Your smartphone gallery may contain photos and screenshots of important information you keep there for safety or convenience, such as documents, bank agreements, or seed phrases for recovering cryptocurrency wallets. All of this data can be stolen by a malicious app such as the SparkCat stealer we’ve discovered. This malware is currently configured to steal crypto wallet data, but it could easily be repurposed to steal any other valuable information.
The worst part is that this malware has made its way into official app stores, with almost 250,000 downloads of infected apps from Google Play alone. Although malicious apps have been found in Google Play before, this marks the first time a stealer Trojan has been detected in the App Store. How does this threat work and what can you do to protect yourself?
Malicious add-ons to legitimate apps
Apps containing SparkCat’s malicious components fall into two categories. Some, such as numerous similar messenger apps claiming AI functionality, all from the same developer, were clearly designed as bait. Some others are legitimate apps: food delivery services, news readers, and crypto wallet utilities. We don’t yet know how the Trojan functionality got into these apps. It may have been the result of a supply chain attack, where a third-party component used in the app was infected. Alternatively, the developers may have deliberately embedded the Trojan into their apps.

The first app where we detected SparkCat was a food delivery service called ComeCome, available in the UAE and Indonesia. The infected app was found on both Google Play and the App Store
The stealer analyzes photos in the smartphone’s gallery, and to that end, all infected apps request permission to access it. In many cases, this request seems completely legitimate — for example, the food delivery app ComeCome requested access for a customer support chat right upon opening this chat, which looked completely natural. Other applications request gallery access when launching their core functionality, which still seems harmless. After all, you do want to be able to share photos in a messenger, right?
However, as soon as the user grants access to specific photos or the entire gallery, the malware starts going through all the photos it can reach, searching for anything valuable.
AI-powered theft
To find crypto-wallet data among photos of cats and sunsets, the Trojan has a built-in optical character recognition (OCR) module based on the Google ML Kit — a universal machine-learning library.
Depending on the device’s language settings, SparkCat downloads models trained to detect the relevant script in photos, whether Latin, Korean, Chinese, or Japanese. After recognizing the text in an image, the Trojan checks it against a set of rules loaded from its command-and-control server. In addition to keywords from the list (for example, “Mnemonic”), the filter can be triggered by specific patterns such as meaningless letter combinations in backup codes or certain word sequences in seed phrases.
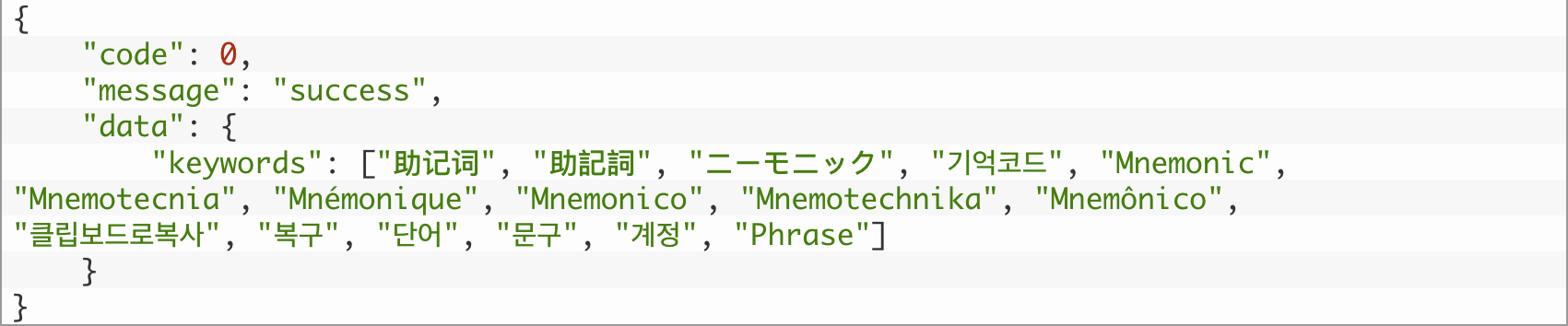
During our analysis, we requested a list of keywords used for OCR searching from the Trojan’s C2 servers. The cybercriminals are clearly interested in phrases used to recover access to crypto wallets — known as mnemonics
The Trojan uploads all photos containing potentially valuable text to the attackers’ servers, along with detailed information about the recognized text and the device the image was stolen from.
Scale and victims of the attack
We identified 10 malicious apps in Google Play, and 11 in the App Store. At the time of publication, all malicious apps had been removed from the stores. The total number of downloads from Google Play alone exceeded 242,000 at the time of analysis, and our telemetry data suggests that the same malware was available from other sites and unofficial app stores, too.

Among the infected apps are popular delivery services and AI-powered messengers in both Google Play and the App Store
Judging by SparkCat’s dictionaries, it’s “trained” to steal data from users in many European and Asian countries, and evidence indicates that attacks have been ongoing since at least March 2024. The authors of this malware are likely fluent in Chinese — more details on this, as well as the technical aspects of SparkCat, can be found in the full report on Securelist.
How to protect yourself from OCR Trojans
Unfortunately, the age-old advice of “only download highly-rated apps from official app stores” is a silver bullet no longer — even the App Store has now been infiltrated by a true infostealer, and similar incidents have occurred repeatedly in Google Play. Therefore, we need to strengthen the criteria here: only download highly-rated apps with thousands, or better still, millions of downloads, published at least several months ago. Also, verify app links in official sources (such as the developers’ website) to ensure they’re not fake, and read the reviews — especially negative ones. And, of course, be sure to install a comprehensive security system on all your smartphones and computers.
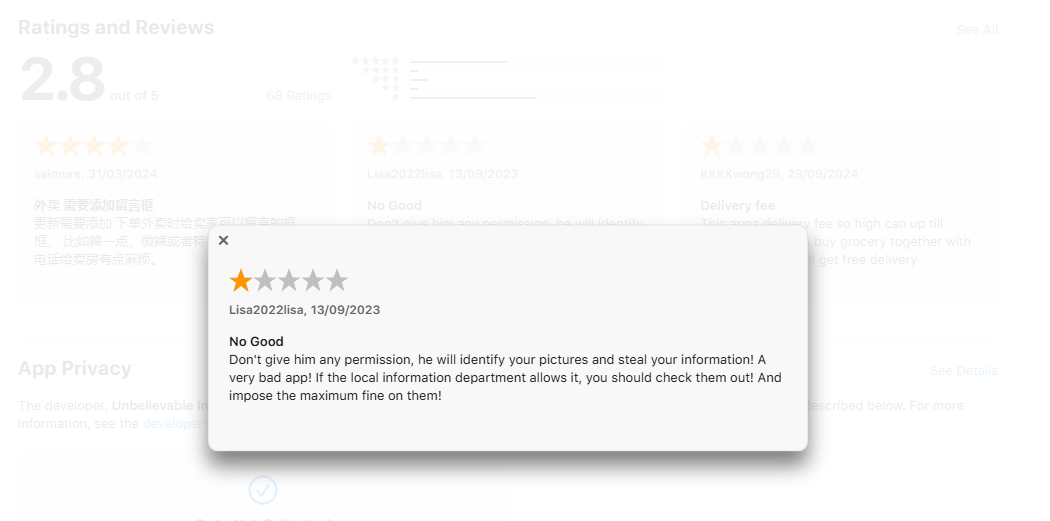
Checking negative reviews of the ComeCome app in the App Store could have put users off downloading it
You should also be extremely cautious about granting permissions to new apps. Previously, this was primarily a concern for “Accessibility” settings, but now we see that even granting gallery access can lead to the theft of personal data. If you’re not completely sure about an app’s legitimacy (for example, it’s not an official messenger, but a modified version), don’t grant it full access to all your photos and videos. Grant access only to specific photos when necessary.
Storing documents, passwords, banking data, or photos of seed phrases in your smartphone’s gallery is highly unsafe — besides stealers such as SparkCat, there’s also always the risk that someone peeks at the photos, or you accidentally upload them to a messenger or file-sharing service. Such information should be stored in a dedicated application. For example, Kaspersky Password Manager allows you to securely store and sync not only passwords and two-factor authentication tokens but also banking card details and scanned documents across all your devices — all in encrypted form. By the way, this app comes with our Kaspersky Plus and Kaspersky Premium subscriptions.
Finally, if you’ve already installed an infected application (the list of them is available at the end of the Securelist post), delete it and don’t use it until the developer releases a fixed version. Meanwhile, carefully review your photo gallery to assess what data the cybercriminals may have obtained. Change any passwords and block any cards saved in the gallery. Although the version of SparkCat we discovered hunts for seed phrases specifically, it’s possible that the Trojan could be reconfigured to steal other information. As for crypto-wallet seed phrases, once created, they can’t be changed. Create a new crypto wallet, and transfer all your funds from — and then abandon completely — the compromised one.
 iOS
iOS

 Tips
Tips