One of the most common ways to spread malware is to add malicious commands to macros in documents. In the vast majority of cases, this means macros for Microsoft Office files. That is, for Word documents, Excel spreadsheets, or Power Point presentations. The average company employee handles many such files every single day.
This problem is over 20 years old, so a solution, to put it mildly, is long overdue. This February, Microsoft announced its intention to block execution of macros in documents downloaded from the internet. However, already in early July, Microsoft Office users noticed that this innovation had been rolled back. At the time of posting, the company had yet to release an official statement on the decision, although a spokesperson noted it was temporary and “based on feedback.” In any event, this is a good time to recall what macros are exactly, how they can bad for corporate cybersecurity, and how to guard against this threat.
What are macros and why are they dangerous?
Often, Microsoft Office users need to automate various processes. To do so, you can program a certain algorithm or sequence of actions, known as a macro. A simple example: an accountant draws up a standard report every month; to save time, they create a macro to automatically highlight the names of clients in the second column in bold.
Macros are created in VBA (Visual Basic for Applications), which is somewhat simplified, but still a programming language. As is frequently the case, attackers can use it for their own purposes.
It’s worth noting here that familiarity with macros implies a fairly deep knowledge of the Office suite, which by no means all employees have, no matter what they write in their resumes. Some are not even aware that macros exist. Cybercriminals, on the other hand, use macros not for creating harmless algorithms for automating routines, but malicious commands.
How do they work?
A typical attack on a company starts with a mass dispatch of malicious e-mails to employees. These messages can look like job offers, company news, contractor invoices, information about competitors, and so on. The level of sophistication is limited only by the attackers’ imagination. The main aim is to get the recipient to open the attached file, or download a document by clicking the link provided and then opening it.
What the cybercriminals need is for the malicious macro in the file to be run. Many moons ago, embedded macros would run automatically, but Microsoft limited this functionality so that now, upon opening a file downloaded online, the user is informed that macros are disabled.
So, no problem any more, right? Not quite. Many users click the Enable Content button without thinking, thereby allowing automatic execution of said macros, which opens the door to malware. This is how attackers often gain access to the target company’s infrastructure. What’s more, as mentioned above, most employees have no idea what problems an innocent click on the Enable Content button can entail.
At long last, Microsoft took the only right decision — not to give the user a choice, but to block macros in downloaded files by default. The entire infosec expert community welcomed the news, and the innovation was implemented in early April of this year. Instead of a button, users saw a security warning with a link to a post about the dangers of macros. But the joy was short-lived — the change was rolled back shortly afterward.
How to protect yourself?
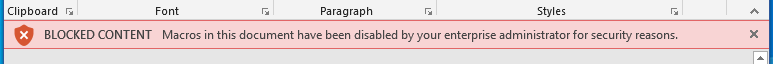
IT admins at large companies have always been able to disable macros at the security-policy level. So, if your workflows don’t require the use of macros, we’d recommend doing the same. I you do, a user who opens a document with a macro will see a different warning:
If this option isn’t available to you for some reason, then until Microsoft reintroduces default blocking of macros in downloaded files, it’s vital to protect all work devices with reliable security solutions. In addition, we recommend training all company employees in the basics of cybersecurity, focusing on the following main points:
- Never download and then open unexpected files, even if they appear to come from a person or organization you trust. It’s possible they were sent by scammers.
- Don’t blindly consent to enabling content in files downloaded from the internet or received by e-mail. For normal content viewing, this shouldn’t be necessary.
- If someone in an e-mail or on a website asks you to enable content, be especially suspicious.
 macros
macros


 Tips
Tips