The volley of major cybersecurity news keeps swooping down: Kaspersky Lab has discovered an active and proliferating APT codenamed Desert Falcons, apparently the first one to be developed and operated by native Arabic speakers; most of the targets are entities located in Middle East. The research on Desert Falcons was presented yesterday at Kaspersky Security Analyst Summit by our security expert Dmitry Bestuzhev.
Who are they?
Most likely, these are cybermercenaries gathering intelligence data. They use a very sophisticated array of tools and apparently are politically motivated, thus their operations could be state-sponsored. On the other hand, there are at least three campaigns targeting different types of victims known, and the attackers themselves are located in Palestine, Turkey and Egypt, which makes the theory that these campaigns are sponsored by a single specific nation state a bit dubious.
What do they do?
Desert Falcons attack military and government organizations, employees responsible for health organizations, combating money laundering, economic and financial institutions, leading media entities, research and educational institutions, energy and utilities providers, activists and political leaders, physical security companies, etc. A very broad and diverse range of targets, unified by the fact that they have access to possibly important geopolitical information in the regions they operate in.
Swooping down into the sands: Desert Falcons #APT
Tweet
There are more than 3,000 victims in 50+ countries. Most of them are found in Palestine, Egypt, Israel and Jordan, but others have been discovered in Saudi Arabia, the UAE, the US, South Korea, Morocco, Qatar and others.
How they do it?
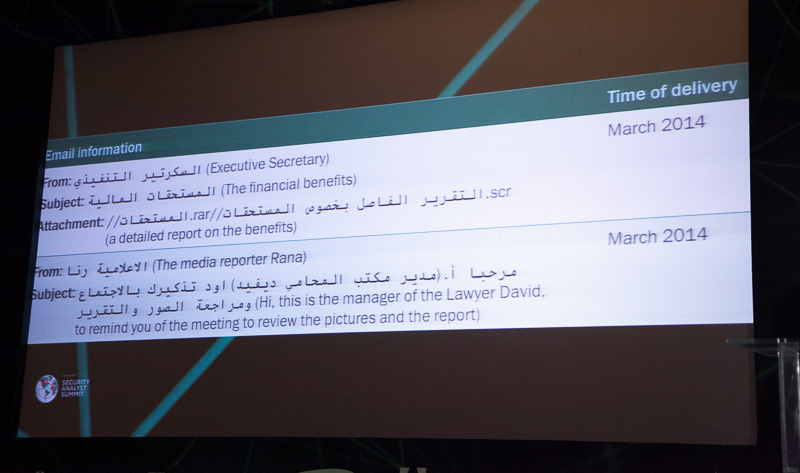
Malware writers use a variety of technical and social engineering methods to deliver their files and encourage victims to run them, creating an infection vector that’s quite effective, even though there are no methods involved that haven’t been seen before.
Among these – a fake website that promises to publish censored political information and asks users to download a plugin to view a video. Plugin is, of course, malware. Spear phishing emails (examples shown on a slide above) or social network messages are also used to deliver malicious files.
They use a handful of backdoors targeting both PC and Android devices. The scope of success is huge: so far more than 1 million files were stolen from victims, including diplomatic communications from embassies, military plans and documents, financial documents, VIP and Media contact lists and files. Files have been stolen from both hard drives and removeable media such as Flash or USB drives.
Still active
The operation is on the peak condition right now. The first operations date back to 2011, first infections – to 2013. We are yet to see, whether the attackers are bold enough to keep going after being discovered.
Kaspersky Lab’s products detect and block all variants of the malware used by Desert Falcons.
A detailed report is available at Securelist.
 FalconsAPT
FalconsAPT


 Tips
Tips