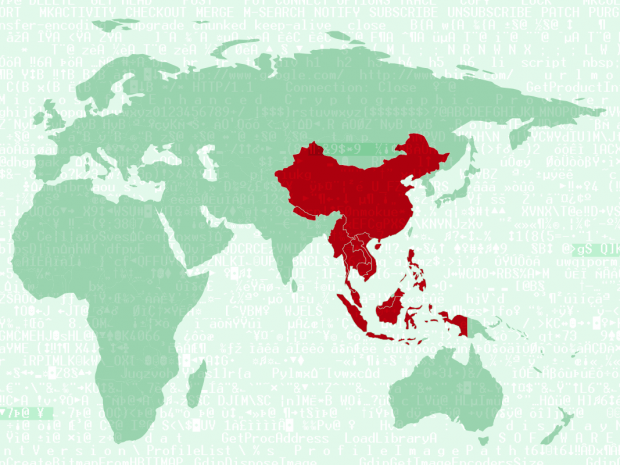
Naikon APT steals geopolitical data from the South China Sea
A new, Chinese-language APT has emerged, seeking geopolitical information and targeting nations in and around the South China Sea
1441 articles

A new, Chinese-language APT has emerged, seeking geopolitical information and targeting nations in and around the South China Sea

When you look at airplanes moving on a map, you get the feeling it’s sheer Brownian motion. Of course, that’s not the case: aircrafts keep to air tracks all the time.

Using a biochip, Microsoft Kinect, a servo, and a bit of IT magic, we are going to make the imaginary idea of Jedi Force come to life in the real world!

Our personal implementation of the cloud security model is called Kaspersky Security Network. And here we’ll explain how it actually works.

How many research centers do you need to fight for a safer cyber world? We used to have three labs based in Moscow, Beijing, and Seattle. Now, we’re excited to announce the opening of a fourth lab — our new European Research Center based in London.

It was recently discovered that certain Hospira drug infusion pumps contain dangerous and easily exploitable security vulnerabilities.

A legendary Soviet spy, Richard Sorge, is famous for conveying the exact date of the German invasion into the Soviet Union, and for letting the command know Japan had no plans of attacking the USSR in the Far East.

Five lessons from the story of the Enigma cryptographic machine which are still relevant.

During WW2 modern cryptography principles were often coupled with ‘amateur’ ciphering methods. Curiously, the latter ones often proved to be equally reliable

Let’s imagine the things we would have to leave behind as a brand new world of driverless cars is evolving at a full speed (besides the enjoyment of driving itself)

New research demonstrates that it is possible to hack and hijack devices used to perform remote surgery

Technologies which seemed like they were from science fiction yesterday, are entering our everyday lives. One such tech is direct neural interfaces.

Yet another APT of the ‘Dukes family’ is hitting high-profile targets, including the US government office.

The story of how Israeli UAVs defend the country on the ground, in the sky, and in the information domain.

The annual RSA Conference in San Francisco, California of Internet-of-things insecurity and how no amount of money can fix computer security

Recent report by US GAO was treated by medias as “Modern aircrafts can be hacked and commandeered through onboard Wi-Fi”. Is it really that bad?

Everybody knows about flying drones, but there are also swimming and diving drones that patrol ports and ships, demine shores and so on. Let’s take a closer look at maritime robots.

Big data helps to catch child abusers, drug dealers, and terrorists, and allegedly it also helped to locate Bin Laden.

Flightradar24 allows you to track what’s happening to any particular aircraft taking a family member or friend to their destination. Let’s find out how this service works.

Kaspersky Lab and the Dutch cyber-police created a tool that restores files encrypted by CoinVault ransomware.

Recently Interpol, Microsoft and Kaspersky Lab revealed and the shut down of a huge botnet which zombified about 770,000 PCs worldwide. Check this story out and then check your PC