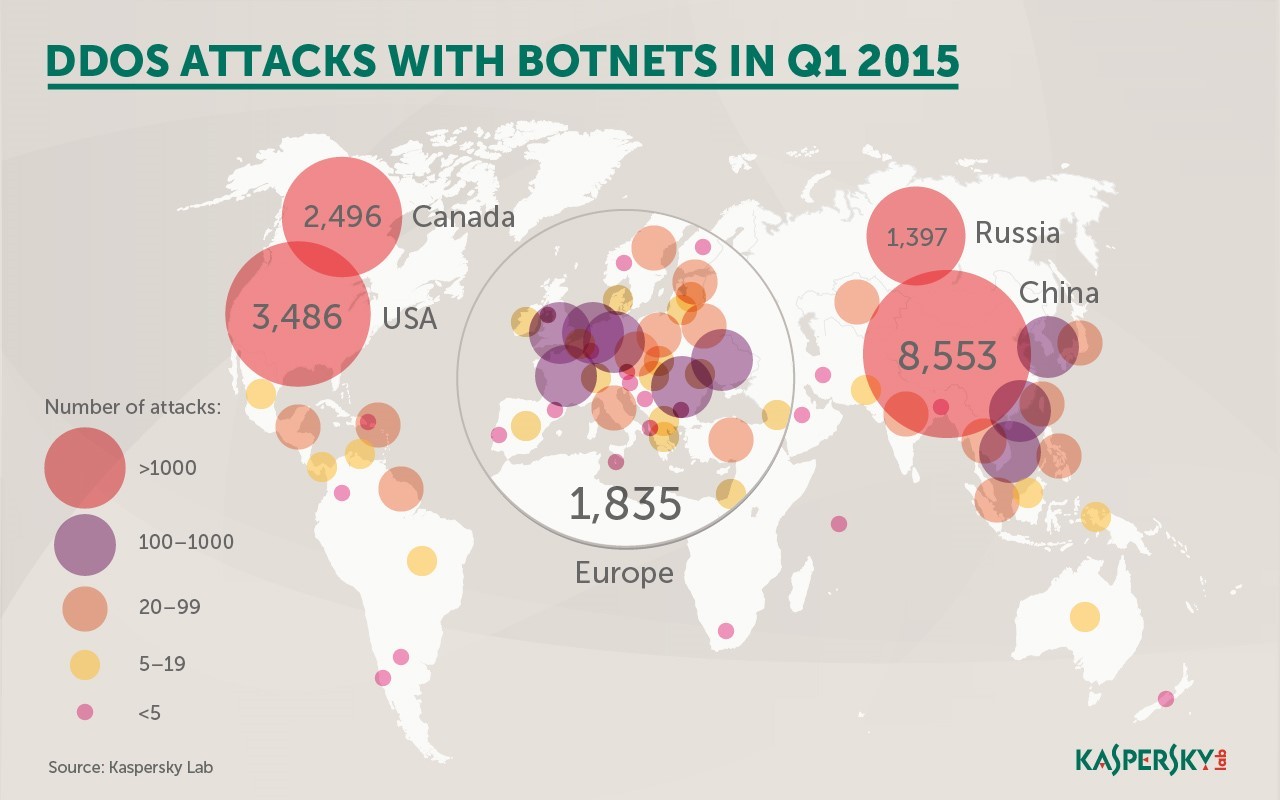
Cybercriminals in Q1, 2015 carried out more than 23,000 botnet-assisted DDoS attacks on web resources located in 76 countries, which is up 15% from Q4, 2014. Servers in the U.S., Canada, and China were most frequently targeted, while the top 10 victims also included resources in Europe and the Asia-Pacific region, according to Kaspersky Lab’s latest stats.
The good news: overall there were less botnet-assisted DDoS attacks than in Q4, 2014. The bad news: the geographic expanse has increased. Besides, as Kaspersky Lab’s experts acknowledged, the stats are based on data from DDoS Intelligence system (a part of Kaspersky DDoS Protection solution), and that data is limited to those botnets that were detected and analyzed by Kaspersky Lab.
Q1, 2015: #DDoS On The Move
Tweet
Also, botnets are the most popular, but not the only tool for carrying out DDoS attacks. Which means that the data gathered isn’t covering the entire range of DDoS attacks for the given time period.
Still, the Kasperky Lab’s statistics tell us a lot:
Stats
- There were a total of 23,095 attacks in Q1. These affected targets in 76 countries, up 15% from the 66 countries affected in Q4, 2014.
- The greatest number of attacks on a single web resource in Q1 was 21 – about two attacks a week. In Q4, 2014 the equivalent figure was 16.
- The most protracted botnet attack in Q1 was almost six days long.
- The infographics below show the largest number of the DDoS attacks occurred in China.
It is also high in the list of the countries with the largest numbers of C&C servers at the specified time period.
- In Q1, 2015 SYN DDoS and HTTP DDoS were the most common scenarios for botnet-assisted DDoS attacks.
- Attacks peaked in numbers around December, decreased notably in February, and began to grow again by March. Apparently that increase in activity is linked to the Christmas season, when competition is hot, and unscrupulous individuals prefer to “protect their business” that way.
Damaging factors and mitigation
DDoS are most often targeted at businesses, with a main purpose to cripple operations and break continuity. Which they do in a rude yet effective fashion – by flooding the internet bandwidth making the company’s website unreachable or by sending a number of requests to the company’s server that it is unable to process.
We have previously wrote about the types of DDoS attacks (there are quite a few of them, and, again, not all of them are botnet-assisted) – take a look.
The primary damaging factor of DDoS attack is restoration cost. A single attack may cost a business from $52,000 to $444,000, depending on the size of the company. For many organizations these expenses may have a serious, if not lethal, impact on the balance sheet, along with reputation damage due to loss of access to online resources for partners and customers.
At the same time, criminals have to pay just around 50 dollars a day to those who operate the botnets. A lot of damage with little effort and cost.
By the way, it also allows the attackers to be quite persistent: in Q1 a A Russian-language website belonging to a group of investment companies had been hit (hold onto your hats) 21 times! A Vietnamese website of a wedding provider had been DDoS’ed 16 times, and a hosting provider in the U.S. was attacked 15 times per quarter. Clearly those were attempts to put the businesses out of commission or to extort money.
There is very little chance to find out who ordered and launched the distributed DoS attacks, which allows the attackers to revel in impunity.
The primary damaging factor of #DDoS attack is cost
Tweet
According to an earlier study by Kaspersky Lab and B2B International, only 37% of the organizations surveyed said they currently have measures in place to protect against DDoS-attacks. Probably because until recently, protection from these kind of attacks was deemed impossible or overly expensive. In fact, it is neither: IT security market today can offer reliable and easy-to-deploy security solutions that are able to prevent loss of access to online services caused by DDoS attacks.
Kaspersky DDoS Protection is one of them. A dedicated security solution to filter cybercriminals’ junk requests from legitimate web traffic, Kaspersky DDoS Protection combines Kaspersky Lab’s proven expertise with in-house technology such as DDoS Intelligence. It is a system that analyzes the information sent from C&C servers to botnets, and aims to improve protection against DDoS attacks.
For details on how Kaspersky DDoS Protection and Intelligence work, please refer here.
 ddos
ddos