
Cybersecurity in season 2 of The Mandalorian
The Galactic Empire’s heirs analyzed for cybersecurity.
1244 articles

The Galactic Empire’s heirs analyzed for cybersecurity.

In the face of high-profile ransomware attacks on healthcare institutions, here’s how to protect your business from the threat.


The most active groups targeting companies, encrypting data, and demanding ransom.

If an incoming message asks you to sign in to your MS Office account, here’s what to do.

With a website that looks like it could represent an online service provider, DarkSide Leaks makes us wonder what cybercriminals’ other PR tricks might be.

A zero-day vulnerability in Microsoft Windows may already have been exploited.


Ransomware operators sometimes resort to rather unconventional threats to get their victims to pay.

Unknown attackers tried to add a backdoor to PHP scripting language source code.

Several cybercriminal groups have exploited vulnerabilities in VMware ESXi to infect computers with ransomware.

To stop all threats to the corporate infrastructure, you have to do more than just protect workstations.

A vulnerability in Google Chrome has already been exploited by malefactors. All users need to update to version 89.0.4389.90.

Vietnam started a coordinated anticybercrime campaign at the government level in 2020. The results are amazing.

Attackers exploit four dangerous vulnerabilities in Microsoft Exchange to get a foothold in the corporate network.

Three reasons not to pay cyber-extortionists — and what to do if you get hit.

Would Johnny Mnemonic’s cybersecurity be plausible in the real 2021?
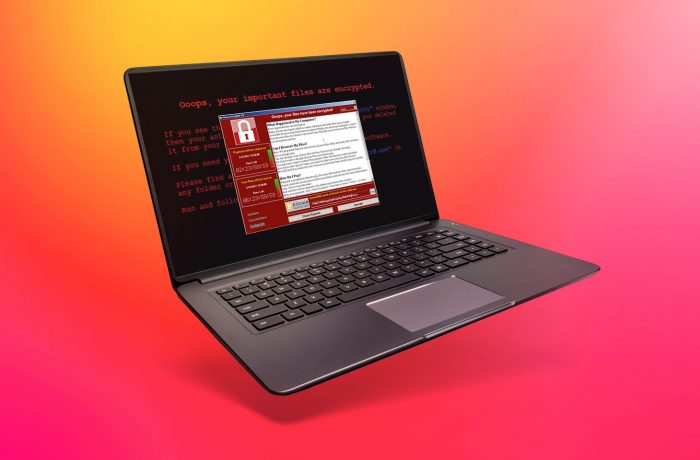


CD Projekt confirms attack on internal systems. Hackers claim to have downloaded Cyberpunk 2077 and The Witcher 3 source code, and demand ransom.