Whenever we discuss Android security, we always recommend downloading apps only from the Google Play Store, as it contains significantly fewer malicious apps than other such sites. Still, developers manage to sneak in malware every now and then. So, how do you avoid picking up something nasty when downloading apps from Google Play? Pay close attention to the permissions requested by the app, and think carefully about why the app needs those permissions before you give it the green (or red) light. Today’s post looks at that very issue: the danger posed by a Google Play app that demands seemingly unnecessary permissions.
Not long ago, we discovered a couple of fairly unhealthy programs in Google Play posing as photo apps. Both apps hung around in the store long enough to chalk up 10,000 downloads each. There was nothing particularly eye-catching about them; they were just two members of the “yet another photo editor” class.
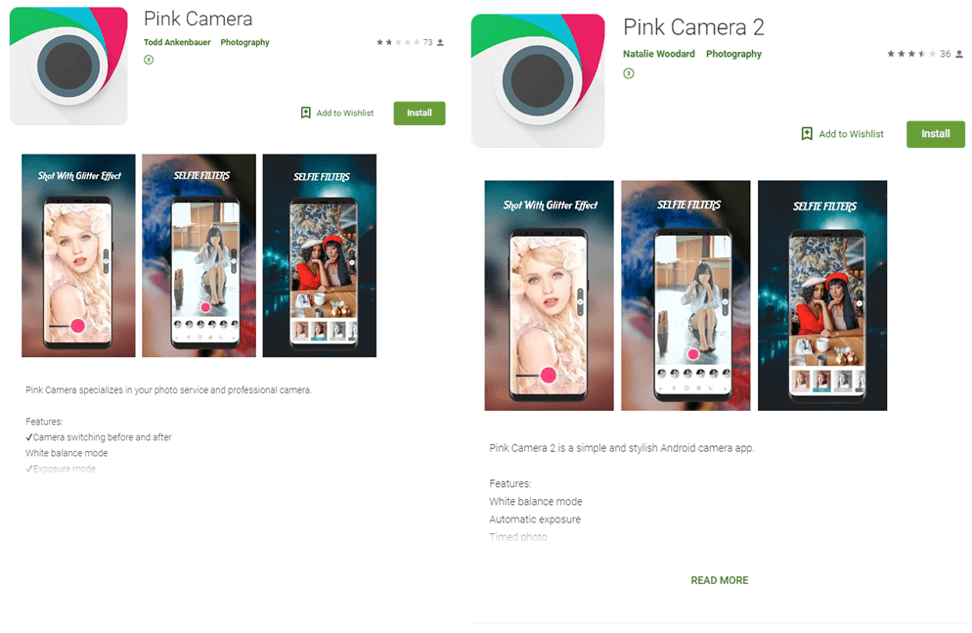
Two almost identical photo editors, said to be from different developers, secretly set up paid subscriptions
The only detail that might have alerted the observant user was that both apps persistently requested access to notifications, and they wouldn’t take no for an answer. All incoming messages appear in notifications, which means that the photo editors, if given permission, could read them. A photo editor has no need for such access — normally, that’s something used for communicating with a smartwatch. So, why would it request that?
Well, after installation, the putative photo editor collected information (phone number, smartphone model, screen size, mobile operator, etc.) and sent it to the cybercriminals’ server. In response, it received a list of Web addresses pointing (via several redirects) to a paid subscription sign-up page.
You’ve probably come across paid subscriptions at some point — either in the form of a tune that people hear when they call you and that requires daily payments, or a WAP or SMS mailing that you don’t need but that still empties your mobile account, penny by penny. Carriers in various countries are more or less fond of such paid subscriptions. More often than not, people subscribe to them out of sheer carelessness, not on purpose. Fail to read the fine print and before you know it, you’re paying for a horoscope. Victims usually become aware of such subscriptions only when their mobile phone account runs dry earlier than expected.
In this particular case, the malware’s task is to sign the victim up for the paid content in a way that raises no flags whatsoever. To do so, it disables Wi-Fi and, using mobile data, loads malicious pages in a window unseen by the user. To fill out the required fields (for example, with a phone number), it uses the previously harvested information. If the signup process employs a CAPTCHA, the image is sent to a special service for decoding. And the SMS verification code, if required, is intercepted through access to notifications.
How to avoid unwanted subscriptions
It is difficult to immediately gauge an app’s potential for harm. That said, there are ways to recognize a suspicious app and protect against undocumented features.
- Carefully review the list of permissions that the program requests. We strongly advise reading our separate post about Android permissions. If an app requests access to potentially dangerous permissions that you consider unnecessary, don’t be afraid to refuse. If it insists, delete it.
- Use a robust security solution. For example, Kaspersky for Android detects “subscription pages” and warns you of the danger.
- If your mobile operator offers the option, make such subscriptions impossible by opening a separate “content account” or activating a subscription-blocking service.
 Android
Android

