
Busted! Top prosecutions of August
The final month of summer wasn’t full of cybercriminal stories, but law enforcement groups around the world still found and punished some evildoers.
1441 articles

The final month of summer wasn’t full of cybercriminal stories, but law enforcement groups around the world still found and punished some evildoers.

Tor is an online browsing portal that keeps your web activity completely anonymous.
A survey reveals the motivations behind hacker attacks, showing that they are not afraid of consequences.

On September 9th, Apple showed some new devices and its own payment system, which utilizes an NFC chip, Touch ID sensor and Passbook app. So we had a try to find out how it works, what it gives us and how well this system is protected.

KL and Mensa have announced the first champion of the Global Think Test challenge.

The Apple iCloud nude celebrity photo fiasco underscores the uncomfortable reality that even the savvy among us aren’t totally sure about what goes on and into “the Cloud.”

Your data is the finest treasure on your computer. Protect it the way the secret service protects a president, create a robust defense system where an antivirus will be just the last line of defense.
Don’t want your private photos or credit card posted somewhere on the web? You should rethink your approach to cloud services then.

Brian Donohue and Chris Brook recap the month’s security headlines from its beginnings at Black Hat and DEFCON, to a bizarre PlayStation Network outage.

Beware of phishing, malware, spam and other online scams based on the extremely popular ALS Ice Bucket Challenge.

It would be nice to think that it would take a lot more than an overeager amateur hacker like Seth Green’s character from the 2003 movie “The Italian Job,” to bring traffic to a screeching halt.

Preparing to watch your child trundle off to school with these expensive devices in their backpacks will be a lot easier if you guard against the many perils that can threaten them – theft, malware and unwanted Internet browsing chief among them.
Community Health Systems breach exposes the Social Security numbers of 4.5 million patients. Were you a victim? If so, how do you react?

We have bought our very own Blackphone to check its security firsthand.

A recap of last week’s security news and research from the Black Hat hacker conference in Las Vegas, Nevada.
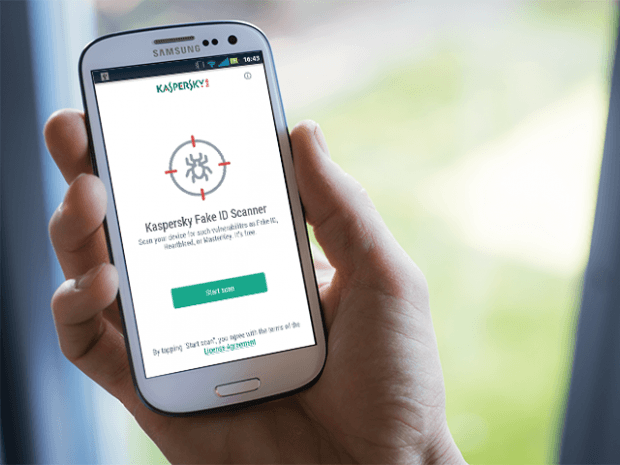
Unpatched flaws in Android make your device vulnerable to “Invisible” infection. You better find out now in order to protect yourself.

Some things we routinely do in the office are dangerous for careers as they pose significant risk to the company’s business. It’s equally relevant for CEO and intern alike, so watch out!

Yahoo plans to implement end-to-end encryption for all of its mail users, giving normal, non-technical users the power to communicate securely and privately.
Car hacking is back and Charlie Miller and Chris Valasek no longer have to plug their computers into the cars to make them do their bidding.