Researchers from universities in both the U.S. and Israel have published a paper describing a “video-based cryptanalysis” method. This term is far from easy-to-understand, as is the paper itself. But, as always, we’ll try to explain everything in plain language.
Video-based cryptanalysis attack
Let’s imagine a real attack using this technology. It might go as follows. Intruders gain access to the video surveillance system in a corporate building. One of the cameras is pointed at the door of a high-security storage room for, say, secret documents. On the door is a smart card reader. A company employee approaches the door and inserts their card; the lock opens.
The smart card contains a microchip that talks to the reader. To verify the key encoded in the smart card against the data in the reader, the latter performs a cryptographic algorithm — that is, a series of calculations. In a normal situation, it’s extremely difficult to make a copy of such a key — even if you manage to get hold of the original. But there’s a vulnerability: the reader’s LED. This indicates that the device is working, changing color from red to green when a visitor is authorized and the door can be opened.
The brightness of the indicator, which depends on the load on the reader’s systems, changes during the cryptographic operation: for example, when the reader’s processor is busy with calculations, the LED brightness dips slightly. By analyzing these slight alternations, it’s possible to reconstruct the private key and thus create a smart card that opens the door to the secret room. If intruders have access to a video camera and can get video footage of the reader’s LED, in theory, they can then hack into the building’s security system.
Practical difficulties
Putting theory in papers such as this one into practice is never easy. The above scenario is unlikely to be implemented in practice any time soon. And for hardware-security pros, this vulnerability is nothing new. It’s a case of a classic side-channel attack: data leakage through some non-obvious process in a device’s operation. A traditional, decades-old method of attacking smart cards and other devices that use data encryption algorithms is to measure the voltage on the device. During the calculations, this voltage changes slightly. By observing these slight changes, an attacker might be able to reverse-engineer the algorithm: for example, by linking a voltage drop with a certain value being processed.
A feature of this kind of side-channel attack is that the calculations are very fast. To reconstruct the encryption key, one would have to measure the voltage hundreds or even thousands of times per second. But the LED is a part of the overall power-supply circuit of the device, which means that its brightness varies with the voltage. Check out the progress: the attack no longer requires complex and expensive equipment. No need to take the device apart and solder wires to the circuit board. Just point the video camera at the LED, make a recording, analyze it and get the result.
Video analysis features
When analyzing video footage in practice, the authors of the paper encountered numerous difficulties. A regular camera shoots video at 60 frames per second, while an advanced one — no more than 120. For an attack on an encryption algorithm, that’s way too low. To improve the method, the researchers exploited an inherent flaw in any digital camera that manufacturers typically struggle to overcome: the so-called rolling shutter. When we press the shutter button, the camera’s image sensor doesn’t take an instantaneous snapshot. What happens is that the sensor’s pixels are scanned sequentially, line by line, from top to bottom. If we photograph an object moving at high speed, this can produce artistic effects. Think of the rotating blades of a helicopter.

While the digital camera sequentially reads data from the image sensor, the propeller has time to shift. The result is a distorted image. Source
The researchers proceeded as follows: they moved the camera closer to the LED so that it filled almost the entire area of the frame. Then they measured the brightness, not of the whole frame, but of each line. Hence, the “measurement frequency” — and thus the accuracy — got a massive boost: up to 61,400 times per second in the case of the iPhone 14 camera. Curiously, in this rather atypical camera usage scenario, the iPhone got the better of Samsung in terms of the amount of data recorded.
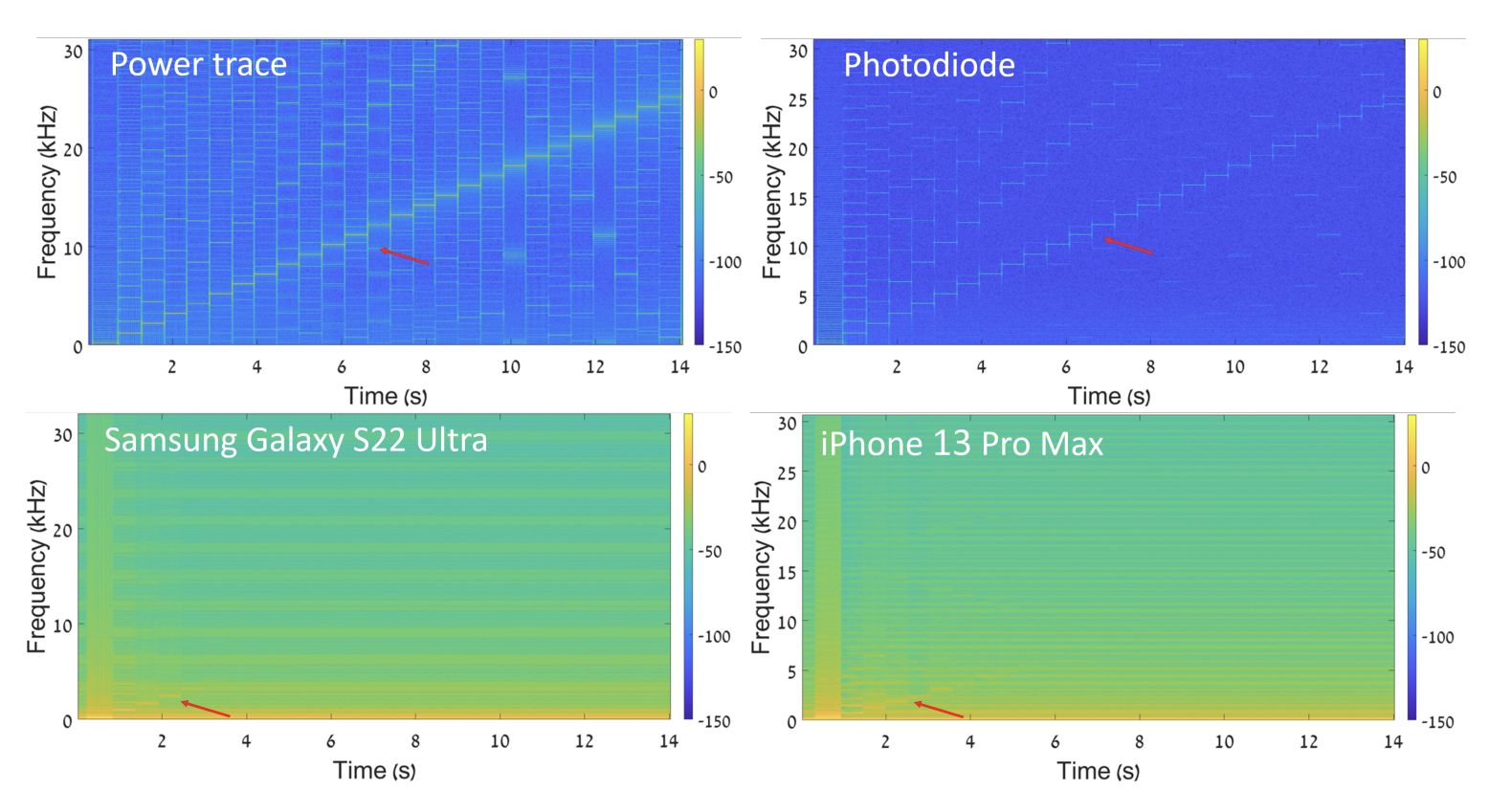
Testing smartphones’ ability to capture small changes in LED brightness at a certain frequency. Source
The above screenshot shows the result of this improved configuration: the researchers made the LED blink at a certain frequency, gradually increasing it. The switching on and off of the LED is clearly visible by measuring the power fluctuations (top left). The change in LED brightness can be seen clearly when using a specialized photosensor (top right). The test used two smartphones as video cameras (bottom row). As we can see, they recorded the blinking of the LED at a fairly low frequency; higher frequency changes in brightness were lost. But at the base frame-rate (60 or 120 times per second), even these results would be out of reach. This improvement turned out to be sufficient for a successful attack.
Attack results
To prove the possibility of a “video attack” in practice, the researchers showed how a private encryption key can be exfiltrated from various smart card readers. In each of the five experiments, the LED was made to blab its secrets. In theory, it’s not even necessary for the smartphone or video camera to be near the device; under certain conditions, the signal can be recorded from up to 60 meters away. The team also found that the presence of other light sources (a sun-lit room, for example) impacted the measurement accuracy. This complicates the attack by adding noise to the useful signal, but is not critical to the outcome.
But that’s not all. The researchers attacked a Samsung Galaxy S8, which was running the SIKE data encryption algorithm.

Exfiltrating secret data from a smartphone. Source
A smartphone has no LED that lights up when the device is turned on. But the researchers got crafty: they took the phone and connected portable speakers that did have an LED! Because the speakers were powered by the smartphone, the scenario whereby LED brightness depends on processor load was replicated.
The result was a Hertzbleed attack on the phone (see here for details), confirming that processors based on ARM architecture are also at risk of this type of attack (the original paper covered only vulnerabilities in Intel and AMD chips with x86 architecture).
We’re now talking about a wholly theoretical experiment, not about stealing any actual encryption keys in use. Cryptographic calculations were triggered on the smartphone according to a certain algorithm. By measuring the brightness of the LED on the speakers connected to the phone, the researchers managed to capture the operation of the algorithm and recover the private key. Since a smartphone is far more complex than a smart card reader, the noise level in the measurements was much higher. Nevertheless, the experiment was successful.
On the usefulness of this scientific research
This study will unlikely be applied in practice any time soon. The attack is highly complex, and it’s hard to find a realistic use case for it. As is often the case, the interest value of such papers does not lie in the practical exploitation of “discovered vulnerabilities”. Perhaps the key takeaway of this study is that the specialized equipment once needed for side-channel attacks has been replaced with off-the-shelf devices.
We often post about data exfiltration through non-obvious channels, such as a desktop PC speaker. But in all these cases, malware must already be installed on the victim’s computer. This paper hints at the possibility of exfiltrating sensitive information without prior hacking, simply by observing a power LED.
And that makes it an important contribution to our general knowledge of side-channel attacks. We can only hope that manufacturers of vulnerable devices take note and improve the design of new models — before such security holes become exploitable in practice. After all, as the paper rightly points out, it’s quite simple to make an LED that doesn’t reveal secret information: for example, add a dirt-cheap capacitor to the power supply circuit, and the problem’s solved. And measures to counteract side-channel attacks can be implemented at the software level too. Finally, why not ditch the LED altogether? Would anyone really miss it?
 data
data

 Tips
Tips