You might think a ransomware-infected ATM, a timetable showing an extortionist’s message at the airport, or a slot machine demanding a ransom in bitcoins would be the stuff of urban legend. Nevertheless, people observed all those things during the WannaCry ransomware epidemic three years ago. Therefore, today, Anti-Ransomware Day, seems like an opportune time to reminisce about those peculiar cases.
Who would even think of infecting a payment terminal with ransomware? What could the payoff possibly be? The truth is that the creators of WannaCry did not choose explicit targets for their malware. It entered the network through ordinary personal computers and infected every device that it could reach through an unpatched vulnerability in the SMB protocol. That means the ransomware infected quite a few devices that did not — could not — contain data valuable enough to ransom. The devices were collateral damage.
Many other types of malware are similar but missing WannaCry’s convenient spreading mechanism, but the creators of those other cryptors do share a lack of consideration in targets. So, sometimes devices that pose no financial gain for attackers still fall victim to ransomware. Today’s roundup of the most unusual devices that have been infected by ransomware shows you how random the victims of such attacks can be.
1. Medical equipment
The photo published on Forbes shows the screen of a medical device that is used to improve the quality of the image obtained from an MRI machine and tracks the flow of the contrast agent to the patient. There is no need to explain how important it is to provide a timely diagnosis for a patient using magnetic resonance imaging. And what if such a device were sabotaged right in the middle of a procedure?
2. Traffic cameras
Cyberattacks have hit the cameras that record traffic violations since long before the WannaСry epidemic. But usually it was about illegal access or sabotage. However, 590 drivers in the Australian state of Victoria can thank malware for saving them from having to pay fines. According to ITNews, the infected cameras remained fully operational. The police simply did not collect fines using that particular evidence because the moving violations were recorded by compromised devices.
3. ATMs
WannaCry hit ATMs all around the world. Reinstalling the operating system restored infected ATMs, but doing so takes time, especially in cases of mass infection. What is more, these devices are usually connected to the same network and have the same protection, so if it fails for one, it fails for all. Although the cash stored inside the ATMs was in no danger, many banks had to work hard to rebuild their ATM networks — not to mention their damaged reputations.
4. Arrival and departure screens
WannaCry even hit some arrival and departure screens in airports and railway stations. It is unlikely that anyone would pay a ransom here — absolutely no valuable information is stored in those devices. Nevertheless, it costs both time and money to restore such a board. Nonfunctioning screens at train stations and airports can also cause passengers a lot of trouble. And if passengers are unable to get to their destination on time because of malware, whom will they hold liable?
5. Outdoor advertising signs
Billboards also fell victim to ransomware. Looking past the sarcastic remarks from passersby and the annoyance of those sent out to repair or replace the displays, the main victims were advertisers, which suffered significant losses of reputation. After all, they are paid to display their clients’ videos or ads, and screens stuck showing ransomware messages violate customer contracts. Such problems can also discourage companies from continuing to use the services of the affected advertising firm.
6. Parking payment terminals
Consider returning to a parking garage only to see a ransom demand on the payment terminal. Now you can’t pay for your parking, which means that the gate arm will not rise when you try to exit the garage. But the main victim here, of course, is the parking garage operator. Everyone who is now unable to park in the garage or leave the facility in a timely manner will be angry at the company.
7. Ticket machines
Ticket vending machines were also infected. For example, in San Francisco, ticket machines for the BART subway system remained out of order for two days as a result of a Mamba ransomware attack. The attackers demanded $73,000 from the rapid transit operator. However, the injured party (rightly) refused to pay the ransom, and as a result, the San Francisco Municipal Transportation Agency was forced to give out free subway tickets until the machines could be repaired.
Practical takeaways
The devices unintentionally infected with ransomware were hit largely because their operators saw no need to install up-to-date protective solutions and to update their operating systems in a timely manner. As we’ve seen in practice, many people don’t know that these types of equipment are just computers, that they tend to run some variety of Windows, and that they exhibit the vulnerabilities of their OS family.
Therefore, if your company uses this kind of equipment, then we have the following recommendations for you:
- Move those machines to a separate subnet to isolate them from other computers;
- Install operating system patches in a timely fashion;
- Install appropriate protective solutions.
In fact, our lineup includes specialized protection for these types of devices: Kaspersky Embedded Systems Security protects even low-power embedded computers of the kind frequently found in ATMs, payment terminals, and other similar devices.
 Ransomware
Ransomware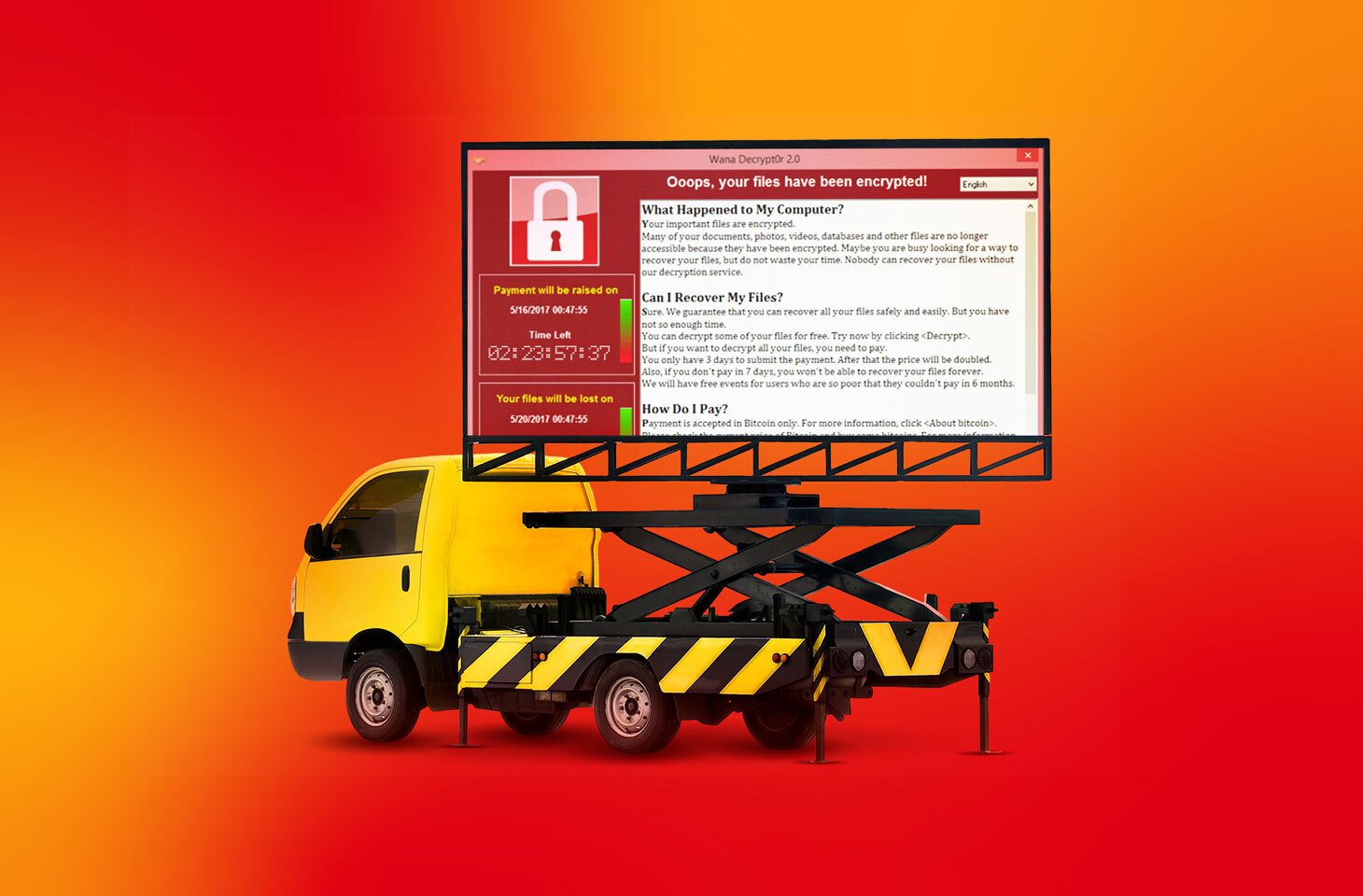


 Tips
Tips