Public awareness of — and wariness about — Web privacy continues to grow. That should come as no surprise: These days, pervasive cybertracking affects everyone. In this article, the last in our series about digital marketing (for some background, see part 1 and part 2), we briefly explain some of the tools marketers use to track pretty much all of your movements online.
You’ve got cookies
Many of you may have heard of Web cookies: small text files that the websites you visit store on your computer. Using web cookies, a website can track your online activity, know how long have you spent on the site, keep your logged-in session open, remember the language you chose for it to display or other customizations, and so on.
When the server of the site you are visiting sets a cookie called a first-party cookie, in most cases it is for analytics or functional purposes only. This kind of cookie is often essential, and without one, site functionality would be compromised.
On the other hand, third-party cookies, Web cookies set by entities from companies whose sites you aren’t visiting, can represent a threat to your online privacy. It’s easy to understand the appeal of those files for Web marketers, which track your activities by across various websites. We therefore suggest keeping the most prominent marketers out of your computer by checking Block third party cookies in your browser’s settings.
Your fingerprint is unique, even on the Web
A very aggressive way to track users, fingerprinting is far more sophisticated than cookies — and harder to evade. The process uses a script to gather information about a device: device type and operating system (PC, iPhone, iPad, Android, Blackberry, etc.), installed browser extensions, version of common plugins such as Java and Flash, character encoding, language, time zone, screen resolution, list of installed fonts, and much more.
All of this information put together helps create a unique ID for a device. Even if a person bought two identical devices and powered on them for the first time in the same location, thus creating identical fingerprints, the fingerprints would diverge after just a few hours of use and personalization by different people.
Local storage is stronger than cookies
It’s easy to develop a website that can read visitors’ browser history, and that information is a treasure trove for Web marketers. Sure, everybody knows how to delete their browser history and cookies, but who does it regularly? Moreover, did you know that HTML5 offers new ways for site developers and Web marketers to save data on your computer, in addition to cookies?
With local storage and session storage, a large amount of data can be stored locally, in the user’s browser — and that is the big difference between local storage and web cookies. Session storage makes data available for the current browser session, but everything is lost when the browser tab is closed. Data saved in local storage has no expiration date, so in theory, such information remains on your computer until you manually delete your browser’s cache. Access to local storage is limited to the domain that saved the data, but once again, that is not enough for you to feel secure.
Marketers target your interests
Let’s dig a bit deeper into Web marketing strategy. How can marketers draw a precise profile of your interests? It’s easy: Consider that most of the websites you visit include third-party advertising and tracking scripts. If two or more websites use the same ad network or DMP (digital management platform), then the data they save as cookies and local storage, or send through tracking parameters, is shared between the sites, which, in fact, lets them overcome the local storage limitations described above.
For example, Krux, a company recently acquired by Salesforce, supports more than 200 billion data collection events each month, interacting with more than 3 billion browsers and devices. Its tracking scripts are hosted on thousands of websites around the world.
Here’s an example to illustrate the concept. Vice.com and allrecipes.com are two independent websites that apparently don’t share users’ information with each other — why would they? — but both sites host Krux’s scripts. If you visit those websites, even at different times, you’ll see that the same keys are saved in local storage by cdn.krxd.com, a Krux CDN (content delivery network).
Websites increasingly implement more than one third-party ad network and DMP script (sometimes dozens!), making it easier for marketers to put together a lot of data about us. With all of that data, marketers can perform segmentation on various bases: geographical, demographic, and, above all, behavioral — in short, quantifying you based on your real interests. That’s how and why you get targeted advertising based on your interests and your recent queries, website visits, and purchases.
Marketers target your sentiments
In part 2 of this series, we mentioned social marketing. The exponential growth in social advertising, which will reach $36 billion in 2017, goes hand in hand with the tracking tools made available by developers. One interesting method is sentiment analysis applied to social networks. It consists of bots that scan what we post on social networks, even in blogs, and try to understand our feeling about some matter.
The simplest way is to analyze likes and emoticons. For example, if you share an article about Caribbean cruises, and you add a smiley in the post, it means that you like exotic vacations. Or you may publish an impulsive post against a politician. Sentiment analysis then yields your political orientation. When someone puts together these and other data, they can define your perfect profile, and in some ways understand you better than your friends do.
Marketers consider context
Marketers use bots, similar to the sentiment-targeting ones we just mentioned, to serve contextual ads on websites. Using this kind of targeted advertising, an automated system scans web page content, tries to understand the topic, and then serves ads based on the context. Contextual advertising, mixed with behavioral targeting and native advertising, is the secret to creeping even into the most aware person’s mind and causing them to click on ads.
The big eye is on you
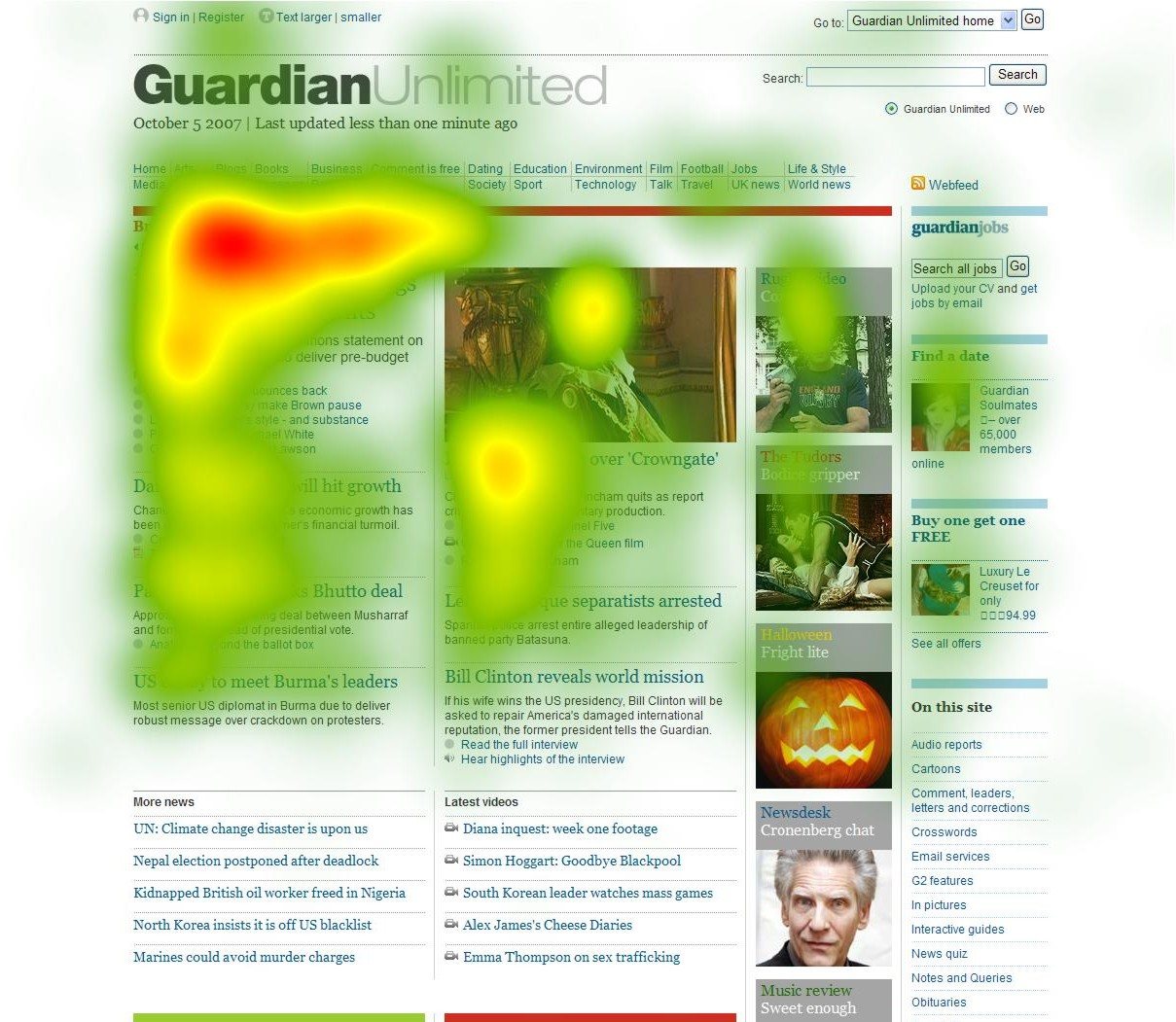
Sentiment and text analysis are not enough for marketers; they want more! They want to see you as if they were standing right behind you, spying on your screen over your shoulder. And many websites use special scripts to do something very close to that, letting marketers record your mouse movements and click activity. Using that data they can make a video capture of your session or heat maps like this one:
Tips for protection
We know some readers are less concerned than others about marketers tracking their movements online in increasingly sophisticated ways, composing comprehensive and highly personal profiles of users. It’s your right not to be creeped out by ads on a news site that know what you were just shopping for on Amazon or what your spouse was posting about on Facebook. We also believe that every user of online services and connected devices deserves to know the extent of the information they are providing to entities whose driving goal is to turn a profit.
With that in mind, here are a few important tips about how to protect yourself from Web tracking:
Change the default cookie settings in your browser and reject third-party cookies to avoid having your data saved by third-party cookies and local storage. This setting affects session and local storage as well. Learn how manage cookie settings in Chrome, Firefox, Internet Explorer, Edge and Opera.
Set your browser to automatically clear local data when you close it. For example, in Google Chrome, go to Settings → Show advanced settings… and click the Content settings button, which is in the Privacy section. Under Cookies, tick Keep local data only until you quit your browser. That’s it.
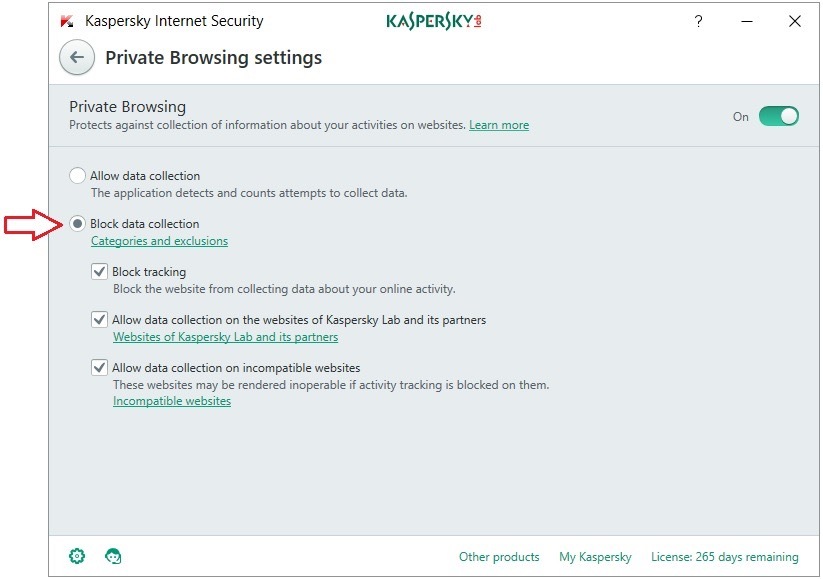
Block fingerprinting, sentiment analysis, session tracking, analytics tools, and any other kind of tracking, by manually enabling Private Browsing in Kaspersky Plus and Kaspersky Premium. To do that, open Settings and select Protection. Scroll down the page and open Private Browsing. Once there, tick Block data collection, which is not enabled by default.
 privacy
privacy

 Tips
Tips