
Six Microsoft vulnerabilities being actively exploited
Microsoft’s March Patch Tuesday fixes several vulnerabilities that have already been used in the wild. Details are not clear at the moment, but it’s worth installing the patches ASAP.
22 articles

Microsoft’s March Patch Tuesday fixes several vulnerabilities that have already been used in the wild. Details are not clear at the moment, but it’s worth installing the patches ASAP.

Exploitation of vulnerability CVE-2024-43451 allows an attacker to steal an NTLMv2 hash with minimal interaction from the victim.

Someone is targeting security experts using an archive that allegedly contains an exploit for the regreSSHion vulnerability.

A new vulnerability allows remote attackers to gain root privileges on Linux servers. How easy is it for CVE-2024-6387 to be exploited – and how to prevent it

Mistakes commonly found in almost every large organization. What should the inforsec team look out for, and what protective measures should they take?

Some thoughts on what PC software patches should be prioritized and why.

Legacy systems continue to toil away in embedded solutions, medical equipment, and precision instruments. How can the respective security risks be mitigated?

After a hack, a company needs to improve security quickly and effectively. We outline the first steps to cyber-resilience.

July Microsoft Patch Tuesday: a collection of exploited vulnerabilities.

Attackers exploit four dangerous vulnerabilities in Microsoft Exchange to get a foothold in the corporate network.

Researchers at RSAC 2019 reported on the current vulnerability landscape and built a model that helps with effective patching strategy.

Since mid-October, several major software vendors have released a number of security announcements and updates, most of them serious or outward critical.

Google’s Android OS is a vulnerable system. Developers make it worse by not providing critical patches in time.
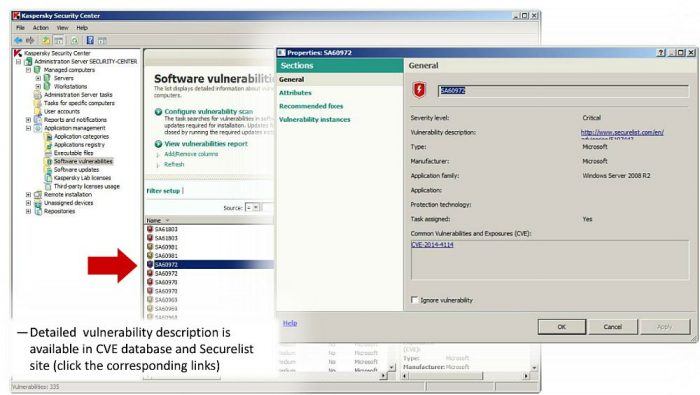
Kaspersky Security Center 10, the Kaspersky Lab’s unified management console, makes it easier to manage and secure all your endpoints – including physical, virtual and mobile devices.

One can find a number of reasons why this very bug cannot be patched right now, or this quarter, or, like, ever. Yet, the problem has to be solved.

A four year old Flash patch did not properly resolve a vulnerable Flex application, and attackers can exploit the bug, which is said to affect some 30 percent of Alexa’s top 10 most popular sites in the world, which threatens the integrity of the businesses behind these sites.
Today’s software packages have become so huge and complex that stacks of patches issued one after the other are increasingly common. This has consequences for system administrators.

Linux bugs may affect or directly threaten entire virtualization infrastructures: Whatever OS is used on VMs, an attack on a hypervisor is possible from both the outside and inside, and exploitation of the dreaded Shellshock vulnerability on Linux-based hypervisors is a possibility, too.

We’ve gathered information for patching the most common Linux distros against the notorious Shellshock Bash Bug. If you see we’ve missed something, please drop us a tip!

Making a case for password reuse, Google hiring hackers to fix the Internet, Apple bolsters security across its services with strong Crypto, plus various fixes and more.

The networking giant D-Link has acknowledged and committed to fixing a very serious backdoor vulnerability in a number of its older routers. The vulnerability was uncovered by security researcher Craig