Kaspersky Lab’s security experts have published the first part of a new study of large scale cyber espionage campaign, called NetTraveler, which aimed at 350 large commercial and government organizations in 40 countries.
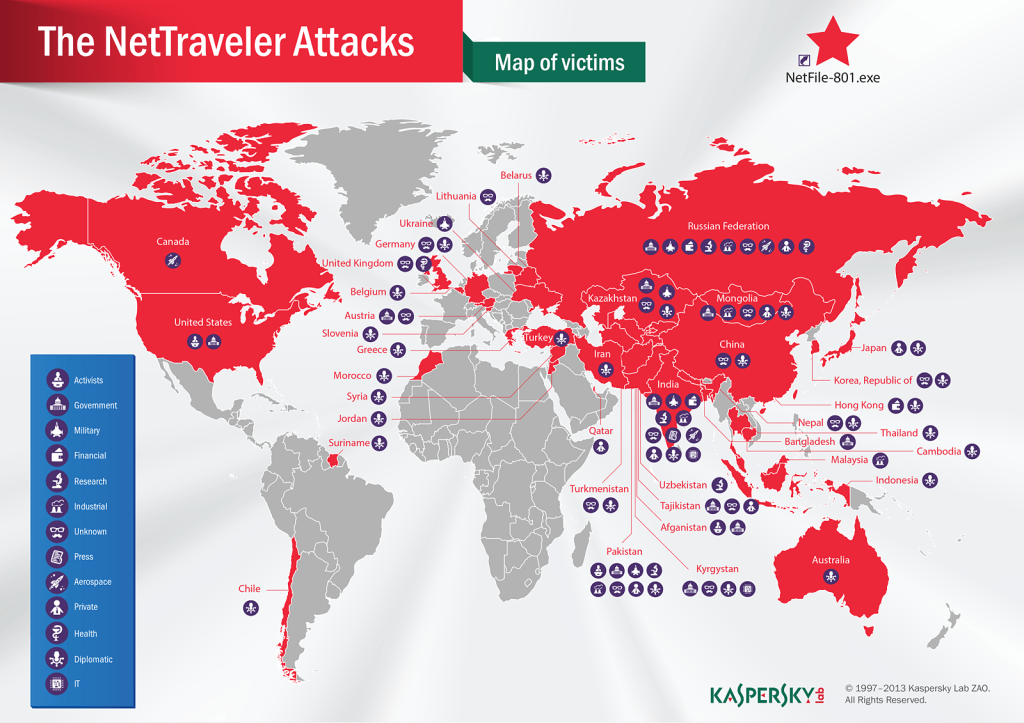
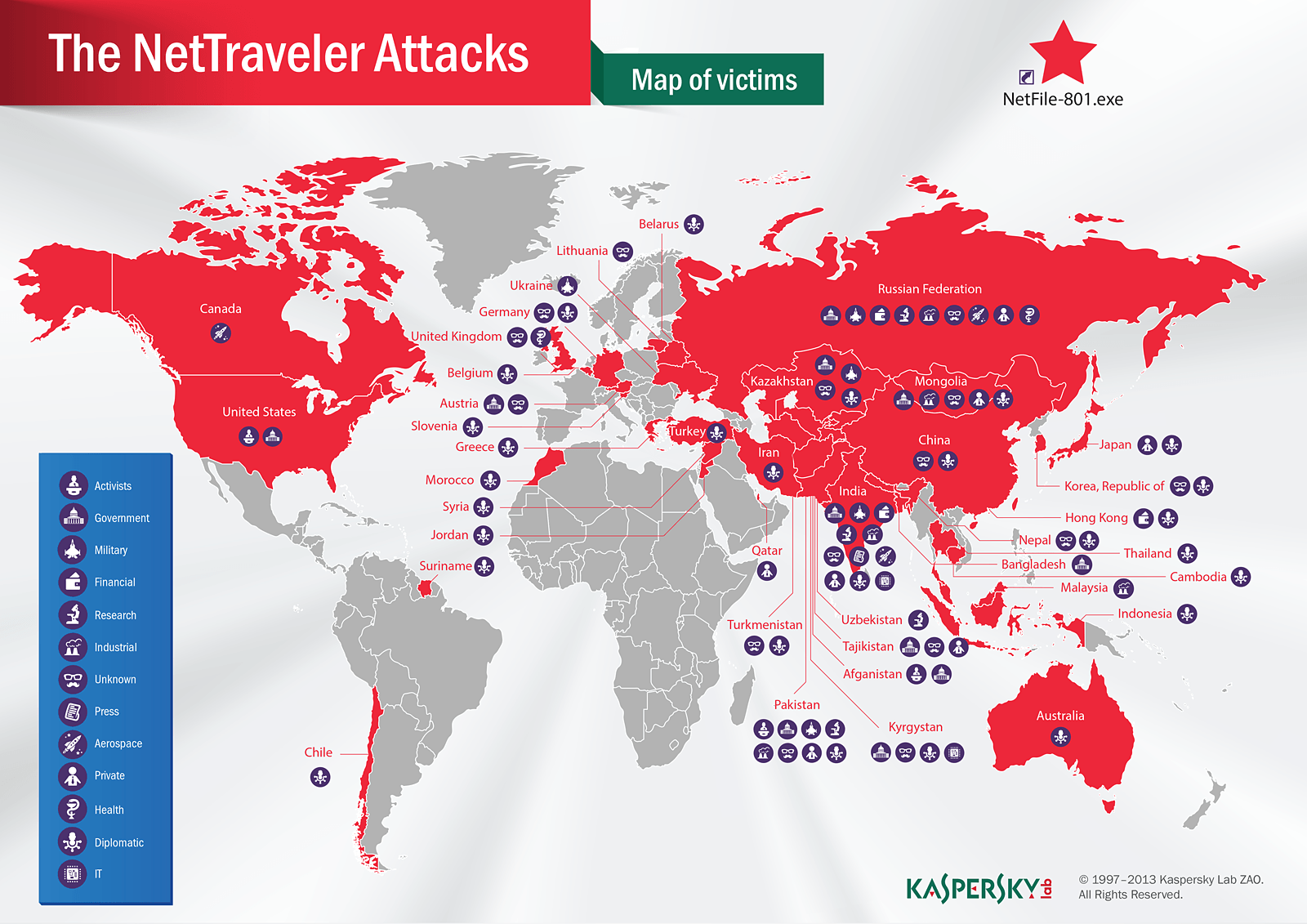
We observed the largest number of infections in Mongolia, which is closely followed by India and Russia. Among other targets there were Kazakhstan, China, Tajikistan, South Korea, Thailand, Hong Kong, Japan, the Middle East, Canada, United Kingdom, United States, Ukraine, Belarus, Lithuania and other countries. The map below shows almost all Asian countries under attack with almost unaffected Africa and South America.
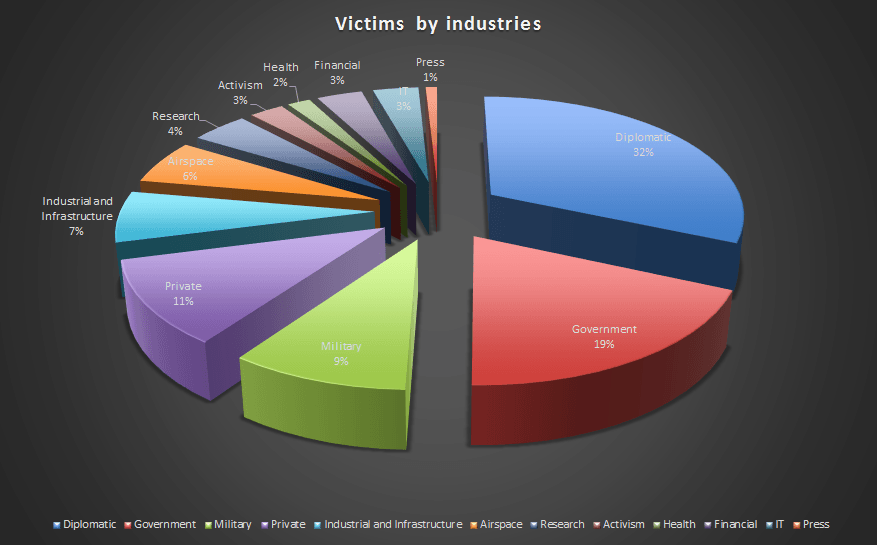
The objects of attack are quite varied, but for the most part those are very large structures, most notably, government and diplomatic institutions, representatives of oil and gas industries, defense contractors and civil society activists. Organizers of the attacks have recently focused on space research laboratories, nanotechnology and energy production companies, nuclear power plants, medicine equipment producers and laser and communications technologies companies. All in all, we are talking about the front line scientific trends. The information there has particular value and costs a great deal of money.
The title NetTraveler was taken from the phrase “NetTraveler Is Running”, present in the code of the earlier versions of the malicious program, which the organizers of this espionage campaign used as their main tool. The English phrase though does not imply that the authors of the code use the English as their mother tongue. The analysis showed that the majority of the organizers of this campaign are Chinese, and they speak English on the “working” level. Our experts say the group consists of about 50 people.
The earliest versions of NetTraveler were found in 2005. However, there is a reason to believe that the first version appeared as early as 2004, therefore, the operation has been going on for nearly nine years. Most of the samples were discovered in 2010-2013, now that the operation has gained the most momentum. The main way of distributing spyware are targeted attacks – phishing messages with attached MS Office documents, which when opened use exploits for old vulnerabilities CVE-2012-0158 and CVE-2010-3333 (these were eliminated in updated versions).
The attackers were mostly interested in files on hard drives, keyboard logging data, various types of documents (. doc,. xls,. ppt,. pdf) and other private information. The data have been leaking for years: we estimate the total amount of information stored with NetTraveler control servers as more than 22 gigabytes. It is worth noting that the attackers did not use the zero day vulnerability, rootkits or any other advanced methods of penetration. Thus it is surprising that such primitive methods have proven so effective. Apparently, the companies and organizations detrimented by NetTraveler either had no means of protecting information at all or they implemented a very weak type of defense.
It should be mentioned that this is the third – after Winnti and Red October – global cyber espionage operation, registered by Kaspersky Lab this year. Winnti was also conspired by a Chinese hacker group, though they used much more advanced tools for their infringement than the authors of NetTraveler.
It should be added that in a recent study we identified six organizations harmed by both NetTraveler and Red October. It does not mean that the organizers of both campaigns have anything in common; they are rather just interested in the same information.
Full report on NetTraveler is available at Securelist.com.
 NetTraveler
NetTraveler