In early 2025, the Chinese chatbot, DeepSeek, burst onto the AI scene. It provoked much comment and controversy across the globe: we could hardly fail to spot the similarity of its logo to our own, comparisons with ChatGPT were abundant, and in Italy, South Korea, Australia, and other countries, DeepSeek was blocked altogether. The hype was — and remains — intense, including among cybercriminals.
We’ve discovered several groups of sites mimicking the official chatbot website and distributing malicious code under the guise of what appears to be a legitimate client. To find out exactly how these cybervillains operate, and how to use AI safely, read on…
Malicious scripts and geofencing
Several malware distribution schemes were detected, all of which had the use of fake DeepSeek websites as the common denominator. The difference lies in what was distributed through these sites and how. This post thoroughly explores one of these schemes; for details on the others, see our full report on Securelist.
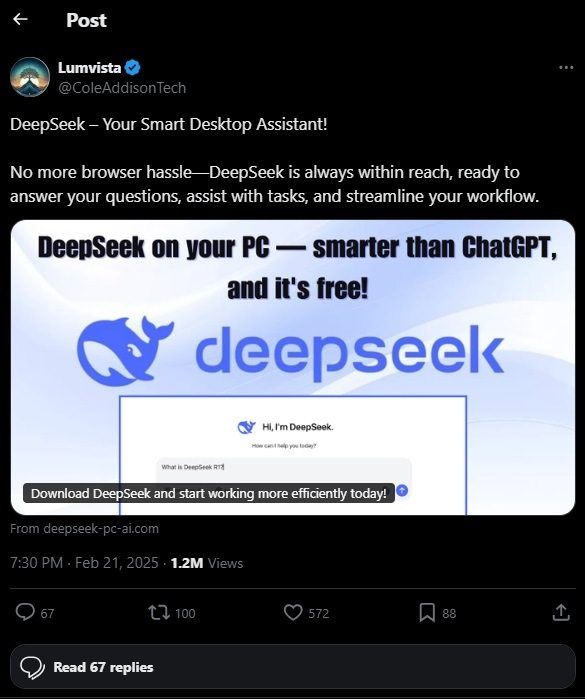
What would you think if you landed on a website with the domain deepseek-pc-ai[.]com or deepseek-ai-soft[.]com? You’d probably assume you could find there some DeepSeek-related software. And what kind of software might that be? A DeepSeek client, of course! And indeed, you’ll quickly see the bright Download and slightly duller Start Now buttons that greet visitors to the site.
Whichever of these buttons you click, an installer starts downloading. But there’s a catch: once initiated, instead of installing DeepSeek, the installer accesses malicious URLs, and manipulates scripts to activate the SSH service in Windows to configure it to work with the attackers’ keys. This enables them to remotely connect to the victim’s computer, who doesn’t even get a DeepSeek Windows client as consolation… which, by the way, doesn’t exist.
Interestingly, the fake sites use geofencing — restricting access based on the region of the IP address. For example, users from Russia on these domains saw a simple stub site with empty texts about DeepSeek — most likely generated by DeepSeek itself or a different large language model. Visitors from other countries, however, were taken to the malicious site distributing the fake client.
A million views on X
The main vector for distributing links to the malicious URLs was posts on the social network X (formerly Twitter). One of the most popular posts (now deleted) was published from the account of Australian startup Lumina Vista, which, open sources say, has no more than 10 employees. The company’s account itself is in its infancy: it only got the coveted blue check-mark in February 2025, and boasts just a dozen posts and fewer than 100 subscribers. Yet the post promoting the fake DeepSeek site garnered 1.2 million views and more than 100 reposts. Bit fishy? We investigated the accounts that reposted it and concluded that they could be bots, since all use the same naming convention and identifiers in the bio section. Incidentally, it’s quite possible that Lumina Vista’s account was simply hacked and used for paid promotion of the attackers’ ad post.
In the comments, some users pointed out that the link leads to a malicious site, but they were in the minority — the rest were simply expressing views about DeepSeek, Grok, and ChatGPT. However, none of the commenters noted the obvious: DeepSeek has no native client for Windows, and you can only access it in a browser. You can also run DeepSeek locally but that requires specialized software.
How to use AI safely
At present, it’s not easy to assess the scale of this and other malicious schemes involving fake DeepSeek pages. But one thing is for certain: these campaigns are massive and not targeted at specific users. Yet they’re developing very quickly: soon after the announcement of Grok-3, attackers began offering to download its client both from the domain v3-grok[.]com, and from… v3-deepseek[.]com! Indeed, Grok, DeepSeek – what’s the difference?…
Without reliable protection, any AI enthusiast is at risk. That’s why it’s vital to follow the safety rules and recommendations when using AI.
- Check the URLs of websites you visit. Especially when it’s something new, popular, and easy to spoof.
- Filter sensitive data. Remember that what you write to a chatbot could be used against you: as with other cloud services, data can leak due to security flaws or account hacking.
- Protect your devices. Check out the reviews and choose the best solution for you that will spot phishing sites and guard against downloading malware.
- Limit the use of third-party plugins. Every add-on app creates new threats. Special monitoring is required for execution plug-ins that can, for example, run malicious code to buy a plane ticket at your expense.
If you’re seriously interested in neural networks and want to learn how to use them safely, check out these posts:
 AI
AI


 Tips
Tips