Sony Corp. underwent a large-scale fiasco in April 2011, when a security breach affected tens of millions of people. The intruders stole the personal data of many users along with their credit card numbers, and the Sony Playstation Network service did not function for several months. Almost immediately, Sony admitted users’ personal data had been stored on Sony Playstation Network servers in an unencrypted form. However, the credit card numbers were stored separately and they were encrypted.
This example from Sony is important because according to the company, the unencrypted personal information was stored within “a very sophisticated security system that [nevertheless] was compromised by hackers”. This approach seems almost logical: why spend money on a data encryption system when your information can be stored behind seven padlocks? However, this approach is flawed and Sony learned the hard way; their financial and reputational loses were enormous.
Sony is not the only example. In July 2012, hackers broke into Yahoo! Voices, which stored user logins and passwords in an unencrypted form as well.
The moral here is very simple: if a company processes other people’s data it must be encrypted. This rule by no means depends on the size of the company and its alleged “attractiveness” to criminals. If criminals believe you have possesses data of interest, it’s just a matter of time before an attack will take place.
Similarly, any company big or small surely possesses data that holds trade secrets that’s too important to let fall into the wrong hands. To ensure its security, you have to back up the data, and secondly, it must be encrypted.
Data encryption functions are implemented in Kaspersky Small Office Security in a simple and effective way. When selecting the appropriate menu item, you open a window, which proposes creating a new “container” – a virtual encrypted disc to store the data on. By default the folder is C:Encryption, but you can place this container anywhere. Storing the data separately on any external disc is not just possible, but recommended.
To create a container, first you must define its location and size, which is critical if you intend to store the encrypted data on an external drive, and after that you set a password. You cannot forget it because the data will be irretrievable without it.
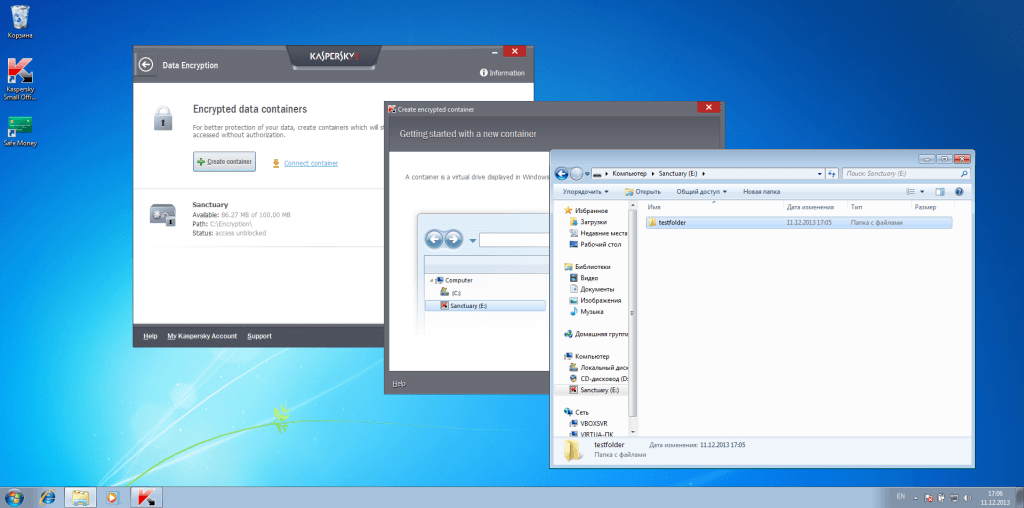
The container is created as a virtual disc in the system. You will be offered a chance to check it for viruses just like any other connected drive.
In order to encrypt data you just drag and drop (copy) the necessary files to this drive in Windows Explorer, then you click the button “Encrypt” in the interface of KSOS.
The newly created virtual drive disappears and there is only one file left with the specified container’s name and extension .KDE.
If you want to extract the stored data you need to “connect the container” by opening the file with Kaspersky Small Office Security (or any other solution by Kaspersky Lab) and enter your password.
 data
data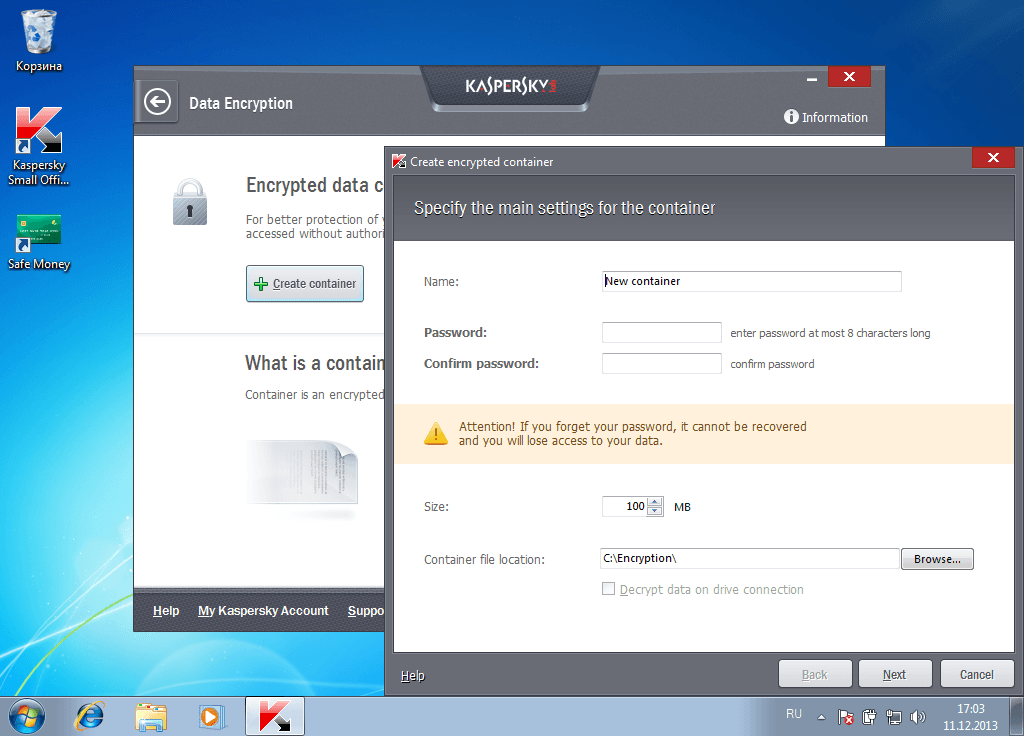

 Tips
Tips