
Secret code for Kaspersky Internet Security for Android: it’s your data
Kaspersky Internet Security for Android can protect data on your mobile from the long arms and sticky fingers of pocket thieves and cybercriminals
65 articles

Kaspersky Internet Security for Android can protect data on your mobile from the long arms and sticky fingers of pocket thieves and cybercriminals

Here are some simple yet effective ways to protect your files from infection by ransomware.

Sometimes even cybercriminals go fishing. They hunt for a special goldfish — our personal data. So, what can you do to protect yourself from phishing?


Criminals can use VoLTE to cause connection failure, subdue voice calls, or strip the victim’s mobile account of money.

Which brain mechanisms are in charge of our memory? Kaspersky Lab analyzed why we forget information stored on our devices.

Vitaly Kamluk answers our readers’ questions about his work with INTERPOL and other digital investigations.
The web service for secure password storage, LastPass, asks users to change their passwords ASAP.
While LTE networks are seemingly just now starting to take off, networking vendors and carriers are already fully engaged in a vivid discussion on 5G’s perspectives. What are those next-gen networks going to be and why do we need them at all?

There are many cool and funny projects in the world that deal with big data and we’ve gathered the Top 10 list of the most interesting ones. See for yourself!

“A single cyberincident can kill a business” may sound like an exaggeration, but it is not. In this blog post we prove it with two different stories.

Cryptolocker is still making the rounds, even though its peak seems to have passed. Or is it just an illusion? How does it affect businesses? Read some real stories and explanations in the new blogpost at Kaspersky Business.

A data access policy becomes an issue for any company as soon as it accumulates a considerable amount of valuable and sensitive data. That doesn’t mean the policy is always in place when it should be, or that it’s implemented properly.

A new poll shows Americans care overwhelmingly about digital privacy.

Tor is an online browsing portal that keeps your web activity completely anonymous.

Despite the fact that we have cheap unlimited Internet connection almost everywhere, there are situations when each megabyte is literally worth its weight in gold.

We hear a lot about so-called MITM attacks, but what is it in a nutshell? Let’s look at the “layman” explanation.

Big Data concept is the new “big thing” of the last two or three years. While it promises a lot of advantages, there are voices of doubt and reservation. This week we are publishing a series of blog posts dedicated to Big Data, trying to find out what this “big” is about. Stay tuned!

On the trail of Cabir’s “jubilee”, a new story about Nokia’s Symbian surfaced, involving stolen code, blackmail, charity donation, and a bag with several million euros. One day it could become a script for a criminal drama, but for now it is a story about sensitive data mishandling.

Having a chance to store as much as we want is a good thing, but is it bringing us more problems than advantages?
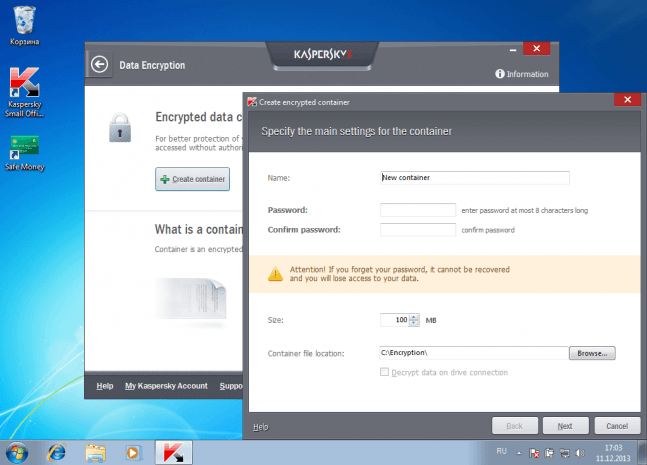
Sony Corp. underwent a large-scale fiasco in April 2011, when a security breach affected tens of millions of people. The intruders stole the personal data of many users along with