Less than three months after Pokémon Go launched, criminals sneaked malware into Google Play to target Pokémon trainers. Our experts discovered the Trojan several days ago and immediately reported it to Google. Unfortunately, by that time, the malicious app called Guide for Pokémon Go had already been downloaded more than 500,000 times.
In the past few months almost 6 million people gave Pokémon Go a try. It’s no wonder that the massively popular game quickly caught the attention of cybercriminals: The first malware for Pokémon Go was traced in July, soon after the launch of the game. At that time, the situation was not so dangerous. The Trojan was stored in a malicious file vault and waited to be spread online. But now we have quite a different story.
This new Trojan was discovered on Google Play. Like a professional rogue, it masterfully hid itself from security experts and chose victims carefully. To those “chosen” ones, it showed ads — a lot of ads. It also rooted their devices and installed a bunch of other malicious files and unwanted apps.
How does it work?
To hide the malware from antivirus scanners, the Trojan’s executable files were compressed with a commercial software packer. Decompressed files included useful Pokémon Go content (the Trojan’s disguise) and a small module with obfuscated code.
After a user installed Guide for Pokémon Go, the malware waited silently for some time. This break was quite deliberate: The malware needed to learn whether it was on a real device or a virtual machine — an emulated computer system security experts use to check how suspicious apps behave in different conditions.
Having confirmed it was on a real device, the Trojan sent a message to a command-and-control server run by cybercriminals. The report included information about the infected device: model, OS version, country, default language, and more.
The server analyzed the information, decided if the victim suited its needs, and informed the Trojan of its decision. With the server’s permission, Guide for Pokémon Go downloaded additional malicious files (their code also obfuscated). These files were the Trojan’s heavy weaponry; they let it use a number of vulnerabilities discovered from 2012 to 2015.
The armed malware rooted the system, silently installed additional apps, and flooded the phone with ads.
Just ads? Is that really dangerous?
Advertisements are rarely pleasant. Besides, it’s one thing to watch ads from Google — that’s one way you pay for its “free” services. It’s quite another thing when criminals infect your phone with malware to display banners all the time.
However, the worst part of this infection is hidden: Guide for Pokémon Go can secretly install any apps on your device. For now, criminals have chosen a relatively mild way to earn money: ads. Tomorrow, they may decide to increase their income by locking your device and demanding ransom — or stealing money from your bank account.
Why you shouldn’t trust the reviews and ratings on #Google Play https://t.co/aMdYbh3T1F pic.twitter.com/n8QmQtAElm
— Eugene Kaspersky (@e_kaspersky) September 1, 2016
Though the Trojan has been removed from Google Play, half a million people downloaded it. We know for sure that the Trojan infected devices in Russia, India, and Indonesia. But it targets users from English-speaking regions as well, and there are certainly more victims around the world.
How to protect yourself
If you are concerned that your device might be infected with this Trojan, remove the malicious app and scan your device with Kaspersky Antivirus & Security for Android. It’s free. Our security solutions detect the Trojan as HEUR:Trojan.AndroidOS.Ztorg.ad.
While you catch #pokemons, cybercriminals try to catch you on #GooglePlay
Tweet
To protect yourself in the future, follow these rules:
1. Keep in mind that even if you download apps only from official stores, nothing is 100% secure. Criminals sometimes bypass the protections of Google and other companies — Guide for Pokémon Go is a good example.
2. Promptly install security patches on your smartphone (and your computer, too). Cybercriminals pounce on vulnerabilities in both mobile and desktop OSes.
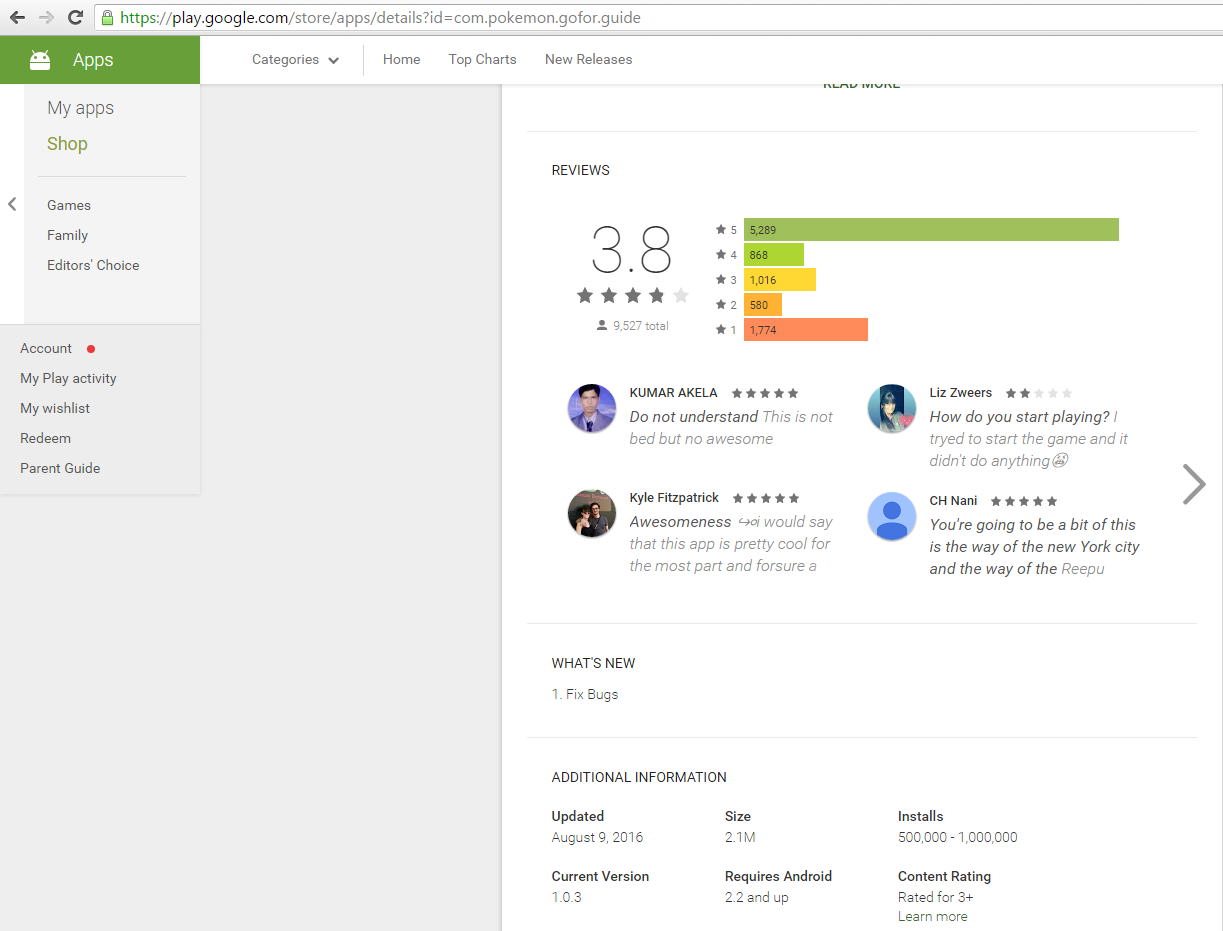
3. Remember that reviews and ratings on Google Play are not necessarily reliable — criminals can fake them using special malware. For example, Guide for Pokémon Go malware had four stars on Google Play.
 Android
Android