On February 16th and 17th in Cancun, Mexico, the Fourth annual Kaspersky Security Analyst Summit took place. That’s an extremely important event for Kaspersky Lab, where we share our researches and invite to speak our colleagues from other companies from security industry.
#TheEquationAPT, #Carbanak, #DesertFalconsAPT: #SAS summary
Tweet
In this particular post we discuss three of our keynotes from Security Analyst Summit regarding The Equation APT, Carbanak and an unknown before entity that we called Desert Falcons APT group. If you are interested in detailed research, please follow the appropriate links to Securelist. Here you can also find a few pictures from the Summit, and later videos from our experts’ keynotes will be available either.
Carbanak. The Great Robbery
Securelist full report with technical details. Indicators of compromise (in .IOC format).
A lot of comments come on the ATM compromise aspect of Carbanak, which is indeed the most high-profile part of the story: one sends a command, the ATM yields money, with no card or PIN required.
Actually, this is where Carbanak failed: it’s clear that ATMs don’t work that way without a third party intervening. Further investigation showed that ATM cracking was just one method of cashing out. There were others too: criminals could transmit funds to their own accounts, manipulate the balance so that multiple security systems failed to detect it. Without total control about internal bank systems the operation like this would be impossible to conduct. So after the initial infiltration attackers used various methods to gather data on internal workings of the bank, including recording the video.

The actual attack started quite trivially:

A letter with a malicious payload exploiting, among others, Microsoft Office vulnerabilities (CVE-2012-0158; CVE-2013-3906) and Microsoft Word (CVE-2014-1761).
So where the $1 bn came from?
Carbanak investigation had been conducted in close cooperation with various LEAs in various countries. Peter Zinn from National Hi-Tech Crime Unit told about it during his speech in Kaspersky Security Analyst Summit.

Information from law enforcement agencies allowed to evaluate the total number of Carbanak victims – about 100 financial organization. Given the on average they lost between $2.5 and $10 million, the total possible losses may mount exactly up to $1bn.
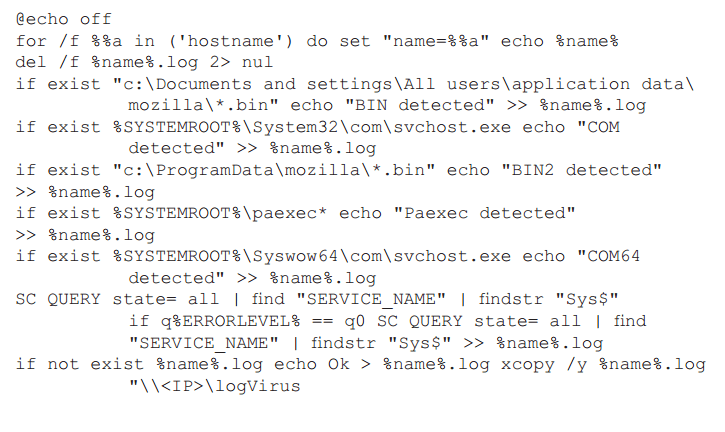
A saviour .bat:
An interesting situation took place during the investigation, when the fact of infection had been already confirmed and there was a need to identify all of the compromised PCs. It should have been done fast: first – to block the threat, second – to gather samples to research. A simple script had been written for this:
The Equation, or “Stuxnet, I am your father”, or attribution difficulties
A Securelist article, Q&A (pdf), Fanny module research
Every SAS guest received as a present Kim Zetter’s book on Stuxnet, signed by author. For your information, it’s a gross 500 pages tome, and, according to Zetter, publisher requested to shorten technical details as much as possible. So if one day a book on The Equation will be written, it won’t be any smaller. An important thing: the investigation of this operation is just beginning right now. We have only published the general information and made a detailed research of one of its modules. Further research will demand time and effort, both from Kaspersky Lab and other companies. Why? Those behind Equation APT is doing their business for more than 10 years, probably even for 20 years already, given the date of first C&C servers domain registration.

Kaspersky Lab researchers speaking on The Equation at SAS: Igor Sumenkov, Sergery Mineev, Vitaliy Kamlyuk, Costin Raiu.
Grzegorz Brzęczyszczykiewicz
We have identified with certainty more than 500 victims of The Equation. Given that malicious modules of the operation are armed with self-destruct mechanism, the actual total number of victims may be dozens of thousands. Among them – governmental organizations, telecoms, aviation industry, gas and oil sector, etc. Our research started when an individual named Grzegorz Brzęczyszczykiewicz (spelled approximately “G(r)zhego(r)zh B(r)zhechishchikevich”) suspected that he was a victim of a malicious attack after he has inserted into his CD-Rom a CD with pictures sent to him from a scientific conference in Houston, he was participating in.
His name has been changed for confidentiality reasons. It’s been chosen from this flick:
What do we know about The Equation now? According to the dates of domain registration and module compilations, the campaign had been active for dozens of years. The oldest modules support Windows 95/98. Different modules had been used for attacks and data gathering, as well as different methods of infection had been used too (infecting forums, for instance). One of the modules, known as Fanny, was used to gather data on the victims in Asia and Middle East. It had been created in 2008 and exploited two 0day vulnerabilites. The same ones Stuxnet used later. “Later” is the keyword here: this fact, alongwith some other, imply there was a connection between Stuxnet and The Equation.

And this plugin is, perhaps, the most interesting. Known only by the file name (nls_933w.dll), it was extremely rarely used, in the outstanding cases it allowed to change hard drive (or SSD) firmware. Why? First – to restore control over the victim’s PC, even if the data had been wiped clean. Second – for reliable and stealthy data storage. The plugin code yieleded identifiers for 12 hard drive models, those could be subjects to such a procedure. Given that firmware is extremely difficult to analyze and any error can brick the hard drive completely, this module shows how potent this APT group is.
Attribution
Now, this is important: “Kaspersky Lab” can say absolutely nothing about those who is behind Equation APT. We just don’t have enough facts to put a substantiated blame on anyone, or even identify the region or the country the operation had been conducted from. Everything else here is wool-gathering and gossip, and we don’t want to relate ourselves to it. Attribution is a very difficult task, afterall, since even the obvious hints on the origins of the malware creators found in the code (in general, not in The Equation code) sometimes are introduced specifically to send researcher on the wrong track.
TWITTER PULLQUOTE
We don’t know who is behind #TheEquationAPT: no enough facts. #nogossip
Tweet
Attribution difficulties have been discussed several times during Security Analyst Summit. Here’s a joking example of speculative approach in Juniper Networks’ Christopher Hoff’s presentation: bullshit attribution bingo.

Desert Falcons: a new APT campaign in Middle East
An article at Securelist. A detailed research (pdf).

What surprised me the most in Dmitri Bestuzhev’s keynote on Desert Falcons, is that how thoughtful are the attackers about the social engineering. Certainly they attack vie e-mail:
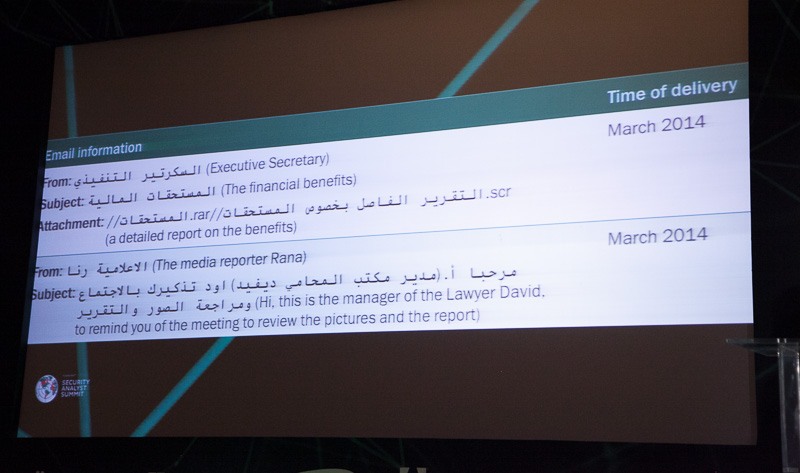
But not just that. They use Facebook. Send friends requests, talk to in in PM, get themselves prepared for months, gain your confidence, all that to send you eventually a link to a malicious file. Or even simpler, they exploit the fact that influential people don’t block their “wall” from posting at by other people. They react at the key events, important for the potential victims, and adapt their messages and emails.
Those behind Desert Falcons know their victims very well. Probably since they reside in one particular country in the Middle East themselves. This is the primary point in this research: we see a new player developing its own tools to attack and gather data (not using someone else’s stolen tools), well aware of the local landscape. Unlike The Equation, Desert Falcon have come in relatively recently – in 2011, and are at their peak now. Results: the data stealing malware infecting PC and Android-based handhelds, with over a million files and documents stolen from 3000+ victims.
We’re preparing a few more posts based on the keynotes at Security Analyst Summit, on such topics as using legitimate software for criminal purposes (including those in cryptolockers) with separate overview and statistics. A Live-blog at Kaspersky Daily shows quotes from almost all SAS speeches and most interesting social media comments.
 APT
APT
