The post is being updated as our experts find new details on the malware.
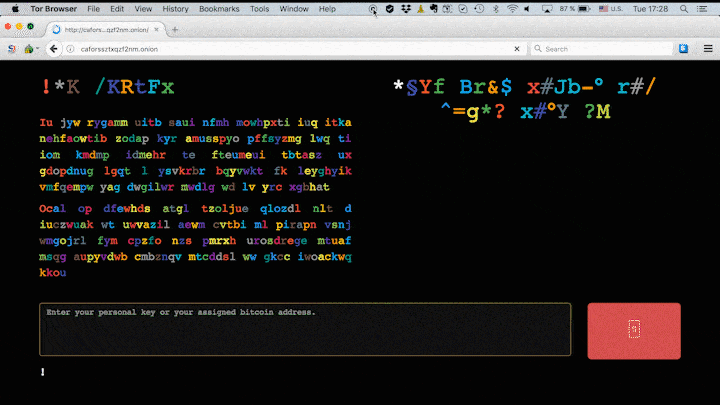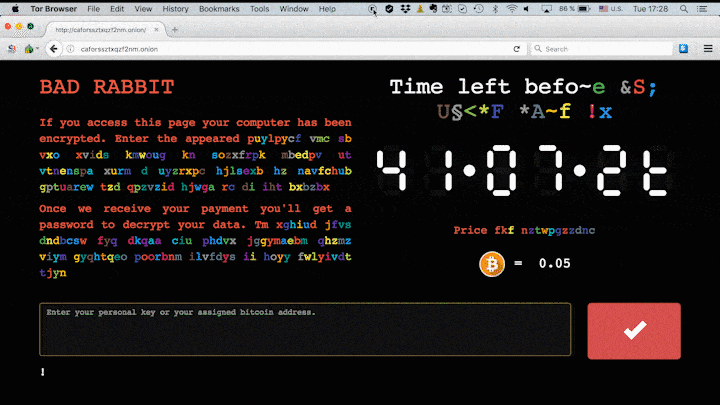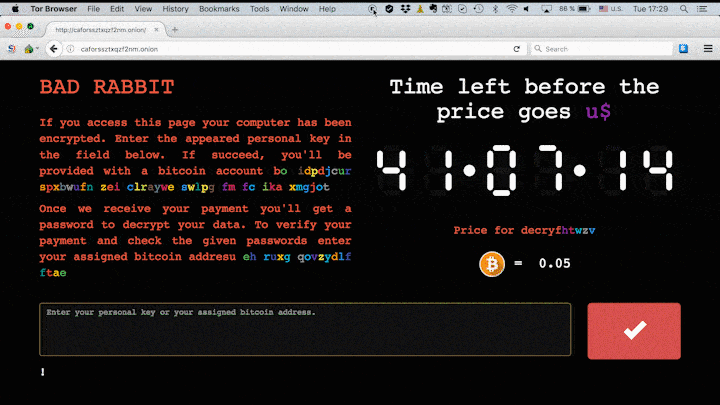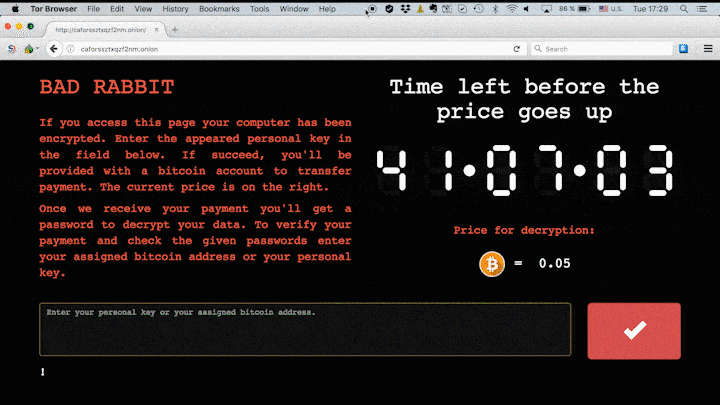
We’ve already seen two large-scale ransomware attacks this year — we’re talking about the infamous WannaCry and ExPetr (also known as Petya and NotPetya). It seems that a third attack is on the rise: The new malware is called Bad Rabbit — at least, that’s the name indicated by the darknet website linked in the ransom note.
What is known at the moment is that Bad Rabbit ransomware has infected several big Russian media outlets, with Interfax news agency and Fontanka.ru among the confirmed victims of the malware. Odessa International Airport has reported on a cyberattack on its information system, though whether it’s the same attack is not yet clear.
The criminals behind the Bad Rabbit attack are demanding 0.05 bitcoin as ransom — that’s roughly $280 at the current exchange rate.
According to our findings, it is a drive-by attack: Victims download a fake Adobe Flash installer from infected websites and manually launch the .exe file, thus infecting themselves. Our researchers have detected a number of compromised websites, all news or media sites.
According to our data, most of the victims of these attacks are located in Russia. We have also seen similar but fewer attacks in Ukraine, Turkey, and Germany. This ransomware has infected devices through a number of hacked Russian media websites. Based on our investigation, this is a targeted attack against corporate networks, using methods similar to those used in the ExPetr attack.
Our experts have collected enough evidence to link the Bad Rabbit attack with the ExPetr attack, which happened in June of this year. According to their analysis, some of the code used in Bad Rabbit was previously spotted in ExPetr.
Other similarities include the same list of domains used for the drive-by attack (some of those domains were hacked back in June but not used) as well as the same techniques used for spreading the malware throughout corporate networks — both attacks used Windows Management Instrumentation Command-line (WMIC) for that purpose. However, there is a difference: Unlike ExPetr, Bad Rabbit doesn’t use the EternalBlue exploit for the infection. But it uses the EternalRomance exploit to move laterally on the local network.
Our experts think the same threat actor is behind both attacks and that this threat actor was preparing the Bad Rabbit attack by July 2017, or even earlier. However, unlike ExPetr, Bad Rabbit seems to be not a wiper, but just ransomware: It encrypts files of some types and installs a modified bootloader, thus preventing the PC from booting normally. Because it is not a wiper, the malefactors behind it potentially have the ability to decrypt the password, which, in turn, is needed to decrypt files and allow the computer to boot the operating system.
Unfortunately, our experts say that there is no way to get the encrypted files back without knowing the encryption key. However, if for some reason Bad Rabbit didn’t encrypt the whole disk, it is possible to retrieve the files from the shadow copies (if the shadow copies were enabled prior to the infection). We continue our investigation. In the meantime, you can find more technical details in this post on Securelist.
Kaspersky Lab’s products detect the attack with the following verdicts:
- Trojan-Ransom.Win32.Gen.ftl
- Trojan-Ransom.Win32.BadRabbit
- DangerousObject.Multi.Generic
- PDM:Trojan.Win32.Generic
- Intrusion.Win.CVE-2017-0147.sa.leak
To avoid becoming a victim of Bad Rabbit:
Users of Kaspersky Lab products:
- Make sure you have System Watcher and Kaspersky Security Network running. If not, it’s essential to turn these features on.
Other users:
- Block the execution of files c:windowsinfpub.dat and c:Windowscscc.dat.
- Disable WMI service (if it’s possible in your environment) to prevent the malware from spreading over your network.
Tips for everyone:
- Back up your data.
- Don’t pay the ransom.
 Ransomware
Ransomware

 Tips
Tips