
Busted! Top prosecutions of July
July is over and that means it’s time to look back and observe the latest results of the battle between cybercriminals and prosecutors.
73 articles

July is over and that means it’s time to look back and observe the latest results of the battle between cybercriminals and prosecutors.

June was a busy month with hacks and data breaches, privacy, cryptography, and mobile security news, and an update on OpenSSL Heartbleed.

Enabling two-factor authentication makes it significantly harder for an attacker to compromise your online accounts, but what is it and when should you use it?

There was a lot of interesting news about hackers and other cybercriminals, so let’s see who has been busted in May.

May 2014 appears to be very stormy and volatile in regards to information security. Still overshadowed by Heartbleed and Windows XP “official demise” from April, it has brought a lot of troubles on its own.

The season seems to be open: The dust hasn’t yet settled after the Heartbleed semi-apocalyptic revelation, and now eBay has confirmed that its security had been badly breached, with service

eBay users will be forced to change their passwords because of a data breach that exposed encrypted user credentials.


Whether you’re a victim or a witness, there are a number of sources you can submit online threat information to in order to make the Internet a safer place.
A series of security tips and guidelines to follow if you are planning to conduct money transfers online.

There is a serious flaw called Heartbleed in OpenSSL encryption library that could expose user login credentials, communications content, an more

The criminals continue to do their bad business and law enforcement agencies successfully chase them down. That happens every month, so here are the most interesting cases from March. A

The biggest annual event in the mobile industry, Mobile World Congress, started yesterday in sunny Barcelona. From the beginning, it has brought some amazing and unexpected news that will likely

The story of Naoki Hiroshima and his single letter twitter handle underscores the importance of taking a holistic approach to Internet security and reiterates the reality that the security of
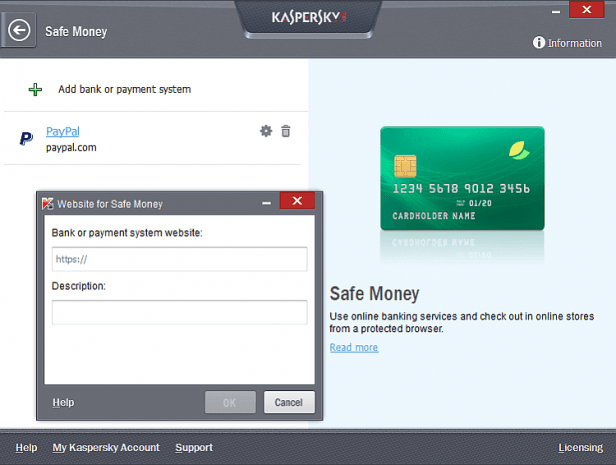
Online payments have remained one of the most vulnerable sections of the IT perimeter. Most banks and payment systems now have two-factor authentication. However, not all of them have instituted

Reports emerged earlier this week that the Starbucks’ iOS mobile application could be exposing the personal information of any customers that downloaded it. To their immense credit – especially considering

For many Americans, November invokes images of turkey, pie and time spent with family, but for a great deal of others this time of year also brings up something very

It’s a weird time for mobile payments. Years ago it was thought that by now some parts of the world would be well on their way to if not fully

Most people bought their first antivirus program to run on a single computer – but that was five, ten or even fifteen years ago. The world has changed, and our

Phishing is a dangerous type of Internet fraud that uses fake websites to swipe user logins and passwords to hijack their online accounts to steal money or spread spam and

Everyday life and online shopping are inseparable. One plastic card allows us to fulfill practically every whim from a pizza to a car, allows us to pay bills and transfer