Operation Daybreak: A brand-new zero-day exploit in Flash
Securelist just released a new cyberespionage campaign alert, code-named “Operation Daybreak.”
115 articles
Securelist just released a new cyberespionage campaign alert, code-named “Operation Daybreak.”
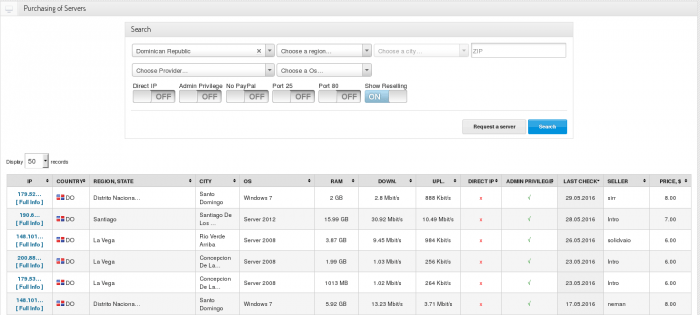
Kaspersky Lab has lately researched an active cybercriminal trading platform xDedic. The main purpose of the xDedic marketplace is to facilitate buying and selling credentials of more than 70,000 hacked servers from all around the world.
A vulnerability affecting all versions of Windows since Windows 2000 through Windows 10 might have been discovered. It’s still uncertain, however.

A new APT group is seen to have been exploiting hotpatching, a now-deprecated feature in Windows operating systems, to carry out their attacks.

Instead of writing their own malicious tools, criminals are increasingly using the off-the-shelf malware, and more and more often – totally legitimate software.

The vast majority of targeted attacks begin with simple steps; spear-phishing with malicious attachments or clickable links, or the infection of employees’ favorite websites (water-holing) to penetrate the security perimeter through the vulnerable browsers or other software. Don’t assume that because these methodologies are well-known, they are any less effective.

Kaspersky Lab launches two new enterprise solutions for preventing the most sophisticated cyberthreats organizations encounter worldwide.

Kaspersky Lab and partners reveal details of the joint investigation of the Lazarus group hazardous activity.

At The SAS 2016, Kaspersky Lab researchers discussed the newly discovered Poseidon Group. A custom APT boutique chasing commercially valuable data

Fraudsters portfolio updated: now they’ve learnt to steal money from banks directly. How did it happen?

Do you work with government or military contractors? Or are YOU the contractor? Then be warned: the Sofacy targeted attack actor has scaled up its activities – and may be

In their predictions for 2016, the GReAT team said that APTs will be replaced by deeper, embedded attacks that are harder to detect and trace back to the perpetrators.
In the fierce storm of active APT campaigns there is always something in motion. Researchers pin down and catalogue new threats all the time, but old names occasionally pop up,

In the new installment of our explosive hit series “Infosec news” you’ll find: the breach of Bugzilla, Carbanak is coming back and Turla uses Level-God hard to track techniques to hide servers.
Law enforcement agencies, with the help of leading IT security providers, are keen on blocking all the malware Command & Control servers they find. Sometimes, they efficiently shut down massive

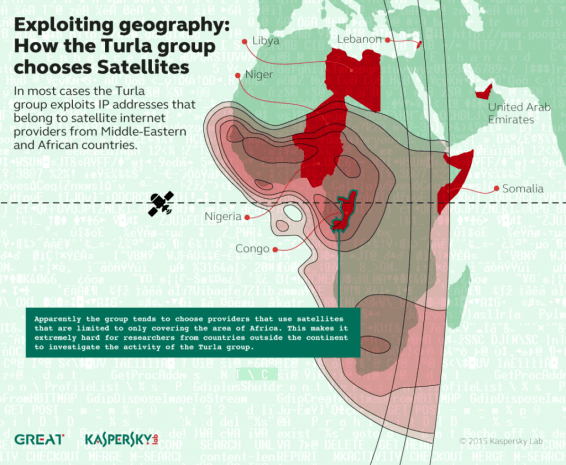
Kaspersky Lab’s researchers have found that Russian-speaking Turla APT group is exploiting satellites to mask its operation ant to hide command-and-control servers.

The BlueTermite APT campaign is rather new and extremely persistent. Here’s why.

These days, the propagation of zero-day exploits occurs almost literally at the speed of light. As soon as such useful exploit makes it to the public, APT authors can begin

Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Here are the details.

Minidionis is yet another backdoor from the same APT group responsible for CozyDuke, MiniDuke, and CosmicDuke – this time with some “cloud” capabilities.