work. An alternative method is to access e-mail through vulnerabilities in server software.
Malicious actors rarely stay in control of a work e-mail address for long, but they do usually have enough time to download the message archive. Sometimes they create forwarding rules in the settings so as to receive e-mail coming into the mailbox in real time. Thus, they can only read messages and not send any. If they could send messages they’d most likely try to pull off a BEC attack.
Another option is malware. Recently our colleagues uncovered a mass conversation hijacking campaign aimed at infecting computers with the QBot Trojan. The e-mails in which the cybercriminals planted their malicious payload most likely came from previous victims of that same QBot malware (which can access local message archives).
But self-styled hackers or malware operators don’t necessarily go in for conversation hijacking themselves — sometimes message archives are sold on the dark web and used by other scammers.
How does conversation hijacking work?
Cybercriminals scour message archives for e-mails among several companies (partners, contractors, suppliers, etc.). The dates don’t matter — scammers can resume conversations that go back years. After finding a suitable exchange of e-mails, they write to one of the parties involved, impersonating another party. The goal is to dupe the person at the other end into doing something required by the attackers. Before getting down to business, they sometimes exchange a few messages just to lower the other’s vigilance.
Because conversation hijacking is a targeted attack, it often uses a look-alike domain; that is, a domain visually very close to that of one of the participants but with some small mismatch — say, a different top-level domain, an extra letter, or a symbol substituted for a similar-looking one.
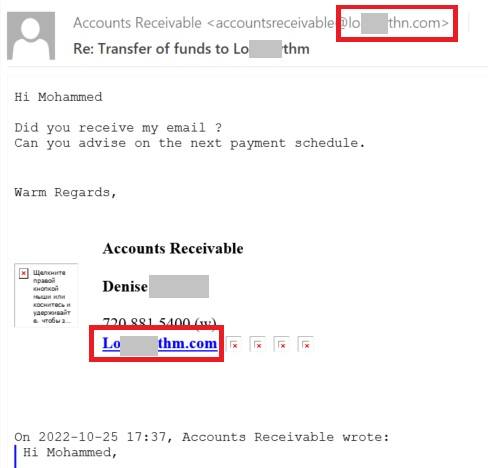
Attackers’ e-mail: the letter “n” appears instead of “m” in the domain name.
What is conversation hijacking used for in particular?
The objectives of conversation hijacking are generally rather banal: to gain access to some resource by stealing login credentials; to dupe the victim into sending money to the attackers’ account; or to get the victim to open a malicious attachment or follow a link to an infected site.
How to guard against conversation hijacking?
The main threat posed by conversation hijacking is that e-mails of this kind are quite difficult to detect by automated means. Fortunately, our arsenal includes Kaspersky Security for Microsoft Office 365, a solution that detects attempts to sneakily join other people’s conversations. To further reduce the risks to both you and your business partners, we recommend:
- Protecting employees' devices to make it harder to steal message archives from them.
- Using unique passwords for work e-mail accounts.
- Minimizing the number of external services registered to work e-mail addresses.
- Not only changing the password after an e-mail incident, but also checking to see if any unwanted forwarding rules have appeared in the settings.
 e-mail
e-mail
