Interpol and Kaspersky Lab’s Global Research and Analysis Team (GReAT) have just announced details of a new threat with a meaningful name, “Darkhotel”. The threat has been active for at least four years, with thousands affected so far.
The Darkhotel’s main purpose is a sophisticated cyber-espionage campaign aimed at corporate executives: CEOs, senior vice presidents, sales and marketing directors, and top R&D staff have all been targeted. The campaign resembles the plot of a spy film, a Stephen King novel, and a whodunit all rolled into one. Fortunately, there are no bloodied corpses or detached limbs, but that’s really the only good thing about it.
So what’s the dark story?
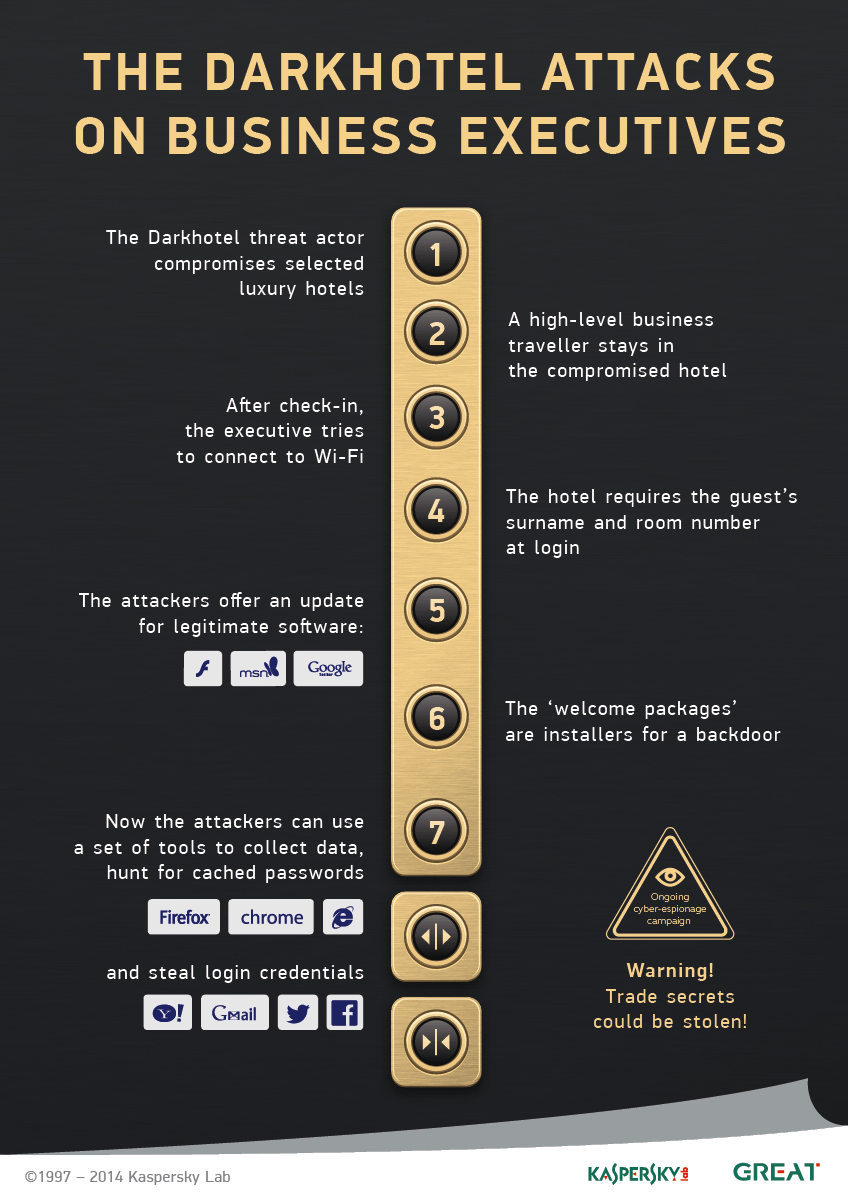
In certain areas in Asia there are luxury hotels, frequented by high-level executives from Asian and European countries and the U.S. The name and location of these hotels understandably won’t be disclosed, but places like these are assumed to sell not just comfort, but privacy and security. However, the latter two aren’t always there.
The dark story of #Darkhotel #enterprisesec
Tweet
After check-in, the guest most likely will try to connect to Wi-Fi on the local network. The hotel requires his/her surname along with a room number at login.
Right after login the guest is prompted to download an update for legitimate software like the Google Toolbar, Adobe Flash or Windows Messenger. Well, if at this point you are suspicious, you’re correct in being so: They’re not legitimate software updates. The unsuspecting user has just installed a backdoor.
Once downloaded to the machine, the backdoor helps attackers identify how important the victim is. Then they decide whether to have the user download more advanced tools. They have many ready: a digitally-signed advanced keylogger; Trojan “Karba”, which collects data on the system and the anti-malware software installed on it; an information thief module designed to hunt for cached passwords for Firefox, Chrome and Internet Explorer browsers, along with Gmail Notifier, Twitter, Facebook, Yahoo! and Google login credentials, and other private information. Victims lose sensitive data – likely the intellectual property of the business entities they represent. It’s important to note that after the operation, attackers carefully clean up all traces of their activities – namely, remove their tools from the hotel network and blend into the background.
 Technical details are available at Securelist.
Technical details are available at Securelist.
Hotels, even the luxury ones, aren’t exactly safe cybersecurity-wise. Public computers used by the visitors in order to access the Web are often equipped with obsolete and unsupervised software (Windows XP included), and are occasionally brimming with all kinds of the malware. It’s extremely dangerous to access any sensitive data from such PCs, or any public PC in general (unfortunately people don’t care too much, unless they lose money).
In a luxury hotel, a visitor would reasonably expect that the “petty cybersecurity problems” are non-existent there and he will be safe from anything like this. That is not the case. Darkhotel infections are spread across thousands of machines globally with the majority (90%) of victims being located in Japan, Taiwan, China, Russia, and Korea. Other affected countries are Germany, the U.S., Indonesia, India, and Ireland.
Darkhotel malicious activity can be inconsistent, however: alongside its highly targeted attacks there is an indiscriminate spread of malware. The attackers use botnet-style operations for massive surveillance or to perform other tasks, such as DDoS (distributed Denial of Service) attacks or to install more sophisticated espionage tools on the computers of particularly interesting victims. They also spread malware indiscriminately via Japanese P2P (peer-to-peer) file-sharing sites. The malware is delivered as part of a large RAR archive that purports to offer sexual content, but installs a backdoor Trojan that allows attackers to perform a mass surveillance campaign.
This Darkhotel package was downloaded over 30,000 times in less than six months.
Luxury hotels are presumed to be safe places. Are they? #security
Tweet
“The mix of both targeted and indiscriminate attacks is becoming more and more common in the APT scene, where targeted attacks are used to compromise high profile victims, and botnet-style operations are used for mass surveillance or performing other tasks such as DDoSing hostile parties or simply upgrading interesting victims to more sophisticated espionage tools,” says Kim Baumgartner, Principal Security Researcher at Kaspersky Lab.
So far, the attackers behind Darkhotel APT seem to be interested in defense industrial bases (DIB), governments, NGOs, large electronics and peripherals manufacturers, pharmaceutical companies, medical providers, military-related organizations, and energy policy makers. The attacks follow the typical spearphishing process with thoroughly disguised Darkhotel add-ins.
Email-lure content often includes topics like nuclear energy and weaponry capabilities, which most likely means the attackers are well aware of current events in the world. Over the past several years spearphishing emails have contained an Adobe zero-day exploit or links that redirect targets’ browsers to Internet Explorer zero-day exploits. The attackers, according to Baumgarter, “possesses operational competence, mathematical and cryptanalytical offensive capabilities, and other resources that are sufficient to abuse trusted commercial networks and target specific victim categories with strategic precision.”
Judging by the code of the malware analyzed by Kaspersky Lab’s experts, the APT attacker is Korean-speaking.
International business and industrial cyberespionage are no longer considered exotic. They are present everywhere, and there are a lot of interested parties with capabilities well beyond your average script. They are even more advanced than seasoned cyber-fraudsters such as those who have recently “skimmed” many ATMs with malware, stealing millions. The most important factor is not who’s behind the attacks, but that all public Wi-Fi, including those that are semi-public in hotels are unsafe, and using them – especially installing any software from them (even if the source seems legitimate) – may be harmful.
A few quick facts and recommendations regarding Darkhotel:
- The attackers left a footprint in a string within their malicious code pointing to a Korean-speaking attacker.
- Kaspersky Lab’s products detect and neutralize the malicious programs and their variants used by the Darkhotel toolkit.
- Kaspersky Lab is currently working with relevant organizations to best mitigate the problem.
In order to ensure safety, Kaspersky Lab recommends the following measures:
- Choose a Virtual Private Network (VPN) provider – you will get an encrypted communication channel when accessing public or semi-public Wi-Fi;
- When traveling, always regard software updates as suspicious. Confirm that the proposed update installer is signed by the appropriate vendor.
- Make sure your Internet security solution includes proactive defense against new threats rather than just basic antivirus protection.
Click here for more about privacy tips.
 APT campaigns
APT campaigns