
Teach your SIEM to detect more threats
Using the Machine-Readable Threat Intelligence Platform fits well with our general position on security: multilayeredness everywhere.
446 articles

Using the Machine-Readable Threat Intelligence Platform fits well with our general position on security: multilayeredness everywhere.

Fantom ransomware displays a fake Windows Update screen while encrypting your files.

Some Android Trojans can write reviews and rate apps on behalf of users, but without their consent.

What lessons can businesses learn from the story of our investigation of the activity of the Lurk gang?

Powerful chatbots can replace real-life communication — and take over the world.

One Instagram post with a picture of a ticket can cost you a whole lot of time and money and ruin your day. This is how you can avoid it

Lynch law, loss of basic privacy, disgusting marketing, digital identity theft — how else can facial recognition be misused?

Short-term rental sites are great for travelers and homeowners. The Wi-fi? Maybe not so much.

Kaspersky Lab has patented technology that can disarm Adobe Flash exploits using special detection technology.

How to keep your money and data safe during the 2016 Olympics: All of the risks you need to know about, in one post.

Kaspersky Lab experts checked industrial control systems for vulnerabilities and found lots of them.

Ranscam deletes your files and then demands ransom to restore them, or it will delete them. Yes, in that order.

New ransomware called Satana encrypts your files and blocks the operating system from booting.
Any USB device can potentially be zombified and turned into a secret agent for cybercrooks. The world needed a shield against this threat, so we rolled up our sleeves and created one.

Once, hackers wrote malware just for the fun of it, but now Trojans are serious business. However, here are five modern, weird malware samples that may be funny and strange, but they are still very dangerous.

Have you ever received a letter from a Nigerian prince? A Nigerian astronaut? How about Daenerys Targaryen? If so, you know that we are talking about funny Nigerian spam — and this post covers it all!

Mobile ransomware is on the rise. We discuss the most popular ransomware families, speculate on some statistics, and suggest the best means of protection.

While we rest, cybercriminals work. Kaspersky Lab discusses the main risks for tourists and travelers on business trips.
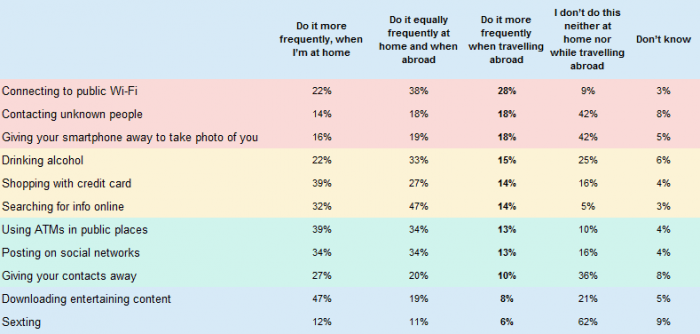
Our survey questioned consumers – 97% of whom had travelled to another country during the past 12 months – about their digital habits abroad. It found that in the world of work and leisure, we are a well-travelled lot, but we tend to leave our digital security at home.

Where ransomware originates, how blockers evolve into cryptors, and why this type of malware is cybercriminals’ favorite tool.

Do you have some long abandoned accounts? Do you use the same password everywhere? If so, change all of them now!