Device control, application control and dynamic whitelisting
What kind of corporate network would be considered secure? Primarily one that is controlled by its operators, or in other words, a network in which the system administrator knows where,
1246 articles
What kind of corporate network would be considered secure? Primarily one that is controlled by its operators, or in other words, a network in which the system administrator knows where,
Although we usually talk about the ways to protect information from threats, today we are going to list several proven and popular ways to lose data and, possibly, even money.

Black Tuesday August the 13th brought numerous challenges to (primarily) corporate users of Microsoft products. The company released patches for critical vulnerabilities in Windows, Exchange Server and Active Directories. As

88% of tablet users and 96% of smartphone owners use personal devices to store important personal information. These figures are from the survey B2B International and Kaspersky Lab cooperatively conducted
The middle of August was marked by several reports of Facebook security issues, all of them quite scandalous. Even though they didn’t cause any catastrophic consequences for the users, they
Today’s malware is definitely not the only security threat for individual and corporate users, but the tools of detecting and fighting malware remain fundamental in any security solution. There are
In IDC’s latest “Worldwide Endpoint Security 2013-2017 Forecast and 2012 Vendor Shares”* report, Kaspersky Lab has been positioned as the third largest Endpoint Security Suite Vendor with a 13% share
Within a few days in the middle of August, reports of massive cyber attacks against the U.S. media surfaced, more specifically, at the Washington Post, CNN and Time, as well
Apple Developer Center down for a week It took Apple about a week to restore the functions of the Apple Developer Center following its crash on July 18. After about

The number of IT security incidents involving smartphones and tablets is on the rise, and most companies have no plans to limit the use of personal mobile devices for work-related

Kaspersky Lab today announces the opening of a new flagship European office in central London. Serving as an official ‘hub’ for European employees and customers, the new office will position
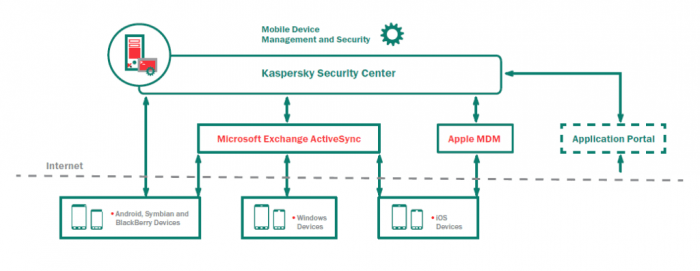
Work does not always require an employee’s presence in the office. In many cases it is acceptable, convenient, and sometimes advantageous for the employee to work remotely from a mobile
MDM systems are often not necessary right away for companies with a small number of mobile workers, whose managers often believe their IT-department can handle it effortlessly. But a reality

A modern man cannot imagine his life without mobile devices like smartphones and tablet computers. A portable minicomputer that provides access to the Internet and offers basic features for processing
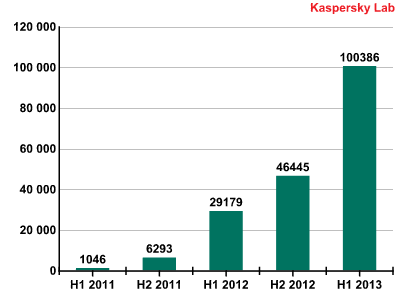
Kaspersky Lab has published its report on the evolution of threats in the second quarter of 2013. This period has been marked with a number of security incidents of different
Using leased infrastructure for storing large amounts of data has been typical for several years. Leased capacities provide an advantage by allowing businesses to greatly reduce the cost of tending
Part two. The first part is available here. Risks associated with the vulnerabilities Bluebox reported that the vulnerabilities could be used to attain root rights in the system providing

The second half of July roused Android users as two very serious and unpleasant vulnerabilities were discovered. Researchers announced these so-called “master keys,” i.e. universal access to any Android device,
On July 31st at the Black Hat conference in Las Vegas, Security Research Lab’s (SRL) Karsten Nohl presented research on the SIM security flaw. Nohl experimentally demonstrated the vulnerability, which

Today the news of the hacking of resources at a major IT company does not really come as a surprise to anyone. Unfortunately, attacks like this now happen more often
Myths and prejudices are inevitable companions to any branch of knowledge, and the information security sphere is no exception, no matter how practical it is. This article will briefly touch