Kaspersky Lab experts have investigated a new series of attacks by the Darkhotel cybercriminal group. Featuring an Adobe Flash 0-day exploit from the Hacking Team breach, the attack also has a wider geographic reach. The first sighting of Darkhotel is mostly remembered for its unusual spreading mechanism. Along with peer-to-peer and other spreading tactics, this APT has, for several years, maintained a capability to use hotel networks to follow and hit selected targets as they travel around the world.
In 2015, actors’ preferable techniques shifted towards persistent spear-phishing of their chosen targets. Currently, we’re finding victims in other geographical regions, new variants of malicious .hta, .rar spearphishing attachments with right-to-left override (RTLO) method to fake files extensions, and the deployment of a 0-day from Hacking Team.
It’s not only high profile targets, and more than the perimeter needs to be secured
Darkhotel’s targeted attack modules, which infects hotel networks, show us that state-owned organizations or large enterprises with a lots of sensitive data are not the only targets. Relatively small businesses (like hotels, in this case) can become a stepping stone to reach a target, and hotels aren’t the only way to aim the corporate C-level managers and their secrets through third-party organizations. So even small and medium companies have to keep the risk of targeted attacks in mind.
Some enterprises underestimate the value of endpoint protection in their IT security strategy; Darkhotel’s victims could tell a lot about just how important endpoints security is. Portable, mobile devices aren’t always used inside the perimeter; outside the corporate environment, endpoints connecting through unknown wired and wireless networks, should be properly protected.
How the disease is spreading
Now spreading to North and South Korea, Russia, Japan, Thailand and Germany, among others, Dark Hotel begins with a spearphishing or drive-by infection that exploits the Adobe Flash 0-day.
Some targets are spearphished repeatedly using similar social-engineering schemes. Darkhotel consistently archives droppers (.scr executable files with faked extensions using RTLO) within .rar archives, in order to appear to the target as innocuous .jpg files.
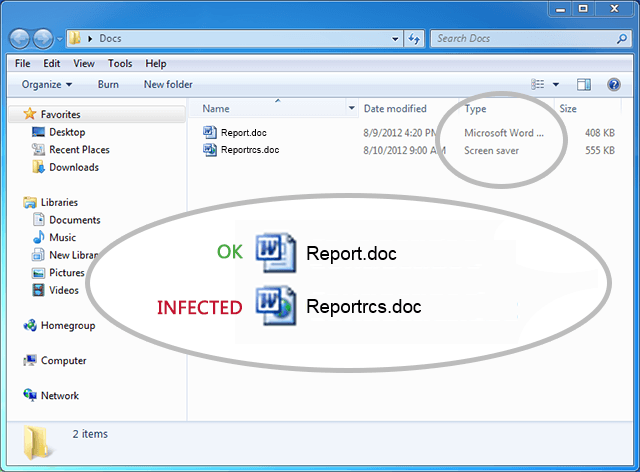
To check what type it really is, switch to Details view
In addition to using the leaked Adobe Flash 0day to target specific systems, less targeted methods – including malicious web sites (e.g. “tisone360.com”) – are being used to spread the attack. Like the Hacking Team 0-day, it looks as though the “tisone360.com” site was also delivering a Flash CVE-2014-0497 exploit. Detailed attack information is available here.
Kaspersky Lab technologies to fight Darkhotel successfully
A full list of measures available to mitigate targeted attacks can be found here. Kaspersky Lab supports the majority of these measures and recommends implementing as many of them as possible. We detect new Darkhotel downloaders and infostealers with the verdict “Trojan.Win32.Darkhotel.*”, spearphishing attachments are detected as “Trojan-Dropper.Win32.Dapato.*” and “Trojan-Downloader.Win32.Agent.*”
0-day prevention
Darkhotel’s lightly obfuscated .hta files, used for initial penetration, are detected using emulation with the “HEUR:Trojan.Script.Iframer” verdict. Heuristic algorithms exist for previously unknown malware samples that cannot be detected using databases. Such algorithms are based on the knowledge of both structure and emulated behavior typical patterns.
Kaspersky Lab’s Automatic Exploit Prevention functionality is designed to fight exploits, including 0-days, and is highly effective at detecting Darkhotel components. Heuristics and Automatic Exploit Prevention in Kaspersky Lab’s advanced antimalware engine is a crucial part of a multilayered, comprehensive defense.
Apply patches in time
Regularly updating to the latest version of installed software and patching OS will help prevent a vast range of attacks. Timely patching is most easily achieved using a Patch Management toolkit, such as Kaspersky Lab’s, working together with or instead of Microsoft WSUS. Vulnerability Assessment and Patch Management[1] combined will also update all popular third-party software to the latest versions.
Stolen certificates
Like other current Advanced Threat groups, Darkhotel uses stolen certificates to give their modules the appearance of trusted apps. Trust in files is based on their reputation and digital signatures play a big role in gauging reputation. But a digital signature by itself is not enough to create trust. Kaspersky Lab products detect digitally signed malware.
Compromised Wi-Fi network start pages
The most interesting initial penetration technique in the Darkhotel campaign is its infection of hotels’ startup web pages. Targets, including high-level managers, are infected immediately after authentication with luxury hotel local WiFi networks. This attack vector could be successfully mitigated by enabling Web Anti-Virus in Kaspersky Endpoint Security policy.
Control servers known URLs
When command and control (CnC) servers of any targeted attack are determined we add their addresses into our security database. Kaspersky Lab clients can obtain all the current information about active CnC servers from our special data feed. This feed could be used (e.g. in customer’s SIEM system) to alert system administrators of any communications with these malicious servers.
Malicious e-mail attachments
Despite all the new ingenious ways to infect hosts, spear-phishing with disguised malicious attachments is still by far the most popular method for malefactors. All Kaspersky Endpoint Security for Business product installations protect hosts from this malware propagation technique. Organizations can also deploy Kaspersky Security for Linux Mail Server or Kaspersky Security for MS Exchange centrally to secure business e-mail traffic on the server side.
[1] Vulnerability Assessment and Patch Management are included in Kaspersky Total Security for Business, Kaspersky Endpoint Security for Business Advanced and Kaspersky Systems Management.
 APT
APT
