
How millions of Kia cars could be tracked
A vulnerability in Kia’s web portal made it possible to hack cars and track their owners. All you needed was the car’s VIN number or just its license plate number.
17 articles

A vulnerability in Kia’s web portal made it possible to hack cars and track their owners. All you needed was the car’s VIN number or just its license plate number.

Vehicle makers sell the data collected by connected cars about their users’ driving habits to data brokers – who resell it to insurance companies.

What personal information do modern cars collect about you, and how can you avoid surveillance or hacking of your vehicle?

After conducting a thorough study of applications for connected cars, our experts highlighted a number of flaws of such software.

Modern computerized car require a secure-by-design platform. And that’s just what we’ve come up with.

Longer product life cycles mean sustainability; shorter ones are easier in terms of support. Which should you choose?

This episode brings you stories of Amazon Alexa, a UK government BCC error, and so-called smart-car apps with hard-coded passwords.

Yachts are now Internet-friendly — and vulnerable because developers aren’t focusing on information security.

In this week’s edition of Kaspersky Lab’s podcast, Jeff and Dave discuss connected cars, an iPhone text bug, GDPR and more.

The largest motor show in the world is the best place to see what cars will look like in the near future.

Several months ago, our experts found a bunch of vulnerabilities in Android apps that allow users to control their cars remotely. What has changed since then?

With connected cars, it is vital to implement strong cybersecurity from the very start. Our experts stand ready to lend a hand.

Kaspersky Lab researchers disclose vulnerabilities in connected car apps.

What is the fundamental difference between Auto 2.0 and Auto 3.0? Technically, they’re the same. From the viewpoint of the car owner, however, the connection of one or more electronic units to the Internet provides pleasant and useful services — as well as Internet access while en route. But to a cybersecurity expert, the difference is huge: remote access to a car and its internal systems is bound to have major consequences.
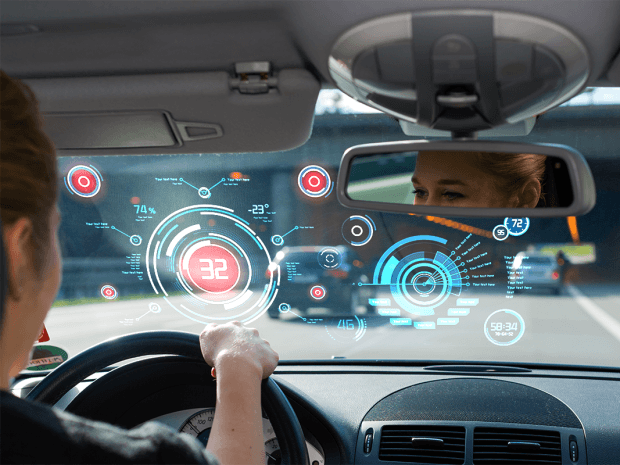
We are almost one and a half decades into the century of biometry and gesture controls, but our cars still have a steering wheel and two to three manual controls. Is this going to change?

New analysis pinpoints some weaknesses in a new generation of cars with online capabilities. If exploited, this may result in car theft and other problems.