
Good security habits for everyone
Cyber-literate users possesses a variety of good habits, which protect them online and offline. What are these traits?
834 articles

Cyber-literate users possesses a variety of good habits, which protect them online and offline. What are these traits?

New variants of the “legendary” banking Trojan Carbanak are making the rounds on the Web, so far noticed in Europe and the United States.

In the new installment of our explosive hit series “Infosec news” you’ll find: the breach of Bugzilla, Carbanak is coming back and Turla uses Level-God hard to track techniques to hide servers.
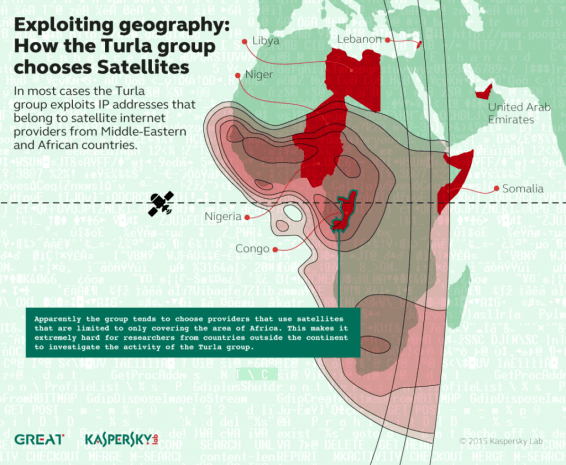
Law enforcement agencies, with the help of leading IT security providers, are keen on blocking all the malware Command & Control servers they find. Sometimes, they efficiently shut down massive

RAT stands for Remote Administration Tool. While it may sound rather innocuous, the term “RAT” is usually associated with the software used for criminal or malicious purposes.

Infosec digest: exploit kit Neutrino in Wordpress, yet another GitHub DDoS, Wyndham responsible for breach, while Target is not.

A year ago, an infamous leak which exposed some celebrities’ nude photos sparked the discussion around password safety. What can you do protect your accounts?
Kaspersky Lab has just released a new version of Kaspersky Endpoint Security for Mac, specifically for Mac-savvy businesses.

A look at what the “threat landscape” is comprised of for businesses.

These days, the propagation of zero-day exploits occurs almost literally at the speed of light. As soon as such useful exploit makes it to the public, APT authors can begin

Don’t be a slowpoke, follow Dr. House’s rule: everybody lies, especially on the Internet.

It’s not feasible to call a security solution, either for individual users or for businesses, “an antivirus.” There’s more than that.

Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Here are the details.

Apple patched a serious issue in its App Store and iTunes Store, which could have undermined many of the businesses working in this ecosystem.

Security experts often mention exploits as one of the most serious problems, although it’s not always clear why exploits are so special and scary. We’ll try to explain here.

Kaspersky Lab launches the new versions of its flagship products, designed with privacy concerns in mind.

Top-level IT security pros believe there’s a significant, unaddressed gap between enterprise security priorities and the serious threats that keep them awake at night.

Minidionis is yet another backdoor from the same APT group responsible for CozyDuke, MiniDuke, and CosmicDuke – this time with some “cloud” capabilities.

Private data of 37 million users are at risk after a huge data breach on the popular Ashley Madison dating site.

Exploits are a subset of malware, but they are not always detectable by security software if it doesn’t employ behavior analysis. In fact, it’s the only good way to beat exploits. Malware programs may be plentiful and varied, but most of them have similar behavioral patterns.

Attacking a broad spread of companies allows the group to access potentially valuable ‘bonus’ data from unexpected sources.