You’re in a hurry, trying to get to work, a business meeting, a date. So you launch your favorite app for booking a taxi as usual, but this time, it prompts you to enter your credit card number. Does that seem suspicious? It may not — apps forget information, and all you have to do is add your card number again.
However, after some time you notice money disappearing from your account. What happened? You may be the unlucky winner of a mobile Trojan. This kind of malware has been caught recently stealing bank data by impersonating the interfaces of taxi-booking apps.
The Faketoken Trojan has existed for a long time, and it has been upgraded for many years. Our experts named the current version “Faketoken.q,” and by now it has learned a significant number of tricks.
After getting onto a smartphone (judging by the malware icon, Faketoken infiltrates smartphones through bulk SMS messages with a prompt to download some picture) and installing the necessary modules, the Trojan hides its shortcut icon and starts background monitoring of everything that happens in the system.
First, the Trojan is interested in the user’s calls. As soon as it detects a call, it starts recording. When the call is finished, Faketoken sends the recording to the criminal’s server. Second, the Trojan also checks which apps the smartphone’s owner uses.
When Faketoken detects the launch of an app whose interface it can simulate, the Trojan immediately overlays the app with its own screen. To achieve that, it uses a standard Android feature that supports showing screen overlays on top of all other apps. A whole bunch of legitimate apps, such as messengers, window managers, and so on, use this feature.
The overlaying window matches the colors of the original app’s interface. In this window, the Trojan prompts the user to enter the number of his or her credit card, including the verification code from the back of the card.
Actually, Faketoken.q is after a huge variety of apps that have one thing in common: in them, a request to enter payment data looks normal enough not to arouse suspicion. Among the attacked apps are a number of mobile banking apps, Android Pay, the Google Play Store, apps for booking flights and hotel rooms, and apps for paying traffic tickets — as well as apps for booking taxis.
During the very stage of stealing money from the user, Faketoken resorts to another ruse, intercepting all incoming SMS messages, hiding them from the user, and forwarding them to the criminals’ server, where one-time passwords for payment confirmation from those messages are extracted.
Judging by the small number of attacks that we have registered and the UI artifacts, which you can see in one of the screenshots above, we’d say the researchers at our antivirus laboratory got their hands on one of the test versions of the Trojan, not the final one.
We must give the assiduous creators of Faketoken their due. They will most likely improve the Trojan, and a wave of infection incidents may sprout from the “commercial” version at some point.
Currently the Trojan is focused on users in Russia, but as we’ve seen many times in the past, cybercriminals constantly steal ideas from each other, so it won’t take long for them to adopt the same trick in other countries. A lot of city dwellers have taxi-booking apps installed these days, so this trick represents a good opportunity for malware creators.
Below you can find several pieces of advice on how to protect yourself against Faketoken and similar mobile Trojans that steal card numbers and intercept SMS messages with one-time passwords used to confirm payments.
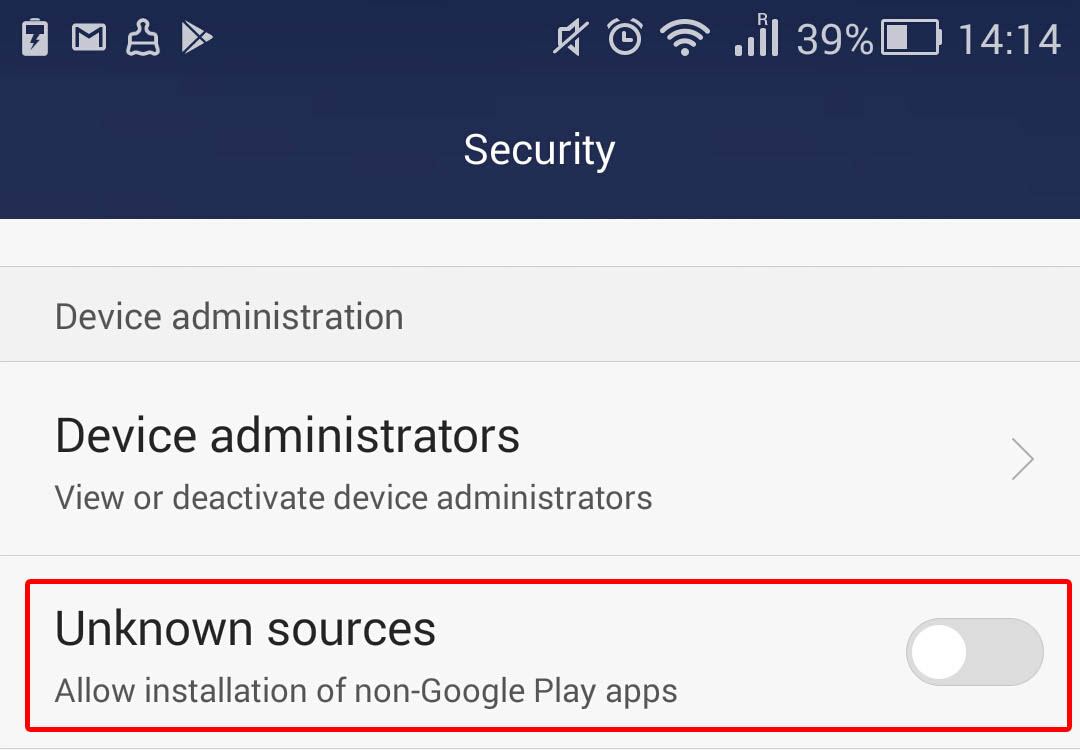
- It is imperative that you go into Android’s settings and prohibit the installation of apps from unknown sources. To block installation from unknown sources, go to Settings -> Security and uncheck Unknown sources.
- Always pay attention to what access permissions an app requests during installation, even if you downloaded it from Google Play (there might be Trojans in the official app store as well). You can learn more about Android permissions in this article.
- It is a good idea to protect your smartphone by installing antivirus, which can find infections hiding in an app. For example, you can use our basic Kaspersky Internet Security for Android, which you can download from Google Play free.
 Android
Android