Trojan subscribers represent a time-honored method of relieving Android users of their hard-earned cash. They infiltrate a smartphone under the guise of useful apps and secretly subscribe to paid services. More often than not, the subscription itself is genuine, only the user most likely does not need the service.
The creators of such Trojans make money on commission; that is, they receive a certain percentage of what the user spends. In this case, funds are usually deducted from a cell phone account, although in some schemes they can be debited directly from a bank card. Here are the most notable examples of the mobile Trojan subscribers that Kaspersky experts have observed in the past year.
Paid subscriptions and confirmation codes in text messages
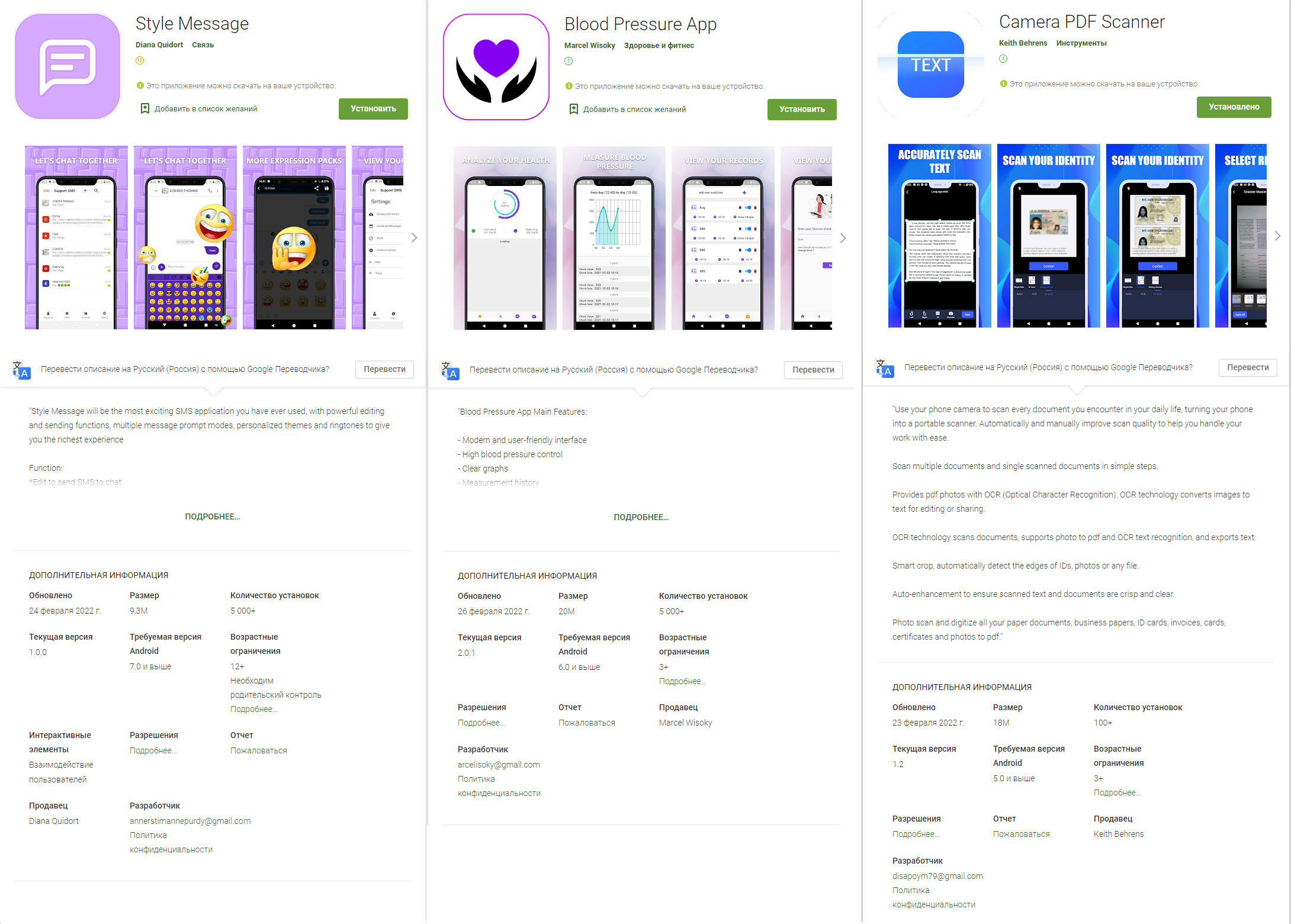
Trojans from the Jocker families usually get distributed through Google Play. Cybercriminals modify genuinely useful apps by adding malicious code to them and uploading to the store under a different name. These could be, for example, apps for text messaging, monitoring blood pressure, or scanning documents. Google Play moderators try to identify such apps, but new ones pop up faster than they can remove those already found.
Now let’s look at how Trojan subscribers work. In a normal situation, to subscribe to a service, a user has to go to the content provider’s site and click or tap the Subscribe button. To counter automated subscription attempts, service providers ask the user to confirm their intention by entering a code sent in a text. But malware from the Jocker family can bypass this method of protection.
After the infected app gets onto the device, in many cases it asks the user for access to text messages. Next, the Trojan opens the subscription page in an invisible window, simulates the tapping of the Subscribe button, steals the confirmation code from the text message, and freely subscribes.
In cases where the app functionality does not require access to texts (why give it to a document-scanning app, for example?), Trojan subscribers from the Jocker family request access to notifications. This makes it possible to steal the confirmation code as before, but this time from pop-up notifications about incoming messages.
How Trojan subscribers bypass CAPTCHA
Trojans from the MobOk family are a bit more sophisticated. They not only steal confirmation codes from texts or notifications, but bypass CAPTCHA — another means of protection against automated subscriptions. To recognize the code in the picture, the Trojan sends it to a special service — last year we investigated the operation of click farms that provide CAPTCHA recognition services.
In other respects, it operates similarly to Trojans from the Jocker family. In several cases, MobOk was distributed as the payload of the Triada Trojan, most often through pre-installed apps on some smartphone models, unofficial WhatsApp modifications, or the APKPure alternative app store. Sometimes MobOk-infected apps can be found on Google Play as well.
Trojan subscribers from unofficial sources
Malware from the Vesub family is also distributed through dubious sources under the guise of apps that are banned from official stores for one reason or another —for example masquerading as apps for downloading content from YouTube or fellow streaming services Tubemate or Vidmate, or as an unofficial Android version of GTA5. In addition, they can appear in these same sources as free versions of popular, expensive apps, such as Minecraft.
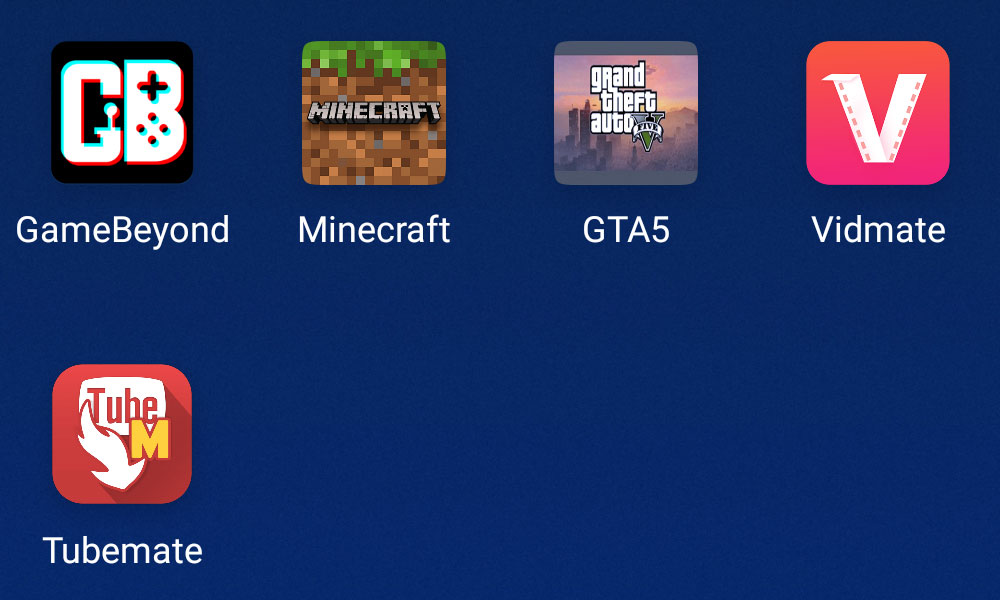
Trojan subscriber Vesub disguised as Tubemate, Vidmate, GTA5, Minecraft or the somewhat mysterious GameBeyond
Unlike malware from the MobOk and Jocker families, Vesub-infected applications often do nothing useful for the user at all. Immediately after installation, they take out an unsolicited subscription and hide the relevant windows from the user while showing an app loading-window on the surface. In some cases there’s something useful inside the app infected with MobOk, but these are rare exceptions.
Login by phone number
GriftHorse.ae Trojans are even less fancy. When run for the first time, they ask the user to enter their phone number, seemingly for login purposes. The subscription is issued as soon as the user enters it and taps the Log In button, and the money is debited from their mobile account. This malware usually presents itself as an app for recovering deleted files, editing photos or videos, blinking the flashlight on incoming calls, navigation, document scanning, translation, and so on. In reality the infected apps offer nothing useful at all.
Autopay subscriptions
Despite the similar name, GriftHorse.l subscribers use a different scheme: they employ subscriptions with recurring payments. Formally this happens with the user’s direct consent, but victims may not realize they are signing up for regular automatic payments. The second trick is to make the first payment insignificant, with later charges being noticeably more substantial.
We’ve already examined a similar scheme as illustrated by fake sites offering subscriptions to training courses. In this case the mechanics are roughly the same, but implemented inside the app. The Trojan is distributed largely through Google Play, and the money is debited directly from a bank card, with payment information being requested to gain access to the content.
How not to fall victim to scammers
Figuring out how to cancel an unwanted paid subscription can be very tricky. So, as ever, prevention is better than cure. Here’s what we recommend to guard against Trojan subscribers:
- First of all, do not install apps from unofficial sources. This will greatly improve the security of your device.
- Official sources are way better, but unfortunately not 100% safe either. Therefore, before downloading an app from Google Play or another store, be sure to check out the reviews and ratings.
- Also look at the date when the app appeared on the platform. Stores proactively remove dangerous fakes, so scammers are forever creating new versions of infected apps. So if an app you want showed up in the store only recently, be wary of it.
- Give apps minimal access to your device. Before allowing an app to read your texts or notifications, for example, ask yourself if it really needs to.
- Install a reliable mobile antivirus — this will protect your phone from all digital nasties, including Trojan subscribers.
 Android
Android