
Ask the expert: Vitaly Kamluk answers questions about malware and security issues
Vitaly Kamluk answers our readers’ questions about malware counteraction and various security issues.
581 articles

Vitaly Kamluk answers our readers’ questions about malware counteraction and various security issues.

Attacking a broad spread of companies allows the group to access potentially valuable ‘bonus’ data from unexpected sources.

Hackers and cyberspies are not something you only see at the movies. The Internet is actually crawling with weirdos and criminals who are just looking for a chance to infect your smartphone or steal your gaming account.

Vitaly Kamluk answers our readers’ questions about his work with INTERPOL and other digital investigations.

In Q1 of 2015, the amount of spam in the world’s email traffic is less than it was a few years ago, but still too high. Junk mail goes from annoying to dangerous when infected by cybercriminals.

I was repeatedly asked the question: “Once you decide to become a cyborg, how would your current routine change?” Today I’m going to give you 10 answers to this question.

A serious zero-day has been disclosed in Unity Web Player. We provide a full breakdown of what it means and how you can protect yourself.

What do a billionaire inventor Elon Musk, the Google Now on Tap service, and the recent “Ex Machina” movie have in common? They all are about artificial intelligence.

How did you like it the last time you saw your friends? Did you have a nice chat with them? Or were you all only taking pictures of your meals to post them on Instagram and talking to each other on Facebook?

Kaspersky Lab experts detected a sly scheme that allows fraudsters to steal personal data without your login and password.

Kaspersky Lab has just publicized the discovery of a new cyber-espionage campaign. Unlike previous thresats, it’s targeting smaller entities – namely SMBs. That’s where it gets interesting.

Let’s imagine the things we would have to leave behind as a brand new world of driverless cars is evolving at a full speed (besides the enjoyment of driving itself)

Big data helps to catch child abusers, drug dealers, and terrorists, and allegedly it also helped to locate Bin Laden.

An annoying story of ‘free’ WiFi hotspots by St. Petersburg-based Smart WiFi. Nothing is for free, though, as you end up paying with your vk.com credentials

As cybercrime keeps focusing on profit, the share of plainly malicious spam, spreading out Trojans, phishing links, etc., will grow.

Major social networks have been known to either unbundle their functionality into multiple apps, or buy other apps and not integrate their functionality into the main one.

Connection inside the aircraft is not that complex: it needs just a Wi-Fi access point, end of story. But deploying the channel on the outside is a totally different and fascinating concept

Fraudsters hacked Skype and tricked people from a contact list to send them about $5,000 over the course of a few days. Skype support, local banks and the police refused to do anything.

#BionicManDiary Entry 003 – The one where I bypassed the smartphone’s password protection whereas had intended to do a completely different thing
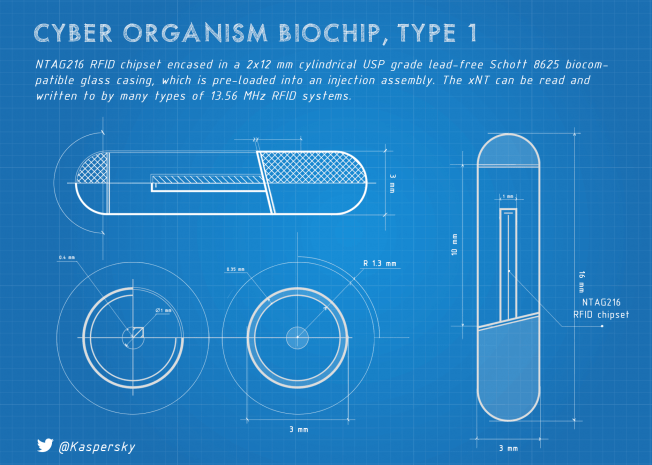
During my first two weeks of the biochip experience I had time to mull over a lot of things. In this post I’m going to touch upon the subject of form factor.

When it comes to Mobile OSes, every 3rd option conversation these days mentions the need for some “true openness”. But do we really need this kind of openness?