
Log4Shell a year on
A year after discovery, the Log4Shell vulnerability is still making itself felt.
234 articles

A year after discovery, the Log4Shell vulnerability is still making itself felt.

We investigate the connection between software security and leaks when handling RAM.

In 2022, cryptocurrency prices fell sharply, but malicious miners are more active than ever.

An interesting bug in one of the most popular embedded DBMS.

How a vector graphics editor helped create one of the internet’s most important technologies, and why it led to huge security risks.

Servers with the Zimbra Collaboration suit installed are being attacked via an archive unpacking tool.

How even high-end solutions for business can have “childish” bugs in their update delivery systems.

The developers of a run-of-the-mill Python module recently found out why old unpatched vulnerabilities can be dangerous.

It’s time to update! Microsoft patches 64 vulnerabilities in a variety of products and components — from Windows and Office to Defender and Azure.

An unusual case of an attack executed by weaponizing legit video game code.

Takeaway from DEF CON 30: vulnerability in Zoom for macOS.

Using a recent study on hardware vulnerabilities in processors as an example, we contemplate the cost of security.

Microsoft has released patches for more than 140 vulnerabilities, some of which need to be closed as soon as possible.

We recall the story of the ILOVEYOU worm — one of the most infamous viruses from 22 years ago.
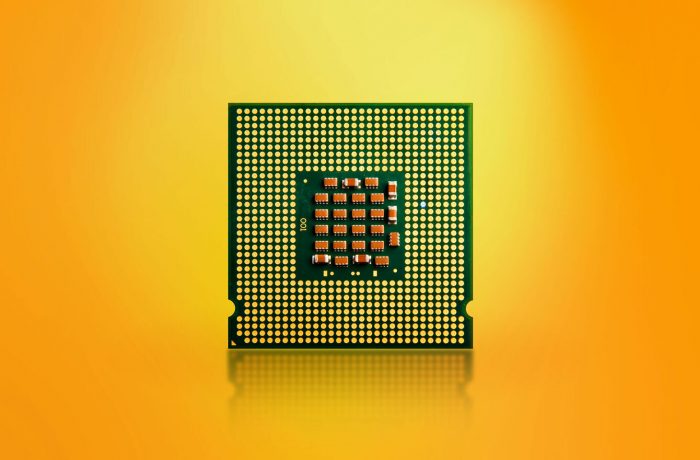
One of the most complex, yet easy to understand, infosec studies of recent times.

Can a device be hacked when switched off? Recent studies suggest so. Let’s see how this is even possible.

New vulnerability CVE-2022-30190, aka Follina, allows exploitation of Windows Support Diagnostic Tool via MS Office files.

The Department of Homeland Security is urging US federal agencies to “patch or remove” a list of VMware products within five days. Probably you should do it too.

Time to update Windows! Microsoft has released patches for several dozen vulnerabilities, one of which cybercriminals are actively exploiting.

Microsoft patches 128 vulnerabilities in a list of products, including Windows and its components.

If you use an iPhone, it’s crucial to always install the Safari and WebKit updates, even if your browser of choice is Chrome, Firefox or something else. Here’s why.