88% of tablet users and 96% of smartphone owners use personal devices to store important personal information. These figures are from the survey B2B International and Kaspersky Lab cooperatively conducted in July 2013. In this study, “personal information” is defined as any data significant to the user; purely personal or corporate.
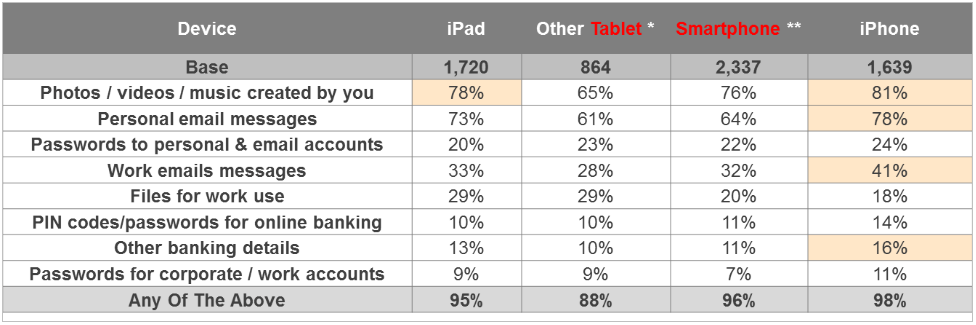
It’s the corporate data that can cause issues, however. Let’s take a look at the table below:
Here we see that a third of iPad users, 28% of other tablets users (the vast majority, over 80%, use OS Android devices), 41% of iPhone users and 32% of other smartphones users (most using Android devices), read work emails on their personal devices. A comparable number of people store corporate files on personal devices as well.
Purely personal information is stored on personal devices twice as often, which is logical. It has become increasingly normal, however, for people to bring personal gadgets to work.
The boundary between corporate and personal devices used to be quite distinctive. Now though, the line is being increasingly blurred. Firstly, no one purchases two different smartphones or tablets for work and home use, and the above table clearly shows employees’ “home” devices are being used for working needs as well, storing critical data including corporate information on personal smartphones and tablets.
Moreover, smartphone and tablet owners often actively use the devices, even simultaneously, with their home computers. And when this is the case, it’s not unlikely for an employee to bring his or her favorite toys to work and run them the same way they are used at home, from personal mailing to shopping and gaming (when there is time).
At the same time, most people ignore using basic means to protect their personal devices: only 40% of smartphone users and 42% of tablet owners have any security software installed.
The fact that about a third of mobile device owners use them for business purposes nowadays is seriously concerning. The boundary between corporate and home devices may be blurring, but the line between corporate and personal data has to remain as distinct as possible. Corporate data leaks should not be allowed. At least 14% of the respondents in the survey said they’d lost their devices or had them stolen or damaged, and data had been lost.
The survey shows though, that only 14% of companies fully applied the security policy to user devices. Moreover, the interviewed representatives of IT departments admitted their executives are very reluctant to reserve the funds for BYOD security. They tend to understand the seriousness of the problem only after actual leaks occur, which the company has been unable, or rather unwilling, to prevent. Basic BYOD security, including the encryption and isolation of corporate data, the option to remotely delete data in case of the device being lost or stolen, restrictions for potentially unsafe devices and applications within the corporate network and other security measures have long been developed and implemented in corporate security solutions, such as Kaspersky Endpoint Security for Business or Kaspersky Security for Mobile Devices.
There is reason to believe the number of personal devices used for working purposes and for storing corporate data will continue to increase, multiplying the risks. So the sooner company owners think of ensuring the safety of their infrastructure, the less probable data leaks and other unpleasant incidents will be.
 BYOD
BYOD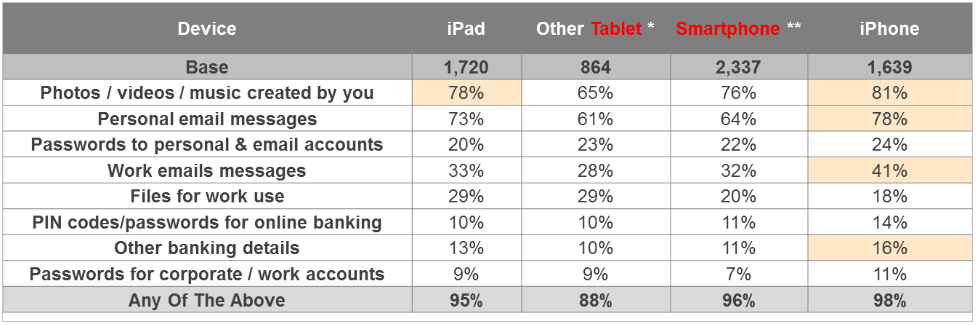

 Tips
Tips