Kaspersky Lab has rolled out a new cyberthreats report covering Q2, and together with B2B International, a new survey: “Consumer security risks.” While it is consumer-oriented, certain findings therein, together with the findings from Q2 report are – unfortunately – extremely relevant to business.
Malware growth
The Q2 report says 291,800 new mobile malware programs emerged since mid-spring through June. This number is almost thrice greater than the relevant figure in Q1. Also, there were 1 million mobile malware installation packages in Q2, which is seven times greater than in Q1.
#Mobile issues of the end users and their relevance to businesses #protectmybiz
Tweet
Mobile banking is the primary target. Kaspersky Lab’s Q1 2015 report mentioned Trojan-SMS.AndroidOS.OpFake.cc, which was capable of attacking no less than 29 banking and financial applications. The Trojan’s latest version that emerged in Q2 is capable of attacking 114 (four times more) banking and financial applications. Its main goal is to steal the user’s login credentials with which to attack, among others, several popular email applications.
The complete text of the Q2 report is available at Securelist.com.
Now, the survey
The survey‘s main (bitter) finding is that around half of the consumers surveyed also use their personal devices for work. At the same time, only one in ten is seriously concerned about keeping work information safe should cybercriminals gain access to their devices.
According to the survey, 36% of respondents store work files on them, and 34% keep work-related email messages. Sometimes, more confidential information can also be found on users’ personal devices, such as passwords to corporate email accounts (18%), networks or VPNs (11%).
Below is the chart from the survey itself, showing what is being stored on consumer mobiles:
Why is it at all relevant to business?
Perhaps needless to say, but information such as passwords to corporate resources represents a valuable prize for cybercriminals hunting for corporate secrets.
While BYOD is convenient for the users – and to a large degree is necessary to businesses too – for various reasons, it also can be “the weakest link in the chain”. The main reason, though, is the carelessness of the end-users, as shown by the survey. Users bring their habits from home to work. Becoming part of the company infrastructure, mobiles also become the potential entry points of choice for the attackers. As one in ten users care about protecting their device, nine of ten are potentially exposed to a security breach and data loss – working files and access credentials included. The ensuing problems would definitely overshadow any kind of convenience.
BYOD integration should be regarded as a specific project, especially in large companies #enterprisesec
Tweet
BYOD isn’t going away
Despite all of these risks and the certain undermaturization, BYOD is an established business practice, so it is by no means going away any time soon.
There are certain recommendations that Kaspersky Lab experts can offer therewith:
- BYOD integration should be regarded as a specific project; this is especially true for large businesses. Every last detail of the integration process should be designed beforehand; and this should ideally include an infrastructure audit, a design stage, and a pilot implementation.
- To effectively protect mobile devices, it is important to use a comprehensive solution that ensures security across the entire corporate network, not one that focuses only on mobile devices. Without this, compatibility problems may arise and create extra work for system administrators.
- Managing mobile devices in a large business requires additional skills over and above those demanded by routine system administration. It is worth ensuring there are appropriately qualified IT security specialists on the team. These can provide centralized management for all mobile devices within the corporate network, ensure that all mobile applications are installed, removed and/or updated via dedicated corporate portals, and regulate data access levels and employee privileges.
- Most importantly, the business needs to develop robust scenarios for how to remove personal devices from the corporate network if they are lost or stolen, or if an employee leaves the company. A procedure should be developed to remove confidential corporate data from these devices and block access to the corporate network.
Specifically, to ensure the security of the mobiles (and, in certain cases, from mobiles too), Kaspersky Lab offers Kaspersky Mobile Security, a BYOD protection solution.
It ensures the protection of corporate information on users’ devices, helps to manage mobile applications and devices, protects users from malware and other cyberthreats, and allows for remote management of devices if they are lost or stolen. Kaspersky Security for Mobile is a component of Kaspersky Endpoint Security for Business, and is managed from a single console alongside other security solutions provided by Kaspersky Lab. More data on this suite is available here.
 BYOD
BYOD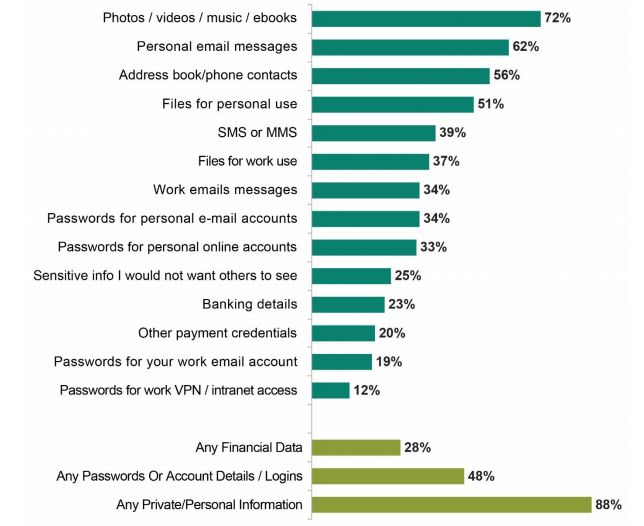

 Tips
Tips