In terms of daily workload, few infosec roles compare with that of a security operations center (SOC) analyst. We know this firsthand, which is why we pay special attention to developing tools that can automate or facilitate their work. Following our recent upgrade of Kaspersky CyberTrace to a full-fledged threat intelligence (TI) platform, here we demonstrate how a SOC analyst can use this tool to study the attack kill chain.
For example, suppose someone uses a workstation on the corporate network to visit a website that is flagged as malicious. The company’s security solutions detect the incident, and the security information and event management (SIEM) system logs it. Ultimately, a SOC analyst armed with Kaspersky CyberTrace sees what’s going on.
Identifying the attack chain
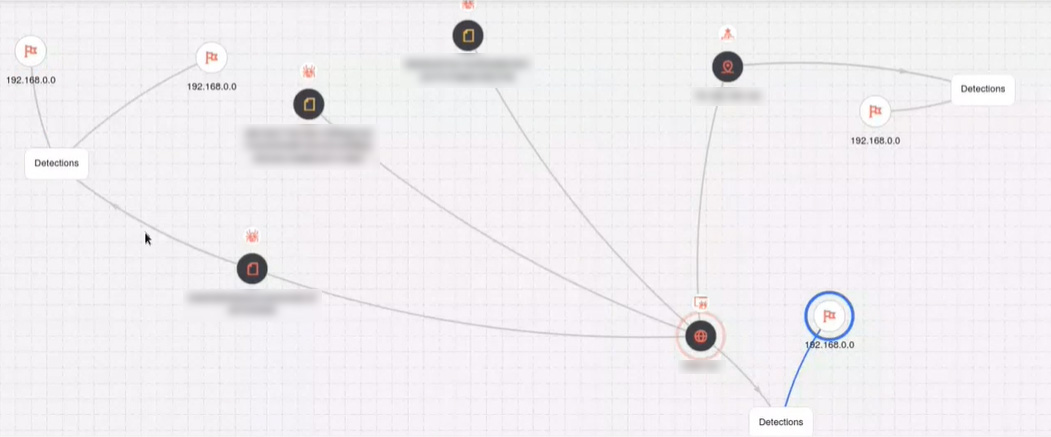
In the list of discovered anomalies, the analyst sees a detection based on data from the “Malicious URL” feed and decides to take a closer look. Contextual information (IP address, hashes of malicious files associated with the address, security solution verdicts, WHOIS data, etc.) is available to the analyst directly in the feed. However, the most convenient way to analyze the attack chain is to use a graph (the View on Graph button).
So far we have little information: the fact of detection, the detected malicious URL, the internal IP address of the computer from which the URL was opened, and the ability to view full contextual information for the detected threat in the sidebar. That’s just a prelude to the interesting part, however.
By clicking on the icon of the malicious URL, the analyst can request the known indicators associated with the address: IP addresses, additional URLs, and hashes of malicious files downloaded from the site.
The next logical step is using the indicators to check for other detections in the infrastructure. Doing so couldn’t be simpler: Click any object (for example, a malicious IP address) and select Related CyberTrace Detects. Additional detections are displayed as a graph. In just one click, we can find out which user accessed the malicious IP address (or on which machine a URL query to the DNS server returned the IP address). Similarly, we can check which users have downloaded files whose hashes are present in the indicators.
All indicators in the screenshots represent tests and constitute an example of fairly modest incidents. In the real world, however, we might see thousands of detections, sorting through which manually, without a graphical interface, would be quite difficult. With a graphical interface, however, each point of the graph pulls all context from the threat data feeds. For convenience, the analyst can group or hide objects manually or automatically. If analyst has access to some additional sources of information, he can add indicators and mark the interrelationships.
Now, the expert while studying indicator interconnections can reconstruct the full attack chain and learn that the user typed the URL of a malicious site, the DNS server returned the IP address, and a file with a known hash was downloaded from the site.
Integration with Kaspersky Threat Intelligence Portal
Matching detections to threat data feeds serves for analysis of one isolated incident, but what if the incident is part of a large-scale, ongoing, multiday attack? Getting historical background and context is critical for SOC analysts. For this purpose, the upgraded Kaspersky CyberTrace features integration with another of our analysis tools, Kaspersky Threat Intelligence Portal.
Kaspersky Threat Intelligence Portal has access to complete cyberthreat database, built by our antimalware experts since the day one of Kaspersky. Through the Related External Indicators menu, the analyst can access with one click all of the information Kaspersky have accumulated to find out which domains and zones are associated with a malicious IP address, what other URLs were previously associated with the IP, hashes of the files that have attempted to gain access to the URL, hashes of files downloaded from that URL, which URLs sites hosted at this IP have linked to (and from which URLs it has been linked), and more.
Another advantage of this integration is the ability to search for reports on APT attacks associated with a specific URL or file hash. Kaspersky Threat Intelligence Portal subscribers can readily find and download reports that mention such URLs or file hashes.
None of this information was unavailable before, but getting it required manual work — finding the right hash or address, copying it, navigating to the portal. New quick and easy access to all of this information enables infosec to take appropriate timely countermeasures on attack detection, and it also simplifies incident investigation.
What else can Kaspersky CyberTrace do?
Kaspersky CyberTrace not only works with threat data feeds from Kaspersky, but it can also connect with third-party sources. What’s more, it has a convenient tool for comparing information in different feeds: the Supplier Intersections matrix. The matrix enables analysts to see which feeds have more data — and if one feed has no unique data, the analyst can unsubscribe.
CyberTrace also supports teamwork in multiuser mode: The analyst can give colleagues access to comment on or contribute to the investigation.
If necessary, analysts can unload indicators from CyberTrace, making them accessible via the URL. Such an action may be needed to, for example, add a rule for automatic blocking of indicators at the firewall level.
Another useful feature is Retroscan, which analysts can use to save old logs from SIEM systems and check them later against new feeds. In other words, if analysts had insufficient data for a proper investigation at the time of incident detection, they can still carry one out retrospectively.
See our CyberTrace page for more information.
 threat intelligence
threat intelligence



 Tips
Tips