The owners of smartphones running Android and iOS sometimes enter into heated discussions as to whether it’s worthwhile to perform the mysterious procedures known as rooting and jailbreaking their devices. In effect, these are hacking activities with some interesting consequences. This article considers the pros and cons of these operations.
Despite the two different names, rooting and jailbreaking are essentially the same; the first term is used for Android devices and the second for iPhones. On a new smartphone, many operations are only available to software created by the manufacturer or the creator of the operating system; all programs downloaded from app stores have limited access rights. Rooting or Jailbreaking describes the acquisition of complete administrator rights on the device, allowing third-party programs to perform operations that were not originally available to them, such as controlling CPU clock speed or overwriting system files. With the help of specially created programs, the users can do everything on their smartphones without any restrictions from the manufacturer. Naturally, more power brings more responsibility: “absolutely everything” includes such extremes as bricking your smartphone or installing full-scale spyware.
Why bother with Jailbreaking/Rooting?
Let’s be frank: it’s estimated that between 50% and 90% of users opt to jailbreak or root their devices to enable them to install pirated games or apps without restriction. While I strongly disapprove of this practice, there are more respectable reasons to hack your own device.
Firstly, installing applications with administrator-level rights can give the smartphone previously unimagined functionalities. For example, there is an application that changes the ringtone volume depending on a number of conditions, such as the background noise level determined by the microphone, analysis of camera image and movement readings indicating that the device is in the user’s bag or pocket.
Secondly, it allows for flexible application management. Titanium Backup, a full-fledged, flexible “time machine” software program, is perhaps the most popular Android application that requires rooting. With this program, users can easily transfer data from an old smartphone to a new one,or restore an older version of an application if the new edition is unsatisfactory.
Thirdly, it can provide new security features. This section is, however, worth an entire chapter.
The Rooting/Jailbreaking process
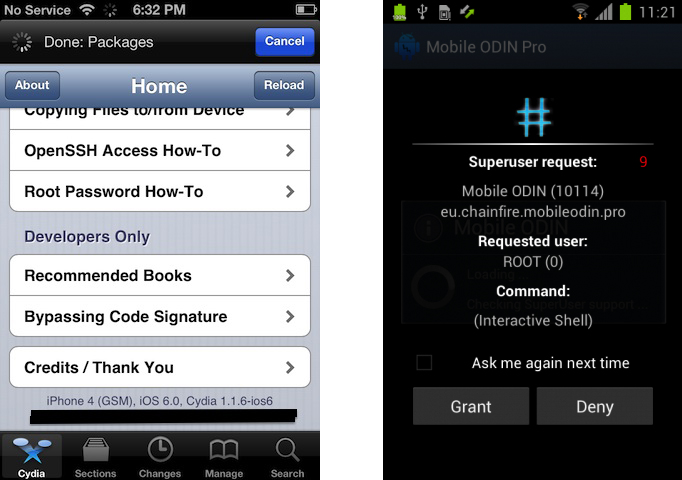
On an Android smartphone, administrator rights can be legitimately obtained with the manufacturer’s approval. Here is how this is typically done: users must type their smartphone’s unique number (IMEI) and download the necessary software. It will unlock the smartphone’s bootloader and enable the upload of a modified operating system that will grant a user’s full rights. Sound complicated? Indeed; this is why manufacturers void warranties on such unlocked smartphones and give them the status of “developer device.”
For this reason, users and enthusiastic attackers often follow a different path: they look for vulnerabilities in the smartphone’s firmware, through which they can obtain the same privileges without contacting the manufacturer. This is very similar to a malware program exploiting vulnerabilities on your web browser so it can automatically install itself on your computer without your knowledge or consent. To have your smartphone rooted using this type of vulnerability, you need either to connect it to a computer using a USB cable and launch an application on the computer, or start the program on the phone. In a few minutes’ time, your phone will be rooted, and you will not have to repeat this procedure in the future.
Jailbreaking an iPhone/iPad is also based on exploiting vulnerabilities. Typically, jailbreaking is performed by connecting the iPhone to a computer and running a program on the computer; however, there are easier ways to jailbreak older devices. Some time ago, there was an enormously popular website, Jailbreakme, which exploited a vulnerability in the Safari browser. With this site, users could gain full privileges on their iPhone/iPad with a single click by accessing this website from the device and clicking on the “Jailbreak me” button. Later on, Apple patched this breach and hired the site’s developer. Prudence pays, it seems.
The main consequence of performing a root/jailbreak is the installation of additional management programs, which offer new functional capabilities. For iOS, the “gold medal” is the emergence of Cydia, an alternative app store; for Android, the proof of success is the emergence of the SU or SuperSU application. The latter manages administrative access – it prompts the user to permit or deny access to a specific application.
Security Benefits from Rooting/Jailbreaking
Applications using administrative functions are capable of protecting the user’s smartphone or Tablet in fundamentally new ways. For instance, a standard Android smartphone lacks a firewall; to put it more accurately, the firewall is integrated into the system, allowing anybody to do anything and is completely unmanageable. Only an application with root status can enforce new firewall rules, e.g. by blocking network access to certain applications while roaming.
In the most recent versions of iOS, a system exists that allows flexible management of the data access granted to applications: each application is granted access to specific types of personal data, such as photos, contacts, locations, etc. In Android, a similar permission system exists, but users do not have flexible management capabilities: they see the entire list of permissions prior to installation. If they do not like something about it, they can reject the installation. This situation could be improved with applications that would flexibly manage permissions for installed applications on a case-by-case basis. In other words, you could strip a program of the right to determine your location, for example, if you think it should not have it.
Under both iOS and Android, applications with administrative rights can have extra anti-theft capabilities. For example, in iOS there are anti-theft applications that take pictures of the suspected thief while displaying a lock screen; in Android, there are programs that write themselves into the device’s ROM and can survive a factory reset. Naturally, one should remember that these have not been tested by the manufacturer and may behave in unpredictable ways, draining the battery or even rendering the smartphone utterly unusable. Because of this risk, most application developers, Kaspersky Lab with its Kaspersky Mobile Security included, do not use functions that require rooting/jailbreaking.
Security risks of Rooting/Jailbreaking
Many applications consider rooting/jailbreaking to be a security threat, and refuse to run on an unlocked device. Many MDM (Mobile Device Management)-class applications are like this – these applications help review working documents and email on a private smartphone. Mobile applications from some banks also disable most of their features on an unlocked device. These decisions come as little surprise, though.
Apart from the above-mentioned risk of turning a smartphone into a lifeless piece of plastic, rooting and jailbreaking present new security threats.
Firstly, an application that has obtained administrative rights comes out of the application “sandbox,” so its declared features and granted permissions are no longer relevant. It will be able to do everything it wishes, including reading and sending files associated with other applications, watching the device’s owner, using the microphone without the owner’s knowledge, etc.
Secondly, applications for rooted or jailbroken smartphones are typically created by small amateur groups, so they are very likely to contain sloppy code with its own vulnerabilities. That vulnerability could be exploited by a seemingly-legitimate app, handing over administrative rights of the phone.
Thirdly, a number of changes introduced into the phone’s configuration during rooting/jailbreaking may be a gift for a hacker: jailbreaking makes most iPhone models remotely controllable, since the same password is valid for all devices. Naturally, the password can be changed, but very few users do so.
Your Safety is Not Guaranteed
Rooting/jailbreaking has very serious security implications, but keeping away from such practices does not guarantee your security. Attackers can take advantage of a vulnerability on your smartphone and obtain administrative rights for their malicious application without using intermediary programs like SuperSU. In this case, there is little difference between intact or unlocked devices. The above-mentioned site Jailbreakme.com is a vivid example. If that site’s creator had been a villain, he would have abused that vulnerability. Instead of offering free jailbreaking for all, he might have, for example, surreptitiously installed spyware. Another intriguing site, offering some kind of cyber-miracle like reading other users’ messages, could put up the same “click here” button … and the wicked work is done! So far we are unaware of such cases, but we cannot ignore the possibility that cybercriminals are using these very schemes, at least for targeted attacks.
There is another, more immediate difference between intact and rooted/jailbroken smartphones. An unlocked device is typically stripped of all warranties, so nearly all future problems will have to be settled at the user’s expense. It is your decision whether it is worth doing or not. But regardless of your decision, additional security, such as Kaspersky Mobile Security, will never hurt.
 jailbreaking
jailbreaking

 Tips
Tips