
Talk Security Podcast: Dark Hotel and WireLurker
In this episode of the Talk Security podcast, Threatpost’s Chris Brook and Brian Donohue discuss the Dark Hotel cyberespionage campaign and the WireLurker Apple malware.
369 articles

In this episode of the Talk Security podcast, Threatpost’s Chris Brook and Brian Donohue discuss the Dark Hotel cyberespionage campaign and the WireLurker Apple malware.

Drupal warns customers that they should assume their sites are compromised unless they installed an update from mid-October within hours of the release.

Brian Donohue and Dennis Fisher talk about a new attack on the SSL protocol, which is now known as POODLE.

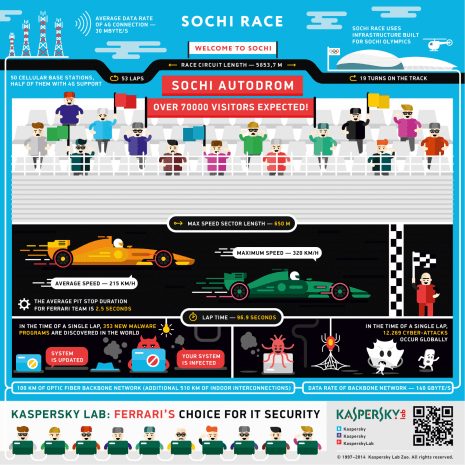
Almost three dozen computers are required by Ferrari engineers to analyze everything happening with a racecar and decide on the maintenance. However, there are other computers in the paddock, very unusual ones.

What changed in Sochi since Olympic games? Does infrastructure suit Grand Prix? Let’s find out together.

September’s security news was dominated by three stories: the Home Depot data breach, the Apple celebrity nude photo leak scandal and the Shellshock vulnerability in Bash.

Elena Kharchenko, Head of Consumer Product Management, answers the important security questions that you submitted.

Tor is an online browsing portal that keeps your web activity completely anonymous.

The Apple iCloud nude celebrity photo fiasco underscores the uncomfortable reality that even the savvy among us aren’t totally sure about what goes on and into “the Cloud.”

Is it even worth applying for popular jobs? The answer is “Yes, absolutely” – as long as you keep in mind a few important points that will help you stand out from the crowd.

Brian Donohue and Chris Brook recap the month’s security headlines from its beginnings at Black Hat and DEFCON, to a bizarre PlayStation Network outage.

In this short video, we will explain six steps you can take to conveniently maximize the security of your PayPal account.

Many recruiters will compare finding the right candidate to finding their mate. It is especially relevant for Kaspersky as we need very special people with unique skills.

Participate in Kaspersky Lab’s Global Think Test to test your brain power.

In the news: Microsoft’s No-IP takedown fiasco, Chinese APT groups curious about U.S. Iraq policy, Verizon says the government wants locations data, and Microsoft denies backdoor insinuations.
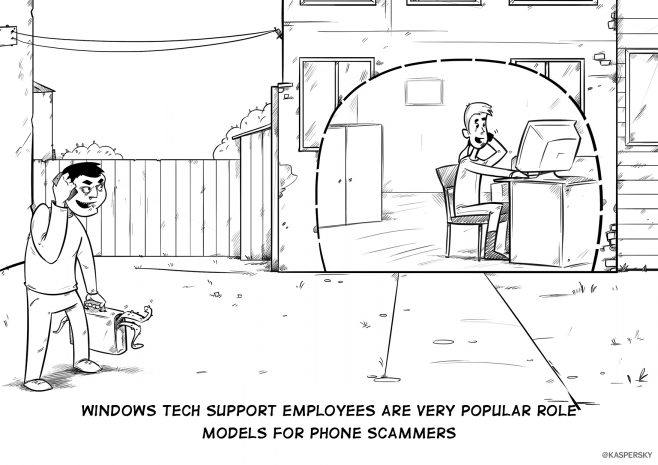
The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS

The next page of The Сyberworld Survival Guide. The entire guide can be found here: http://www.kaspersky.co.za/blog/tag/securityIS