
Dennis Technology Labs awarded top ratings to our solutions
We’re pleased to announce another three accolades from an independent test lab. Dennis Technology Labs awarded our home and business products with AAA rating.
1246 articles

We’re pleased to announce another three accolades from an independent test lab. Dennis Technology Labs awarded our home and business products with AAA rating.

Apple has announced new versions of its operating system. OS X and iOS become closer, gradually merging into a single environment. How well is it protected?

May 2014 appears to be very stormy and volatile in regards to information security. Still overshadowed by Heartbleed and Windows XP “official demise” from April, it has brought a lot of troubles on its own.
Something very weird is going on with the popular free whole-disk encryption suite TrueCrypt. The story is still developing, but it does look like the suite ceases to exist right

Kaspersky Lab has launched new a Cyberstat portal, which shows how vast the present day cyberworld is and how quickly it expands.
In recent years, payment and banking services have been drawing closer attention of all sorts of criminals. The number of crimes related to stealing money via electronic communications keeps growing.

Earlier this month, I have spent a week in Protaras, a very nice resort town located at the Eastern part of Cyprus. It’s a brilliant place for a getaway especially

New facts and figures on our partnership with Ferrari.

The season seems to be open: The dust hasn’t yet settled after the Heartbleed semi-apocalyptic revelation, and now eBay has confirmed that its security had been badly breached, with service

The famous indendent lab AV-Test has just completed another round of its comparative tests of security solutions – this time the ones intended for use within the virtual environments. Three

Last week, Kaspersky Lab hosted a webinar to discuss the threat landscape in the era of targeted attacks. Here’s a summary and slides from this event.
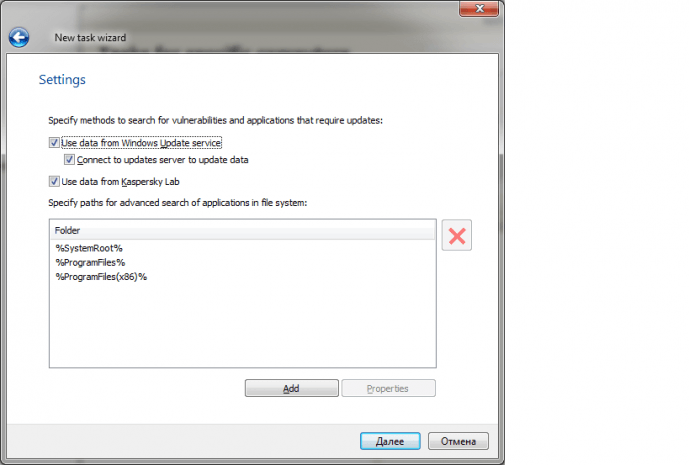
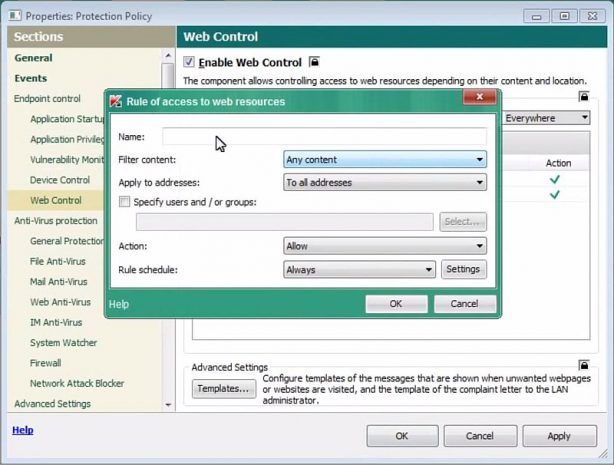
We continue our overview of the Kaspersky Security Center functionality and Software Assistant technologies in particular.
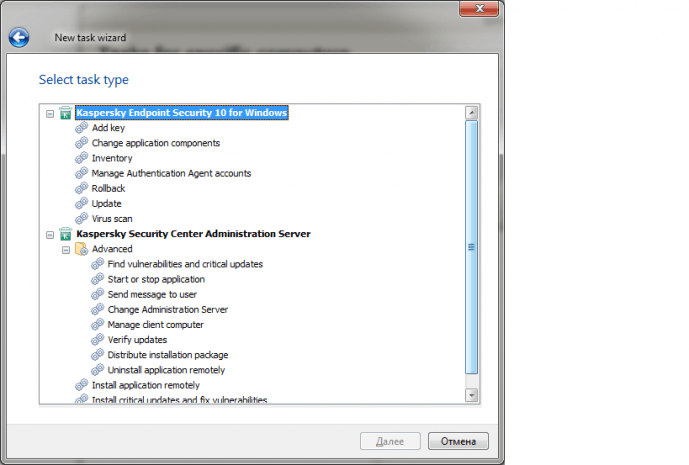
IT workers sometimes have to manage several dozen or even several hundred PCs at once, which makes an automated management solution absolutely necessary. Kaspersky Security Center’s Software Assistant makes accomplishing routine IT tasks extremely easy.
Habits are easy to form and hard to break in all facets of life, including technology usage. Sometimes a user’s habits may not seem so harmful, at least from their

So, you may have heard that antivirus has been pronounced dead – again. It has happened before and, no doubt, will happen again. Usually, such “big” announcements are used when

Microsoft had to deal with a new less-than-pleasant vulnerability in Internet Explorer browser, which affected all of its versions starting with IE6 in all of its operational systems including the

Aside from protecting virtual environments without straining servers, Kaspersky Security for Virtualization offers a number of advantages to admins. For instance, there is no need to reboot or put servers into maintenance mode to deploy our solution.

Traditional ‘agent-based’ solutions should not be used in virtual environments, especially those in dynamic use. Instant-On Gaps are the most common problem here: it strains servers and creates a serious vulnerability window for a VM. Kaspersky Security for Virtualization has been designed specifically to eliminate this problem.

April 2014 was destined to be the month ‘when Windows XP’ died, but this didn’t happen. The ‘Heartbleed’ bug outshone everything else. Still, there were incidents (unrelated to Heartbleed) worth mentioning.

Banks require new tools to prevent fraudsters from getting to others’ money and Kaspersky Lab’s new Fraud Prevention platform is just the tool to use.

The virtual environment requires the same protection as physical PCs, but the approach should be different. Full blown security solutions on every virtual machine? The strain for a physical server would be too great. But here comes ‘Light-Agent’…