
Small Business Story: Music and Stage Equipment Manufacturer
We’re continuing the series “Small Business Stories”, in which CEOs of small companies talk about the role IT plays in their general activities and in the protection of their information.
12 articles

We’re continuing the series “Small Business Stories”, in which CEOs of small companies talk about the role IT plays in their general activities and in the protection of their information.

Mr. Vitaly Kamluk, Kaspersky Lab’s security researcher, enters the stage, goes over a certain number of slides, and then proceeds to do a live demo. He warns the audience about
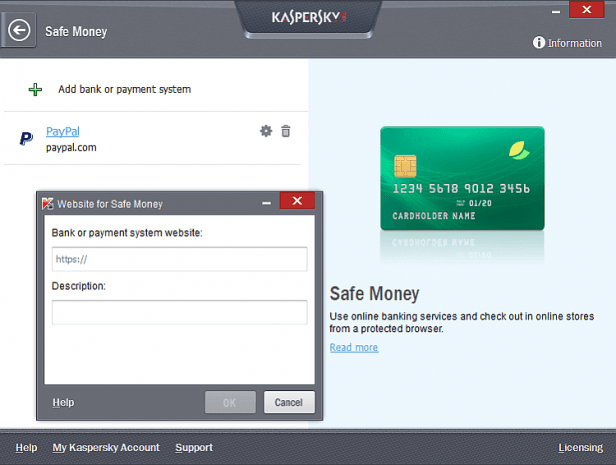
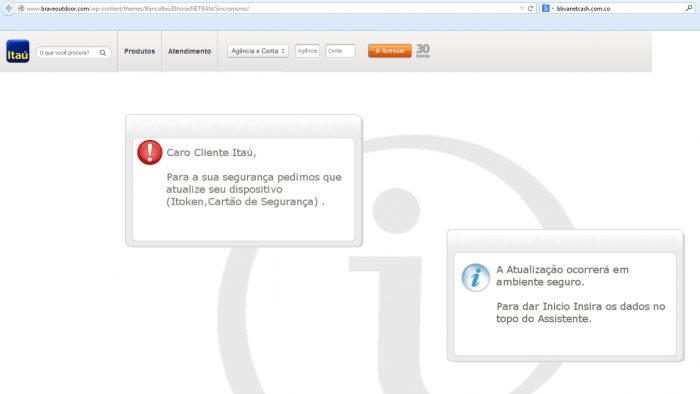
Online payments have remained one of the most vulnerable sections of the IT perimeter. Most banks and payment systems now have two-factor authentication. However, not all of them have instituted
We are starting a series of articles “Small business security stories” in which executives of formally small business companies talk about the role of IT and particularly data protection in

Information security sites are brimming with discussions surroudning a new program, which is classified as 150% malicious since it causes great harm and spreads malice like all blockers do. It

The Problem One of the most effective and dangerous ways to run malicious software on a victim’s computer is by exploiting vulnerabilities in popular applications or within the operating system.
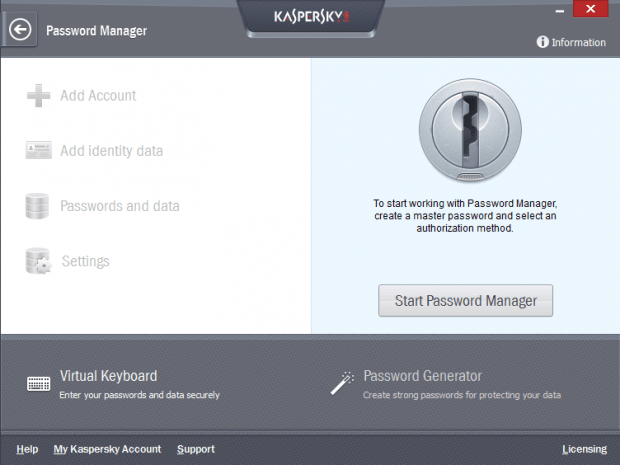
Passwords. They are a curse. However many of them you try remember, they are being forgotten. No matter how many of them you write down on paper they get lost.
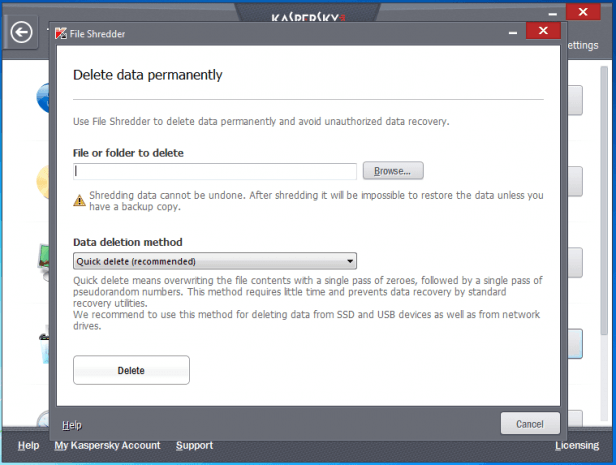
There is a joke about a note in a letter saying “Burn after reading.” It’s not the highest degree of secrecy. The best form of secrecy would be “Eat before
The Problem At present, even very small companies store information that could cause irreparable damage to their financial future if it fell into the wrong hands. An example of this
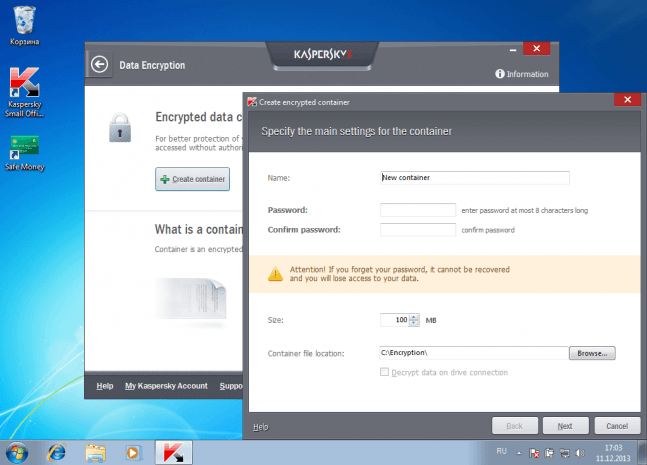
Sony Corp. underwent a large-scale fiasco in April 2011, when a security breach affected tens of millions of people. The intruders stole the personal data of many users along with
The Problem We often hear from small business owners that the modest size of their companies provides them with “invisibility protection”. Employees believe that their organization and its activities are
The bill for your company’s Internet access just made you grunt in annoyance. And you know exactly who to thank for it. The offender has repeatedly been addressed, but either