Kaspersky Lab has discovered an ultra-massive money-stealing campaign codenamed Carbanak APT with total losses summing up to $1 bn so far. The campaign is still active. Kaspersky Lab’s researchers Sergey Golovanov and Sergey Lozhkin presented the research on Carbanak yesterday at the Kaspersky Security Analyst Summit. Follow the live blog here.
One day there will be a movie
In late 2014 Kaspersky Lab has predicted that money-minded criminals are going to switch targets moving closer to the point of their interest. Simply put, they’ll attack banks. This is just what has happened. According to information provided by law enforcement agencies and the victims themselves, total financial losses could be as a high as $1 billion, making this by far the most successful criminal cyber campaign we have ever seen. Perhaps one day there will be a movie, as with the Great Gold Robbery of 1855.
Around the world
Coming back to the point, Carbanak investigation started in Ukraine where money had been siphoned mysteriously straight from the ATM. It then moved to Moscow; most of the victims are located in Eastern Europe, but, thanks to the data obtained from the Command and Control servers, we know that Carbanak also targets entities in the USA, Germany and China.
https://twitter.com/k1k_/status/567406121636220930
A backdoor and a manual recon
From what is known so far, attackers plant a Carberp-based backdoor into their victims’ systems. The initial attack starts with a spear phishing e-mail with a malicious attachment; there were also cases where Word documents exploiting known vulnerabilities were used. After executing the shellcode, the backdoor is brought in.
Interestingly, attacker then proceed on performing a manual reconnaissance, trying to detect and compromise “relevant” computers, such as those of administrators. Their actual points of interest are the systems through which it is possible to extract money.
To understand how a particular bank operates, infected computers were used to record videos that were then sent to the Command and Control servers. The relatively poor quality of the videos was still good enough for the attackers, armed also with the keylogged data for that particular machine to understand what the victim was doing. This provided them with the knowledge they needed to cash out the money.
Cash ’em out
During the investigation several ways of cashing out had been found. Either ATMs were instructed remotely to dispense cash without any interaction with the ATM itself, with the cash then collected by mules; or the SWIFT network was used to transfer money out of the organization and into criminals’ accounts. Also, databases with account information could have been altered so that fake accounts could be created with a relatively high balance, with mule services being used to collect the money.
The campaign had been active since, presumably, December, 2013. The peak of infections was recorded in June 2014, the campaign is still active, thus barely any financial organization can feel totally safe.
All Kaspersky Lab’s corporate products and solutions detect and block known Carbanak samples.
A few general safety recommendations:
- Do not open suspicious emails, especially if they have an attachment;
- Update your software regularly
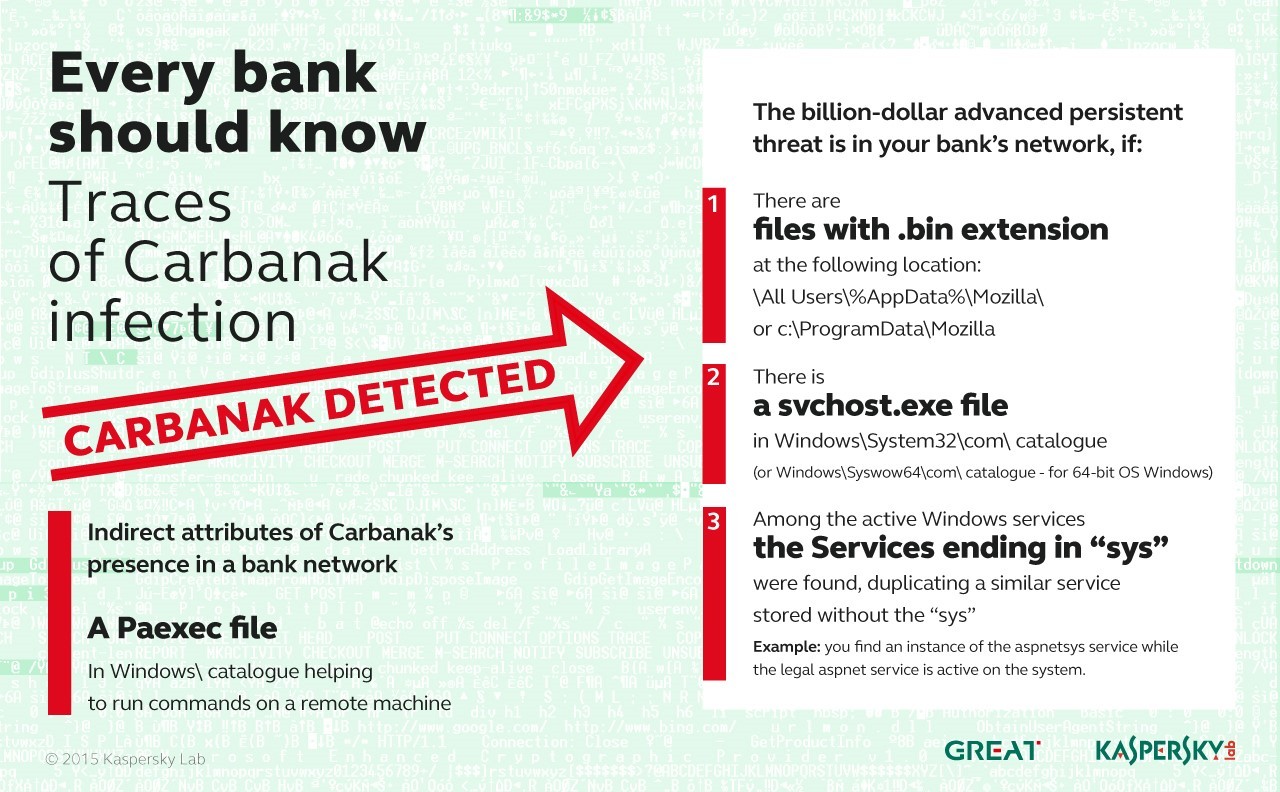
A slide below also shows, how the traces of Carbanak infection can be detected:
The more detailed report and a link to full disclosure is available at Securelist.
 Carbanak
Carbanak

 Tips
Tips