Merely 23 years ago Microsoft released Windows 3.1 operating system, Apple showed its first iPhone PDA, and Linus Torvalds released Linux under GNU license. Eugene Kaspersky published the book with a detailed description of next to all known at that time virii and methods of their removal, among them — by using the program known then as -V. The threat landscape then wasn’t a big deal: all virii could be described in a relatively small book, and even over the next couple of years it was quite relevant.
Those were good times. Now we have 325,000 new malware pieces arriving daily, and the industry on almost a weekly basis faces new proofs of system-wide security failures — from cars and skateboards to nuclear power plants. This is both bad and good at the same time: the more people who think of security of their data, business and their own lives, which is dependent on computers these days, the more chances are there things will turn to the better.
And now, lean back and relax, watch the things going on. Moving forward, each Monday we’re going to present the three most important news with extensive commentary and trolling. The stories will be hand-picked from Threatpost and Kaspersky Daily.
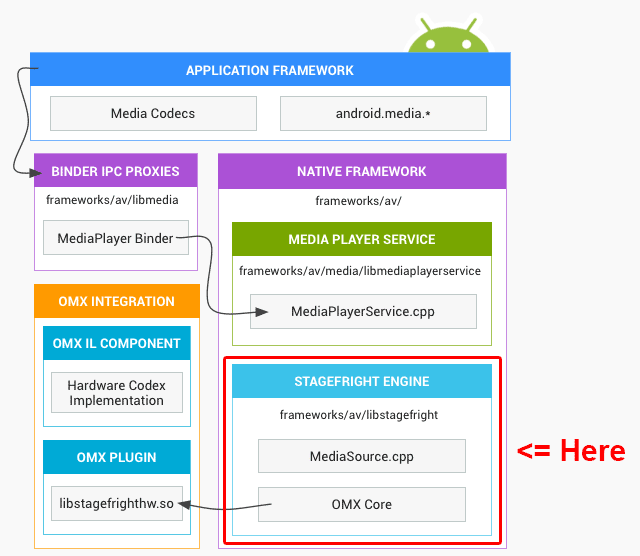
Stagefright: an Android flaw that hasn’t changed anything yet
The Threatpost story. Google’s feedback. CERT Advisory. The Kaspersky Daily advice on how to prevent infection.
Wired calls it one of the “worst Android vulnerabilities discovered to date,” but it is wrong: it can be worse. The main difference of this flaw from, say, Heartbleed and Shellshock, is that there was no need to invent a fancy name, Stagefright is an Android engine for audio and video playback, a part of Android Open Source Project. Technically, it is an entire set of vulnerabilities (the Zimperium experts who discovered this reserved seven IDs at CVE base), mostly related to buffer overflow.
The engine’s task is to play back various sounds and videos, and as ZDNet mentioned, it is tailored in a way to be ready to play the video “before you even think about watching it.” For some mysterious reason all these tasks are sometimes performed at “God” access level. The reasons, actually, are not too mysterious: it was easier to code it that way. Regardless, it was quite easy to escape the Android’s sandbox, prepared specifically for the tricks like these.
95% of #Android phones can be hacked with one just #MMS, millions at risk https://t.co/BJg5e7ss8N #infosec pic.twitter.com/DGBSkhQdDo
— Kaspersky (@kaspersky) August 4, 2015
As a result we have an illustrious proof of concept: send MMS to the phone – and gotcha. It’s not even necessary to open the “loaded” MMS: the phone will break itself since it is manufactured that way for the users’ convenience. Is it all so bad? Not exactly. First, in the Android 4.1 and later, Address Space Layout Randomization technology prevents the mess from happening, or at least “dismantles the problem” partially.
Second, following the rules of responsible vulnerabilities disclosure, Zimperium held back the exploit code. Although, thanks to the published patches, it’s all quite clear.
The Google’s reaction is interesting here. Here is the short summary of the relevant post from the official Android blog: “Everything’s fine. Our Sandbox is terrific. Only 0.15% of Android-based devices have the malicious app (lots of asterisks, fine prints and clauses go here). But in order for the things to be alright, Nexus devices will receive security updates monthly”.
‘Tis great, but what about all the rest Android-based smartphones and tablets? Google’s initiative doesn’t help with Android fragmentation problem, constant delays with updating of the newest devices to the latest OS versions and terminal non-updating the older hardware.
lol when ur Jeep gets updates faster than ur Android phone
— SwiftOnSecurity (@SwiftOnSecurity) July 27, 2015
Fortunately, HTC, Samsung, Sony, LG and a couple of other developers also claimed they are going to update their smartphones and tablets more often than before. Still, there’s lot of things remaining in the mist, all we know is that some devices will receive updates. Some day. Maybe. If we behave.
But anyway it is a good sign. Sooner or later Android will have an update mechanism similar to Microsoft’s Patch Tuesday. Just a year ago the same Adrian Ludwig, Android security chief at Google, said everything’s fine with security, all it takes is to fix Google Play a bit. So it is to say, Stagefright will bring on really useful changes. At least we hope and believe so. What else is there to do, after all?
Keep hacking the cars
The Threatpost story. The previous Threatpost story. The Kaspersky Daily report form Black Hat. And another report from DEF CON.
Last week we have a milestone event: the first-ever critical patch for the cars. Or, more specifically, for the Uconnect infotainment system used by Fiat Chrysler, which a) allowed for management of totally non-entertainment functions (specifically, it allowed to send the car into a ditch) and b) received the inbound connections via cellular networks. Can’t help reposting this:
WHY DOES A CAR EVEN HAVE INBOUND CONNECTIONS
WHY IS THE STEREO CONNECTED TO THE IGNITION
WHY DOES SOME IPHONE GUY HAVE TO POINT IT OUT
— SwiftOnSecurity (@SwiftOnSecurity) July 22, 2015
Ye. But this was last week. This week yet another flaw has been discovered, not so epic, but also quite an interesting one. Imagine you are in sunny Spain. Or in Bulgaria. Or in Greece, no matter. You leased a car, came to a beach and went swimming. As you do it, somebody could have stolen your car keys. In a normal situation this won’t help a thief much: try finding the car among the rest of them. But since your car is a leased one, it has its plate number on the keys.
#BlackHat 2015: The full story of how that Jeep was hacked https://t.co/y0d6k8UE4n #bhUSA pic.twitter.com/SWulPz4Et7
— Kaspersky (@kaspersky) August 7, 2015
In other words, use the hotel pool. Samy Kamkar, an independent security researcher, discovered that such a scenario is real if you use OnStar RemoteLink, which allows you to find the location and even remotely open the doors of GM’s cars. Kamkar was quick to build a miracle device, which can intercept the connections between the mobile app and the car itself, just by standing next to the owner.
It’s not as bad as it looks: the researcher says that the problem is with the app, not the cars themselves, and a simple update would fix the problem. Another thing is important here. Many are familiar with multimedia systems in the modern autos: they are almost like Android and iOS, they have touchscreen, sometimes internet access and various multimedia tricks. The problem is that they are way, way worse – slow, buggy and dull. I’d quote Wired again: compared to Android, automakers’ own multimedia systems “stink”.
Why? Because all these infotainment thingies evolve just too fast for the rather conservative automakers, and they lag behind. Fortunately, there’re exceptions.
Tesla Model S being hacked and patched blazing-fast https://t.co/ZuC0uzeKfn pic.twitter.com/al9naQnsbx
— Kaspersky (@kaspersky) August 10, 2015
The automotive industry also lags behind with security. For a security professional an Unconnect bug is no less than a total facepalm. Besides, doing something new, security is low on your concerns lists, because “insecure” coding is cheap and ease. And that’s where the attacks on oilpump starter begin. The relative isolation of auto technologies from the world of computers saved them so far, but in time it will become their weakest spot: they would be hacked where nobody expected, then there is no security, do what you will.
How to stop tracking and start enjoying life
The Threatpost story. EFF article.
Do Not Track mechanism is supported by all of the popular browsers, but unfortunately does not work. It was a good idea, actually: if you, users, don’t want the banner and social networks, Internet researchers and counters, Google, etc. to track you, check the box and enjoy your newly-gained privacy.
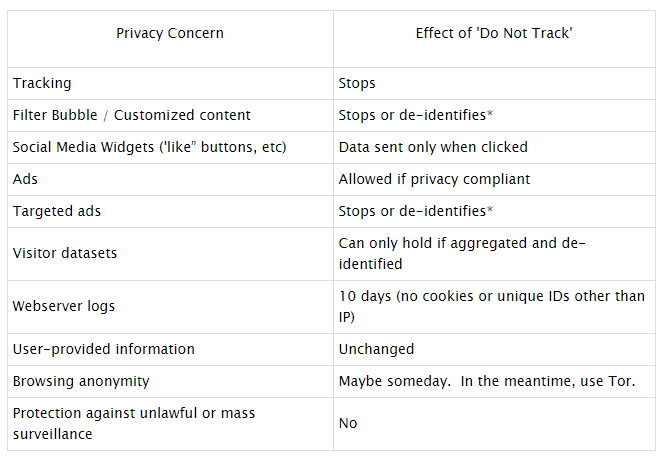
Yeah, forget it. The idea has been promoted for 10 years already, and it hasn’t moved on. Keep looking the ads of the goods you have already purchased, from the shop where you have bought them. The problem is that the industry can’t agree on practical use of Do Not Track and respect for the users who don’t want to be tracked.
Electronic Frontier Foundation sees the solution in a new standard that toughens up the do-not-track demands for the websites. For instance if you announce you follow the principle, don’t add the buttons from social networks who violate these principles. If you have a technical need to track the user’s activities (to purchase something, to authorize, etc.) – ask for permission.
New demands, however, remain voluntary, without control and enforcement. EFF relies on the fact that (in some countries) the violation of voluntarily taken obligations can lead to a lawsuit. But it’s not mandatory. So the new policies announcement says candidly: it can help with targeted ads, but in order to ensure a really anonymous web-surfing VPN and TOR are the only things useful.
The problem is further aggravated with the fact that most people don’t care, whether they are being watched or not. Do Not Track rules are debated by the small group of activists, outside of which users wouldn’t bother to check yet another box in settings. That’s wrong. And it’s not about big bad evil corporations willing to bulk-track you.
New technologies, such as Cortana voice assistant in Microsoft, or Google Now, or Apple’s Siri, in order to be of use, collect and process a ton of data on the device user, because it is necessary. Paranoids are hereby prohibited to read the Windows 10 Terms of Use, where all of these nuances are stated in a rigorous legal language. It is normal that our devices need to know a lot about us for our own convenience.
Security Week 32: #Android #Stagefright, new #car #hacks, Do Not Track 2.0 #privacy initiative
Tweet
But the more data about us companies collect, the more important is the work of those few, who seriously, without any zeal, wants to provide the possibility of limitations on data collection. Down to the necessary minimum.
What else?
Mac’s BIOS hacked. Not for the first time, though.
Some bad guys send out a ransomware instead of Windows 10 update.
A VPN service is discovered in China, which, aside from its own servers, uses the hacked PCs to bring the costs down for criminal activities.
Oldies
“Protect” malware family
Dangerous resident viruses, targeting .com and .exe files on execution. Intercept int 21h and int 1Ch or int 33h, depending on the version. Contain the string “File protection”. “Protect-1157” removes the files attributes and blocks down the mouse. “Protect-1355” announces itself on EGA and VGA displays with petty and extremely pesky flicker.
Quoted from “Computer viruses in MS-DOS” by Eugene Kaspersky, 1992.
Disclaimer: this column reflects only the personal opinion of the author. It may coincide with Kaspersky Lab position, or it may not. Depends on luck.
 car hacks
car hacks


 Tips
Tips