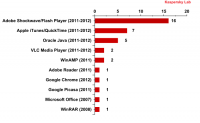
The gap in the fence: the most popular software is the most vulnerable
Imagine the following situation: there is huge disbursement of emails with innocent looking MS Word document attachments sent to the mailboxes of a company’s employees. Some of these employees have … Continue reading The gap in the fence: the most popular software is the most vulnerable