
Millions of indicators: Solving the major incident response challenge
To be successful, incident response has to be integrated with existing security solutions and should be powered by the threat detection solutions of the future.
1246 articles

To be successful, incident response has to be integrated with existing security solutions and should be powered by the threat detection solutions of the future.

New NSS Labs test utilized new methodology, however it’s results raised some serious questions

We shared our general vision of today’s threat landscape at Kaspersky Lab’s RSA booth.

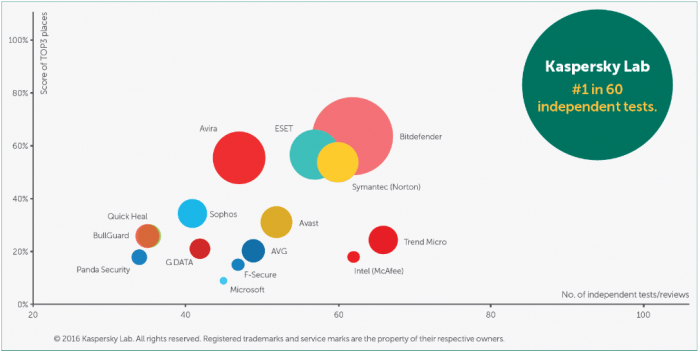
Independent testers are constantly examining security solutions. We have some tips on how to make use of their results.

When an attack combines legitimate tools with fileless malware, it’s extremely difficult to detect, so antimalware teams constantly need to improve their skills

Healthcare technologies and mobile working practices are producing more data than ever before, so there are more opportunities for data to be lost or stolen.

We at Kaspersky Lab consider the Adaptive Security Architecture the most efficient model to build up cybersecurity practices for industrial objects

As you probably know, Star Wars: Rogue One has hit the theaters to tell the story of the Rebellion who steal the plans of Death Star and facilitate its destruction.

In our previous article on this topic, we looked into the history of memory-only attacks, also taking a glance at attack scenarios and appropriate defensive technologies. Now it is time

Digital healthcare allows ever more non-security trained medical staff to access and share confidential patient data, which builds up a challenge for IT security workers.

A company’s business stalls because of a cryptor. The head of IT dept is to solve the problem. But “solving” this time doesn’t mean just “restoring the data”.

At VB2016, Juan Andrés Guerrero-Saade and Brian Bartholomew of GReAT discussed why APT attribution is not easy.

The first zero-day exploit for InPage text processor had been used in attacks on Asian banks.
Kaspersky Lab is giving MSPs a chance to get in on the ground floor of an exciting new integration of security and remote monitoring and management tools.

Sometimes ATM operators make criminals’ jobs easier by leaving banking machines’ network equipment accessible.

Analysis shows that the attackers are particularly active during the holiday period.

Kaspersky Lab will be showcasing and offering beta version of Kaspersky Security integration with ConnectWise.
Forrester Research interviewed vendors and customers to evaluate top endpoint security providers.

Who is responsible when connected devices go on a crime spree?

Yet another example of an attack against an ATM: This time the cash machine itself is emulated.
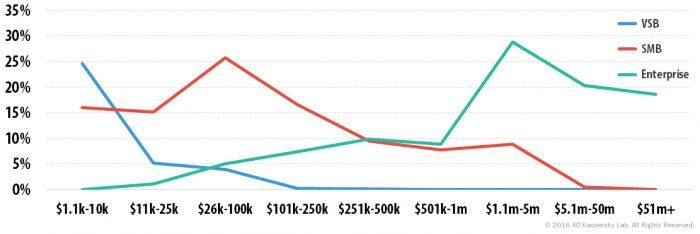
For many SMBs SaaS can provide a cost effective way to take advantage of technology through a cloud-based, subscription model.