As computer users become increasingly concerned about data privacy and protection, they’re turning to encryption software to enhance security. Unfortunately, cybercriminals are always on the lookout for a new trend to exploit and have developed malware that gives them access to encryption software – and the data it’s supposed to protect.
What happened?
In the summer of 2016, a cyberespionage actor we call StrongPity infected some open source encryption installers. In addition to distributing infected installers, they also used watering holes targeting arbitrary users, mostly in Italy and Belgium. This tactic is similar to the one used by Dark Hotel to spread across Asia. Now it’s Europe’s turn.
Our analysis indicates that the StrongPity actor is not only determined, but well-resourced and fairly innovative as well. Over the summer, they compromised both WinRAR (for its file encryption capabilities) distributor sites, and created a fake mirror image of the sourceforge TrueCrypt site (for open source full disk encryption).
Mitigate #threats from infected #encryption software.
Tweet
It’s not the first time official distributives of specialized software have been spoofed. In early 2014 Crouching Yeti trojanized legitimate ICS-related software installers such as industrial camera drivers; the malware was spread by compromising legitimate device driver sites and replacing official installers with the trojanized ones.
This summer, StrongPity adopted the same tactic. First, they set up a domain name (ralrab[.]com) mimicking the legitimate WinRAR distribution site (rarlab[.]com). Then they placed links on legitimate European distribution sites to redirect users to malware-infected installers on a new domain:
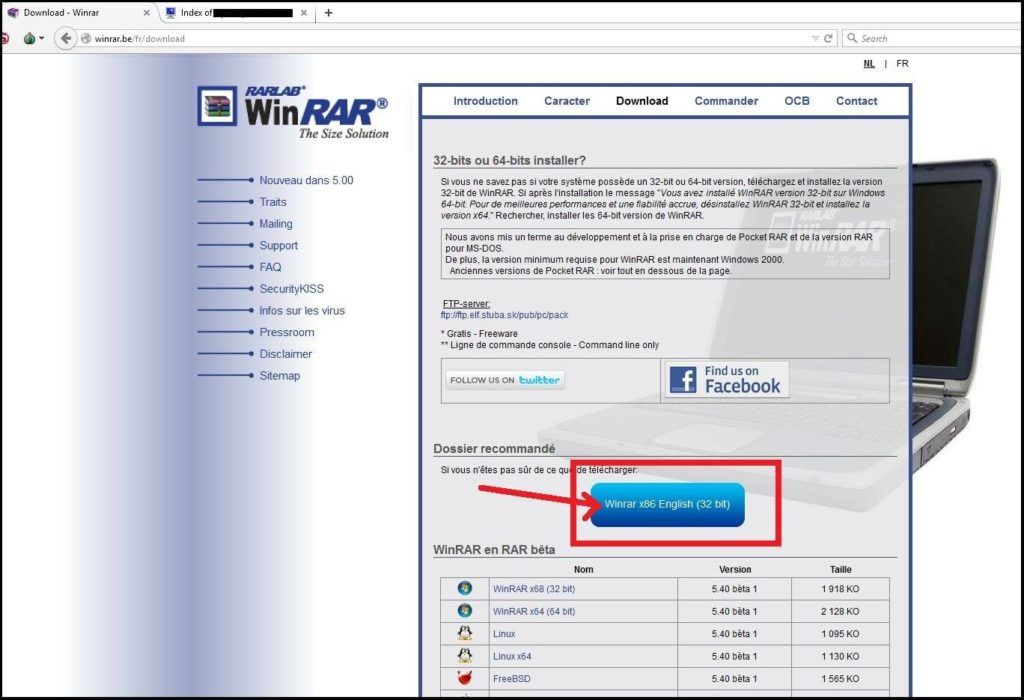
Winrar[.]be site with “recommended link” leading to malicious ralrab[.]com.
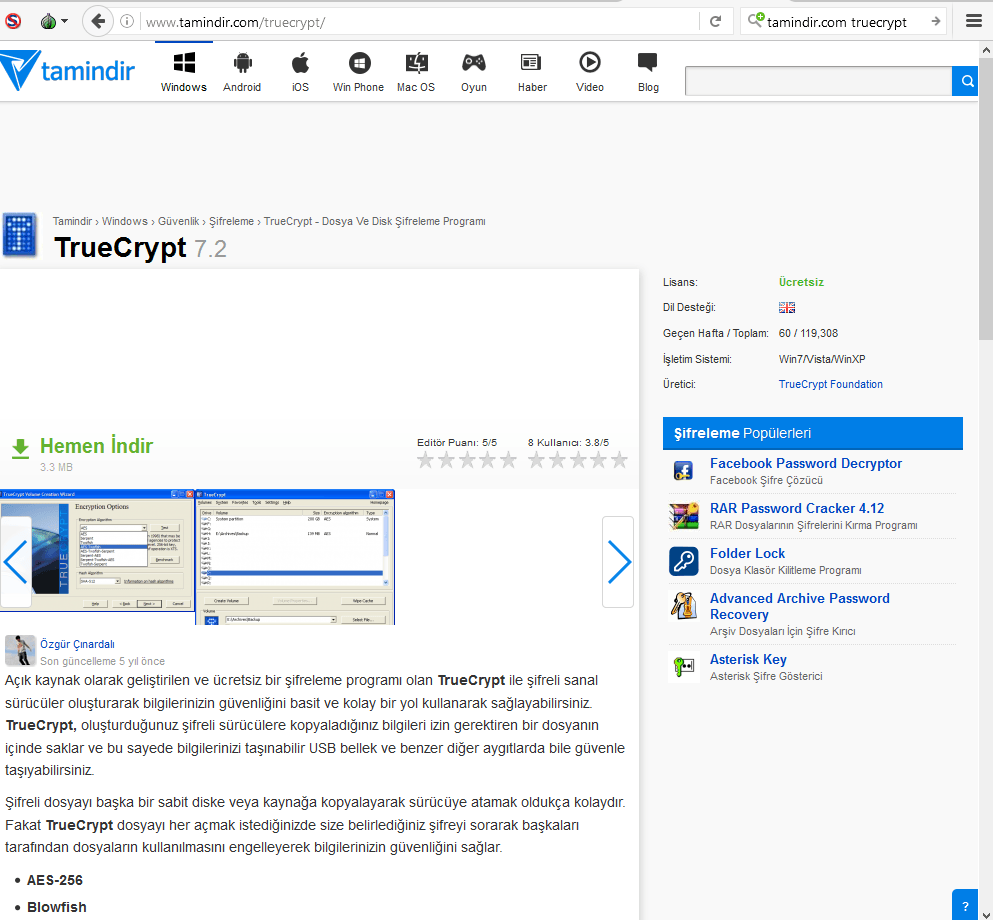
Tamindir TrueCrypt page with malicious redirection.
StrongPity’s malware droppers are often signed with unusual digital certificates. These modules drop multiple components that give the cyber-criminals complete control of the victim’s system and (the reason for choosing encryption software) effectively steal disk contents. To date, over 1000 systems have been detected with a StrongPity component or attempting to download a poisoned/trojanized installer.
A new #malware gives criminals access to #encryption software and the data it is supposed to protect.
Tweet
You can read a detailed report about the operation here.
Protective measures
Once again, we’re seeing an attack in which previously reliable products are compromised, along with the official vendor or localization companies’ websites being used to re-direct users to malicious sites. Our prediction is that the volume of malware masquerading as a legitimate distributive will only grow, making quality software allowlists an important component of effective malware detection mechanisms. We’ll never tire of repeating that only multi-layered security solutions really work.
It’s worth noting that attacks launched through compromised ICS vendor websites and installers could be classified as “industry targeted” – after all, who needs that kind of software, other than industrial businesses? This time spoofed encryption software sites and their trojanized installers mostly targeted victims’ encrypted data and communications.
Correctly installed protection mechanisms could catch attack malware modules in their early stages. Defensive measures should take heuristics, machine learning and all other current corresponding algorithms into account. In Kaspersky Lab’s case, all required measures are implemented in Kaspersky Endpoint Security and its small businesses counterpart, Kaspersky Small Office Security.
In StrongPity’s case, the tools chosen by the threat actors – WinRAR and TrueCrypt – are used mainly by people who don’t want to spend a lot of money on encryption. While it’s highly unlikely that enterprises would choose such software, home users and smaller businesses do. And they’re the ones who become victims of their trust in software that was developed to protect their data. Our advice: trust no one and implement your security properly.
 cyberespionage
cyberespionage

 Tips
Tips