
A layman’s dictionary: What is APT and why is it called that?
APT is a term often mentioned in cybersecurity bulletins. Here’s what you need to know to understand it.
1243 articles

APT is a term often mentioned in cybersecurity bulletins. Here’s what you need to know to understand it.

IT workers routinely set up limited privileges for all users for security sake. However, the users are extremely suspicious about these sorts of limitations, assuming (sometimes reasonably) that it will affect the workflow. Is there a way to mitigate these contradictions?

Interpol just released an alert regarding cyber-attacks targeting multiple ATMs around the world. During the course of a forensic investigation performed by Kaspersky Lab, researchers discovered a piece of malware infecting ATMs that allowed attackers to empty the cash machines via direct manipulation, stealing millions of dollars.

2014 is making its way into Cybersecurity history books with two global-scale software bugs discovered over 6 months. They are obviously not the last ones, and it is actually a good thing.

Kaspersky Lab launches its solution Kaspersky DDoS Protection in Europe. A distributed network of data cleaning centers vs. distributed attacks.

Kaspersky Lab has signed a cooperation agreement with INTERPOL and a memorandum of understanding with Europol to extend the scope of collaboration between the company and the law enforcement agencies in their joint fight against cybercrime.

We’ve gathered information for patching the most common Linux distros against the notorious Shellshock Bash Bug. If you see we’ve missed something, please drop us a tip!

It’s been a day since the BashBug aka Shellshock bug was disclosed. What real damage has been inflicted and who is most in danger?

A new nasty bug discovered in Bourne again shell set the infosec on fire, Heartbleed-style. Is it as dangerous as the notorious OpenSSL flaw? It depends…

Critical infrastructure operators are often reluctant to deploy full-scale anti-malware protection. They are worried about compatibility, performance, compliance, and the most important thing: possible downtime. But our research shows that malware is the true enemy.

Brian Donohue interviews Adam Firestone, President and General Manager of Kaspersky Government Security Solutions, about why critical infrastructure systems are insecure, and why added on security does not work.

iOS-based devices have a large share in the enterprise, which assures a strong demand for BYOD-oriented security features. A number of them arrive in iOS 8.
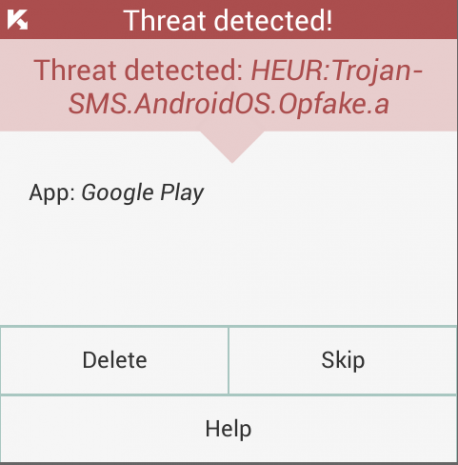
This post is comprised of two topics: a Trojan Opfake.a, which made a lot of buzz earlier this months and analyzing mobile malware at home. The latter is quite possible, but requires protective measures.

Cyber-resilience is the ability to sustain damage, but ultimately succeed. In order to be resilient, businesses need to have a plan. One organization is dealing with attacks today that another will deal with tomorrow. There are ways businesses can help each other become cyber-resilient.

The healthcare and financial services industries are among those especially reluctant to implement newer technologies, security included, and believe they have a good reason for that.

It’s been years since we’ve last heard of any large worm epidemics. Does it really mean that malware epidemics have gone away for good?

Kaspersky Lab’s recent survey surprisingly found that e-commerce, online retailers and financial service providers are not just the biggest sources of stolen financial data, but also feel just a bit too lax about security. However, this has some severe implications.

Having your business bank account hijacked by cybercriminals could bankrupt your company, but that type of breach isn’t really what law enforcement cares about. They are concerned with only one thing: how well you protect certain information.

A curious story about a cyber-investigation of fraudulent activities, which our GERT group had recently conducted on behalf of one of the company’s clients. The attackers were quite thoughtful, but not good enough.

A large number of logins and passwords to accounts in several free email services – Mail.ru, Yandex and Gmail.com – had been leaked. Once again, passwords prove to provide insufficient protection. What does it mean for businesses?

The biggest concern about Apple Pay is that one’s iCloud account now controls not only private photos, app data, and messages, but also money. You lose your password – you lose everything and as the celebrity hack showed us, there is no need to hack Apple’s servers. Social engineering, phishing, trojans – all cybercriminal tools will now be targeted at people’s electronic wallets.