What do you need in order to withdraw cash from an ATM? First, you need to have a debit or credit card, which acts as a key to your bank account. Second, you must know the PIN code associated with the card; otherwise, the bank wouldn’t approve the transaction. Finally, you need to have some money in your account that you can withdraw. However, hackers do things differently: they don’t need cards, PIN codes or bank accounts to get money. In reality, all they need is an ATM with some cash in it and a special piece of software.
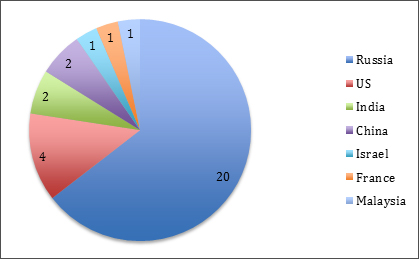
Earlier this year, at the request of a financial institution, our colleagues from the Global Research and Analysis Team (GReAT) performed a forensic investigation into a cyber-criminal attack that targeted multiple ATMs in Eastern Europe. What they discovered was quite impressive. Imagine this: a guy comes to an ATM, enters a code on a pin pad and almost instantly gets 40 banknotes, and then does it again and again. How can this be possible? Our experts say it’s all about a trojan called Tyupkin, which infects the PC inside of an ATM and forces it to dispense banknotes when prompted by a special code.
Hackers gained access to dozens of ATMs and dispensed a lot of cash
Tweet
As the investigation showed, criminals were somehow able to physically access the ATMs so that they could install the malware via a bootable CD on an imbedded Windows machine. The trojan that was used had complex abilities. First, when activated inside of the ATM, it had the ability to turn off the McAfee Solidcare AV software so that it could do its job with ease.
Second, to avoid accidental detection, Tyupkin trojan had the ability to stay in a standby mode for an entire week and activate only Sunday and Monday nights. Third, it had the ability to disable the local network in the case of an emergency, so that the bank could not remotely connect to the ATM to check on what was happening with it.
Thanks to all of these advanced features, all an attacker has to do is merely approach an infected ATM and enter a special PIN code in order to access the secret menu that will allow him to make cash withdrawals or control the trojan (for example, to delete it). To make a withdrawal the person has to know the appropriate commands, as well as a special formula that will calculate a session key — some kind of a two-factor authentication. If both codes are correct, then a second menu will appear that allows the criminal to choose the cassette number and make a withdrawal. Although one can only dispense 40 banknotes per transaction, it’s possible to dispense any amount of money by simply performing the actions several times over.
Attackers were able to steal hundreds of thousands of dollars from ATMS, all without attracting any attention. As Principal Security Researcher at Kaspersky Lab’s GReAT, Vicente Diaz, says, right now hackers can only infect certain ATM models, but the variety of hackable ATMs will grow unless banks and ATM manufacturers increase the physical, and software, protections of these machines.
 atm
atm



 Tips
Tips