About a year ago, UnitedHealth Group, the U.S. health-insurance giant, was targeted in one of the largest ransomware attacks ever. It had such far-reaching, severe consequences that new details about the attack and its aftermath have continued to emerge since the incident. To mark its anniversary, we’ve compiled a summary of all the data available today.
The ransomware attack on UnitedHealth Group
Before we proceed, let’s briefly introduce this organization to those unfamiliar with it. With a capitalization of approximately $500 billion, UnitedHealth Group is the largest company in the U.S. market for health insurance and healthcare services. It ranks ninth globally in terms of revenue — right after Apple.
UnitedHealth Group comprises two companies. One of them, UnitedHealthcare, focuses on health insurance. The other, Optum, specializes in delivering a broad spectrum of healthcare services ranging from pharmaceuticals and direct medical care to the IT systems underlying healthcare operations.
Optum Insight, one of Optum’s three divisions (and the most profitable), handles the latter. In the fall of 2022, UnitedHealth Group acquired the Change Healthcare platform, and Optum Insight integrated it. This digital platform processes insurance claims — acting as a financial intermediary between patients, healthcare providers, and insurers.
Change Healthcare was the target of the attack. On February 21, 2024, its systems were infected with ransomware — rendering the platform inaccessible. The incident wreaked havoc on the U.S. healthcare system, leaving many patients to shoulder the financial burden of medical expenses as insurance claims couldn’t be processed quickly. Healthcare providers were forced to process bills manually.
Recovering the compromised systems took several months. For instance, the Change Healthcare clearing service didn’t resume full operations until November. UnitedHealth Group even set up a dedicated website to track the restoration efforts. Even now, a year after the attack, the company is still regularly publishing updates on the website, and some systems are still listed as only “partially available”.
Timeline of the attack on UnitedHealth Group
A few months after the incident, on May 1, the CEO of UnitedHealth Group, Andrew Witty, was summoned to testify before Congress. From that testimony, the general public was finally able to learn about how the attack on the company unfolded.
According to Witty, the attack began on February 12. The attackers used compromised credentials to gain access to the Change Healthcare Citrix portal, which was used for remote desktop connections. Two-factor authentication should have stopped them but… it wasn’t enabled. Thus, attackers were able to gain entry simply by using the compromised credentials.
After gaining initial access, they began to move laterally and harvest data. The attackers clearly managed to collect a substantial amount of valuable data within the following nine days. In any case, on February 21, they deployed ransomware — initiating the encryption of Change Healthcare’s systems.
Faced with this situation, UnitedHealth decided to disconnect Change Healthcare data centers from the network to contain the ransomware attack.
Witty argued that the decision effectively prevented the infection from spreading to Optum, UnitedHealthcare, UnitedHealth Group, and any external organizations. However, the complete shutdown of a critical digital platform had a devastating impact on both UnitedHealth Group’s business operations and the broader U.S. healthcare system as a whole.
Thus, the most extensive ransomware attack of 2024 was caused by the absence of two-factor authentication on a remote desktop access portal — precisely the place where it absolutely should have been enabled. As Oregon Senator, Ron Wyden, summarized, “This hack could have been stopped with cybersecurity 101”.
UnitedHealth Group pays up
Several days after the breach, the BlackCat/ALPHV cybercrime gang claimed responsibility for it. The attackers claimed to have exfiltrated 6TB of confidential data — including medical records, financial documents, and personal information belonging to U.S. civilians and military personnel, among other sensitive information.
In March 2024, UnitedHealth Group paid a ransom of $22 million to the gang. But the story didn’t end there: after receiving the ransom, ALPHV feigned having their infrastructure seized by the FBI again. This was likely a ploy to double-cross one of their associates — pocketing the funds and disappearing into the ether.
Said associate claimed ALPHV had failed to give them their cut, and later teamed up with another ransomware gang — RansomHub. That gang made some of the stolen data public in April 2024, and then tried to extort more money from UnitedHealth.
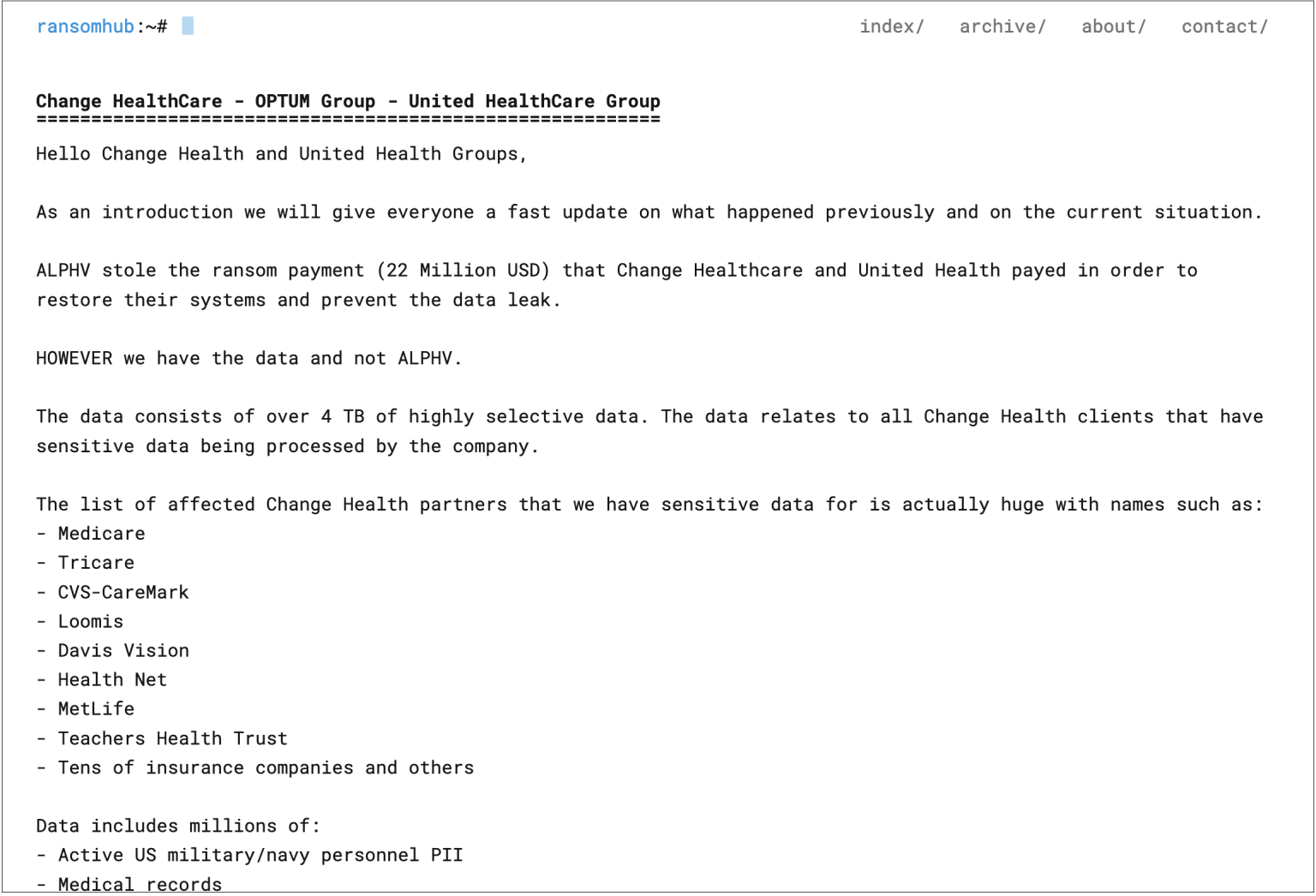
Post by RansomHub demanding a second ransom from UnitedHealth Group. Source
It remains unclear whether UnitedHealth ever paid the second ransom, as there was no official confirmation. However, the demand was later removed from RansomHub’s website, and no further leaks of the stolen company data have been observed. Therefore, it can be assumed that the company did, in fact, pay twice. This is even more likely if one considers that the ransom amounts are dwarfed by the massive financial impact the attack had on UnitedHealth Group.
The aftermath of the ransomware attack on UnitedHealth Group
UnitedHealth Group posted $872 million in losses associated with the cyberattack in Q1 2024 alone. The company also estimated in its Q1 report that the annual cost of the breach could reach $1.35 to $1.6 billion.
Those initial estimates proved to be far too optimistic: predicted damage kept growing quarter after quarter, first increasing to $2.3 to $2.45 billion, and then to $2.87 billion.
By the end of the fiscal year, as reported by UnitedHealth Group in January 2025, the incident resulted in a total annual loss of $3.09 billion. Although the damage estimate for 2024 is now finalized, the total damage could still increase substantially as the company continues to deal with the consequences of the attack.
An official estimate of the number of individuals whose data could have been stolen by the cybercriminals took a long time to materialize. It was only eight months after the incident, on October 24, 2024, that UnitedHealth Group finally came up with a tally. It was a mind-boggling figure: 100 million, or nearly a third of the entire population of the United States.
Nevertheless, it would become evident that these estimations were as overly hopeful as the original predictions about the financial losses. Three months later, at the end of January 2025, UnitedHealth Group released an updated report that put the number of those impacted by the breach at 190 million.
Protecting your company against ransomware
Clearly, the most obvious lesson to be learned from the UnitedHealth Group breach is that two-factor authentication is a must for any public-facing service. Otherwise, a single compromised password could cause massive problems and billions of dollars in losses.
Essential as it is, two-factor authentication is by no means sufficient protection against ransomware. Defending corporate infrastructure from ransomware attacks must be multilayered. Here are some additional tips:
- Raise your employees’ cybersecurity awareness through tailored training programs. Our Kaspersky Automated Security Awareness Platform, provides an easy and cost-effective solution.
- Segment your network, set up proper data-retention rules, and enforce data access policies. Ideally, adopt the XDR system.
- Engage an external threat-hunting and response service if your in-house information security team is under-resourced or lacks the expertise.
 Ransomware
Ransomware

 Tips
Tips